Needing to re-organise. So, splitting personas....
Stay here for professional(ish) InfoSec releases. For personal stuff and uneducated hot-takes, come find me @andrew.waitesworld.co.uk
Needing to re-organise. So, splitting personas....
Stay here for professional(ish) InfoSec releases. For personal stuff and uneducated hot-takes, come find me @andrew.waitesworld.co.uk
I've been building Atuin Desktop. Local-first, CRDT-powered, executable runbooks - with integrated terminals, sql queries + monitoring
blog.atuin.sh/atuin-deskto...
Lmk if you have any questions <3
If they weren’t successfully achieving the goals of Threat Actors, TAs would move on. whilst they achieve the aim, why reinvent the wheel?
isc.sans.edu/diary/31880

If they weren’t successfully achieving the goals of Threat Actors, TAs would move on. whilst they achieve the aim, why reinvent the wheel?
isc.sans.edu/diary/31880
Tickets acquired - see you there
21st June is this year's date
cfp still open for a few more days too...
www.eventbrite.co.uk/e/bsides-lee...

Tickets acquired - see you there
-Fortinet firewall and VPN exploit scripts
-A PHP-based webshell
-Network reconnaissance scripts
hunt.io/blog/keyplug...

-Fortinet firewall and VPN exploit scripts
-A PHP-based webshell
-Network reconnaissance scripts
hunt.io/blog/keyplug...
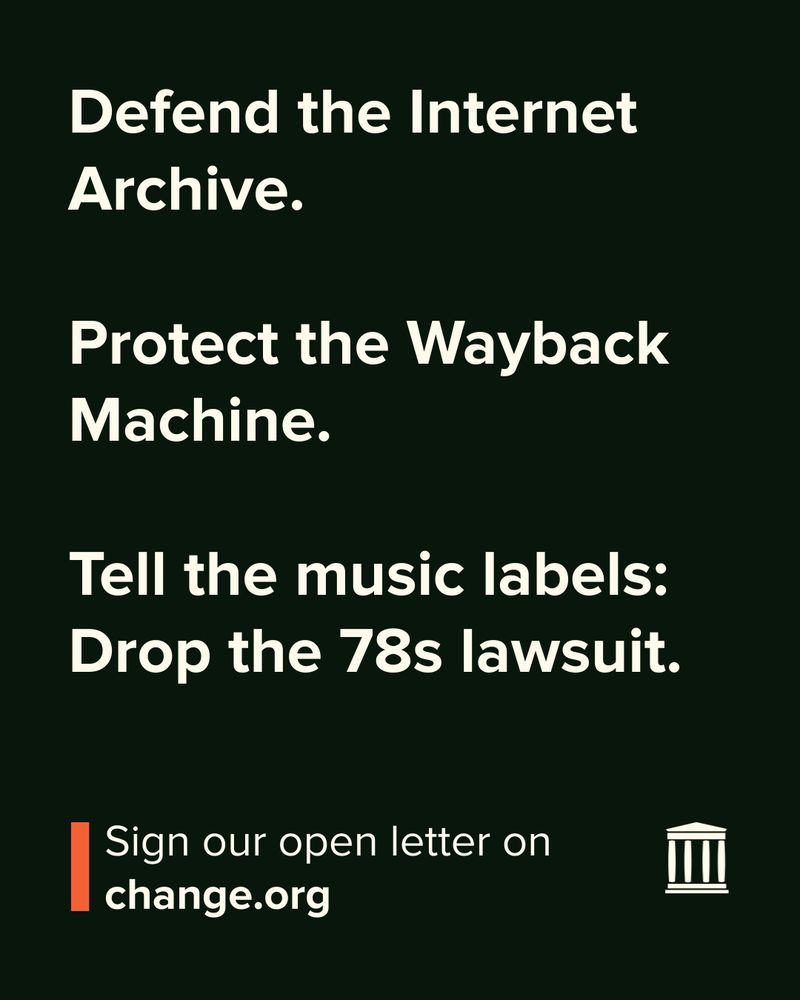
In the darkness of misinformation, silent edits and rewriting of history, WayBack machine offers a light in the dark.
It needs protecting at all costs.
At a time when information is being rewritten or erased online, a $700 million lawsuit from major record labels threatens to destroy the Wayback Machine.
Tell the labels to drop the 78s lawsuit.
👉 Sign our open letter: www.change.org/p/defend-the...
🧵⬇️
In the darkness of misinformation, silent edits and rewriting of history, WayBack machine offers a light in the dark.
It needs protecting at all costs.
They’re canceling all “DEI and misinformation/disinformation” grants.
And the guidance on how to fulfill the longstanding, legally mandated Broadening Participation requirement is utterly incoherent.
www.nsf.gov/updates-on-p...

Just keep my eyes open for the next release

Just keep my eyes open for the next release
“The CVE Program is invaluable to cyber community and a priority of CISA. Last night, CISA executed the option period on the contract to ensure there will be no lapse in critical CVE services. We appreciate our partners’ and stakeholders’ patience.”
“The CVE Program is invaluable to cyber community and a priority of CISA. Last night, CISA executed the option period on the contract to ensure there will be no lapse in critical CVE services. We appreciate our partners’ and stakeholders’ patience.”
From a reliable source. MITRE support for the CVE program is due to expire tomorrow. The attached letter was sent out to CVE Board Members.


Probably should have already been a control, but time to allowlist packages (or at least monitor) in the same vein as we (should) limit DNS, web and other external content?
2. The packages don’t exist. Which would normally cause an error but
3. Nefarious people have made malware under the package names that LLMs make up most often. So
4. Now the LLM code points to malware.
Probably should have already been a control, but time to allowlist packages (or at least monitor) in the same vein as we (should) limit DNS, web and other external content?
Cybersecurity should be a non-partisan issue that unites us in our shared mission to defend our country.
National security can’t afford the chilling effect on both public & private sector
www.lutasecurity.com/post/in-supp...

Cybersecurity should be a non-partisan issue that unites us in our shared mission to defend our country.
National security can’t afford the chilling effect on both public & private sector
www.lutasecurity.com/post/in-supp...
They were doing their jobs.
And they should be celebrated, not vilified.
They were doing their jobs.
And they should be celebrated, not vilified.
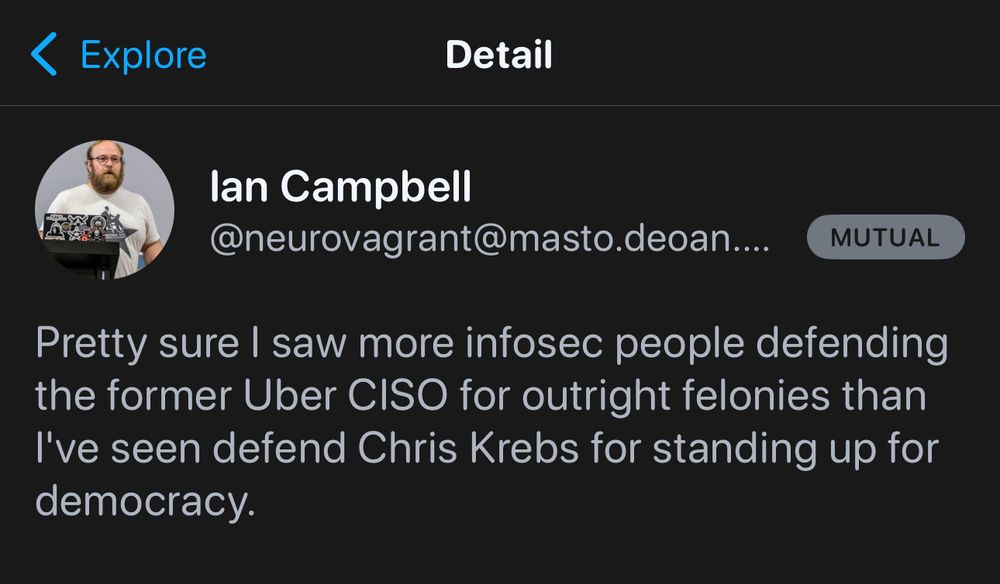
Targeting Chris Krebs and his employer (and CISA) like this is appalling. Chris, a Republican if memory serves, was a great leader for CISA.
Will the infosec industry do any better than the legal industry in showing solidarity?
www.whitehouse.gov/fact-sheets/...
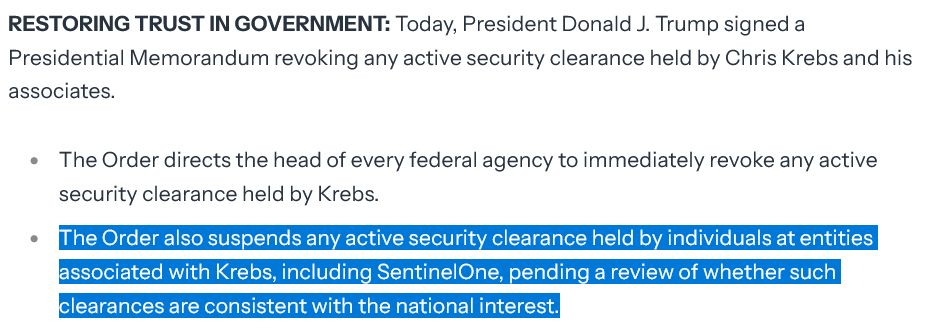
Targeting Chris Krebs and his employer (and CISA) like this is appalling. Chris, a Republican if memory serves, was a great leader for CISA.
www.landh.tech/blog/2025021...
www.landh.tech/blog/2025021...
There will still be workarounds, but they're making it harder
There will still be workarounds, but they're making it harder
My Panel: www.demosondemand.co...
All the panels: www.katilyst.com/res...

My Panel: www.demosondemand.co...
All the panels: www.katilyst.com/res...
This is why folks that don’t know, should listen to folks that do know.
But the folks that know have all been fired (and re-hired, on administrative leave). And the folks that are left are familiar with Peter’ Principles & proud to be scoring high on the Dunning-Kruger scale….
Astonishingly dumb thing to say.
This is why folks that don’t know, should listen to folks that do know.
But the folks that know have all been fired (and re-hired, on administrative leave). And the folks that are left are familiar with Peter’ Principles & proud to be scoring high on the Dunning-Kruger scale….





