I will show you why this rarely leads to good outfits. 🧵

I will show you why this rarely leads to good outfits. 🧵



This is a real issue I solved in Windows, the hurdles I faced, and what I'd do differently.
🐥🐥YOU CAN MUTE JUST THIS CONVERSATION THREAD🐥🐥
It starts with the user editing "HKLM\HARDWARE" and misunderstanding an instruction and breaking Windows.
This is a real issue I solved in Windows, the hurdles I faced, and what I'd do differently.
🐥🐥YOU CAN MUTE JUST THIS CONVERSATION THREAD🐥🐥
It starts with the user editing "HKLM\HARDWARE" and misunderstanding an instruction and breaking Windows.
“We’re trusting that what they’re doing isn’t malicious, but we really can’t tell,” said one escort.

“We’re trusting that what they’re doing isn’t malicious, but we really can’t tell,” said one escort.
Bro, your last infra project was making a cron job email you weather updates.
Sit down.
www.duckbillgroup.com/blog/figmas-...

Bro, your last infra project was making a cron job email you weather updates.
Sit down.
www.duckbillgroup.com/blog/figmas-...
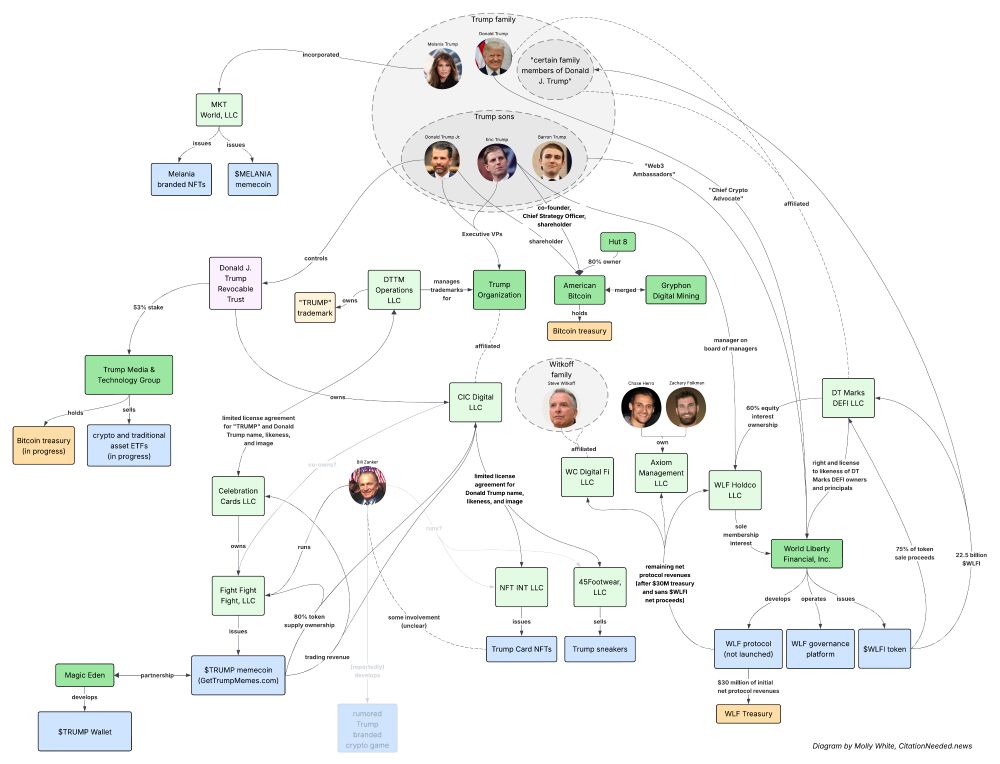
storage.courtlistener.com/recap/gov.us...
storage.courtlistener.com/recap/gov.us...
Signal Desktop on Windows now includes support for a new "Screen security" feature designed to block screenshots of your Signal chats.
signal.org/blog/signal-...
Signal Desktop on Windows now includes support for a new "Screen security" feature designed to block screenshots of your Signal chats.
signal.org/blog/signal-...
www.gomomento.com/blog/valkey-...

www.gomomento.com/blog/valkey-...
blog.torproject.org/introducing-...

blog.torproject.org/introducing-...
How to Get Fired With Both Grace and Aplomb
How to Get Fired With Both Grace and Aplomb
As one example issue, let's suppose one of your employees has "kitty videos" in their OneDrive. Now you'll have an archive of "kitty videos" on your enterprise network too!
www.techzine.eu/news/securit...

As one example issue, let's suppose one of your employees has "kitty videos" in their OneDrive. Now you'll have an archive of "kitty videos" on your enterprise network too!
Still FIPS-compliant, and with a proof.
Key commitment ensures the ciphertext can only be decrypted with one key, to avoid issues in higher-level protocols.
https://eprint.iacr.org/2025/758.pdf
Still FIPS-compliant, and with a proof.
Key commitment ensures the ciphertext can only be decrypted with one key, to avoid issues in higher-level protocols.
https://eprint.iacr.org/2025/758.pdf
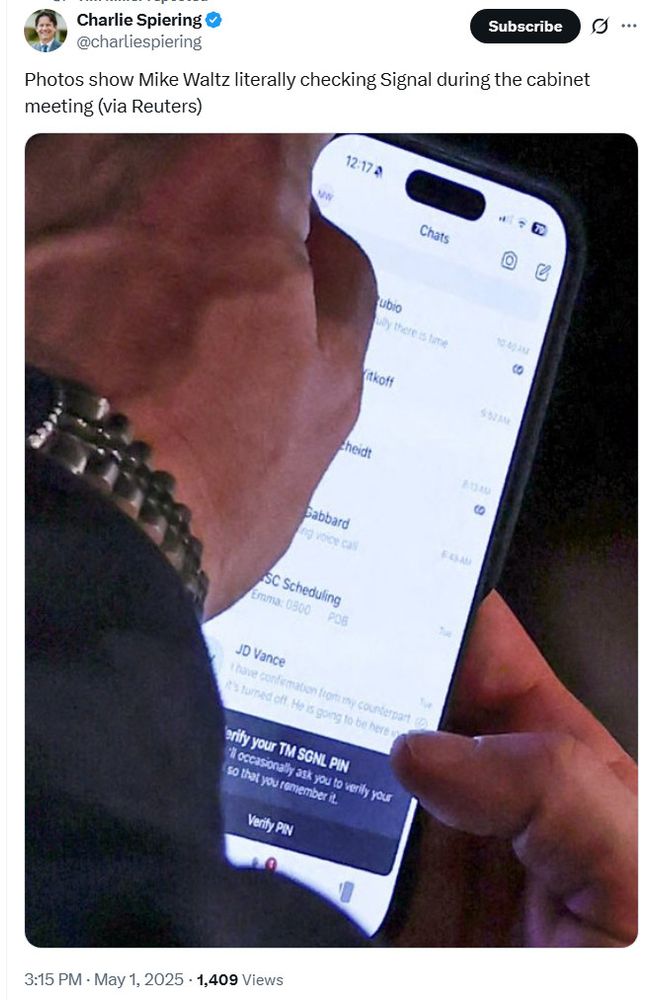
Wired: Israeli intelligence standing up a front company and tricking the White House into paying for the privilege of revealing their communications

Wired: Israeli intelligence standing up a front company and tricking the White House into paying for the privilege of revealing their communications