
Nick Johnson
@sec-nj.bsky.social
Striving to be a great father, the partner my wife deserves and a decent human every day. I may not always succeed, but I’ll try again tomorrow.
Mets, Knicks, Bengals and THE Ohio State University have what’s left of my heart.
PNW == localhost
Mets, Knicks, Bengals and THE Ohio State University have what’s left of my heart.
PNW == localhost
Reposted by Nick Johnson
Do you enjoy guzzling real-time TLS certificate allocations, but don't want to use a third-party service (crt.sh, CertStream, etc.)? Drink straight from the Certificate Transparency log firehose using ctail:
$ go run github.com/hdm/ctail@latest -f -m '^autodiscover\.'
github.com/hdm/ctail
$ go run github.com/hdm/ctail@latest -f -m '^autodiscover\.'
github.com/hdm/ctail
June 21, 2025 at 5:57 AM
Do you enjoy guzzling real-time TLS certificate allocations, but don't want to use a third-party service (crt.sh, CertStream, etc.)? Drink straight from the Certificate Transparency log firehose using ctail:
$ go run github.com/hdm/ctail@latest -f -m '^autodiscover\.'
github.com/hdm/ctail
$ go run github.com/hdm/ctail@latest -f -m '^autodiscover\.'
github.com/hdm/ctail
Reposted by Nick Johnson
Something something leading indicator
www.greynoise.io/blog/surge-p...
www.greynoise.io/blog/surge-p...

Surge in Palo Alto Networks Scanner Activity Indicates Possible Upcoming Threats
Over the last 30 days, nearly 24,000 unique IP addresses have attempted to access these portals. The pattern suggests a coordinated effort to probe network defenses and identify exposed or vulnerable ...
www.greynoise.io
April 1, 2025 at 11:41 PM
Something something leading indicator
www.greynoise.io/blog/surge-p...
www.greynoise.io/blog/surge-p...
Reposted by Nick Johnson
If you want to test out my YARA rule linting work use this PR: github.com/VirusTotal/y...
If you want to get the basic gist of it, this config file change has documentation on it: github.com/VirusTotal/y...
Just set it in your config file and use "yr check" for now.
Happy #100DaysOfYARA. ;)
If you want to get the basic gist of it, this config file change has documentation on it: github.com/VirusTotal/y...
Just set it in your config file and use "yr check" for now.
Happy #100DaysOfYARA. ;)
January 9, 2025 at 2:58 PM
If you want to test out my YARA rule linting work use this PR: github.com/VirusTotal/y...
If you want to get the basic gist of it, this config file change has documentation on it: github.com/VirusTotal/y...
Just set it in your config file and use "yr check" for now.
Happy #100DaysOfYARA. ;)
If you want to get the basic gist of it, this config file change has documentation on it: github.com/VirusTotal/y...
Just set it in your config file and use "yr check" for now.
Happy #100DaysOfYARA. ;)
Reposted by Nick Johnson
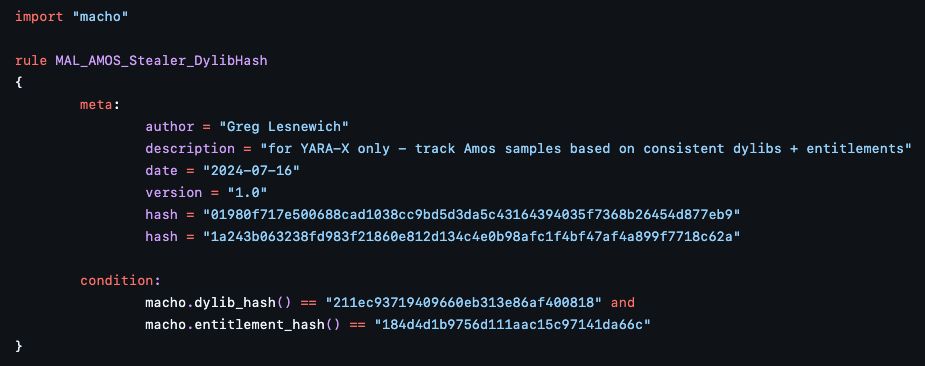
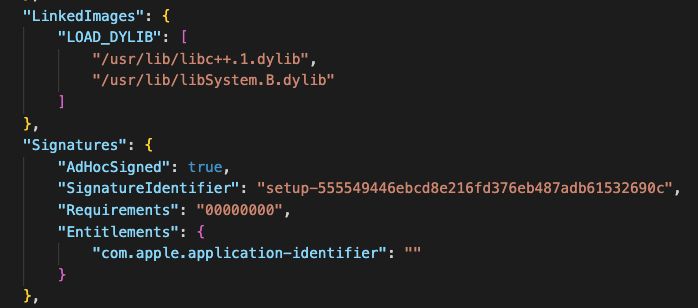
#100DaysofYARA day 1 - the Amos stealer is regularly evolving and updating its obfuscation techniques
You know what isn't changing?
the dylibs it depends on and the entitlements it requests from the OS. Combined, they give us excellent signal
github.com/100DaysofYAR...
You know what isn't changing?
the dylibs it depends on and the entitlements it requests from the OS. Combined, they give us excellent signal
github.com/100DaysofYAR...
January 1, 2025 at 4:36 PM
#100DaysofYARA day 1 - the Amos stealer is regularly evolving and updating its obfuscation techniques
You know what isn't changing?
the dylibs it depends on and the entitlements it requests from the OS. Combined, they give us excellent signal
github.com/100DaysofYAR...
You know what isn't changing?
the dylibs it depends on and the entitlements it requests from the OS. Combined, they give us excellent signal
github.com/100DaysofYAR...
Reposted by Nick Johnson
I looked at all the AWS OIDC integrations I could find to identify how they might be misconfigured and to understand the variations that different vendors have in how they set these up. www.wiz.io/blog/avoidin...

Avoiding mistakes with AWS OIDC integration conditions | Wiz Blog
Secure AWS OIDC integrations by avoiding common misconfigurations. Discover key IAM trust policy conditions for popular SaaS vendors to protect your cloud.
www.wiz.io
January 1, 2025 at 3:21 PM
I looked at all the AWS OIDC integrations I could find to identify how they might be misconfigured and to understand the variations that different vendors have in how they set these up. www.wiz.io/blog/avoidin...
Reposted by Nick Johnson
#100DaysofYARA 2025 edition begins tomorrow!
Any #CTI or #detectionengineering folks looking for a self-paced challenge to start the year with a laid back & fun community? Look no further!
The challenge is simple - write a YARA rule every day for 100 days
Any #CTI or #detectionengineering folks looking for a self-paced challenge to start the year with a laid back & fun community? Look no further!
The challenge is simple - write a YARA rule every day for 100 days
December 31, 2024 at 6:47 PM
#100DaysofYARA 2025 edition begins tomorrow!
Any #CTI or #detectionengineering folks looking for a self-paced challenge to start the year with a laid back & fun community? Look no further!
The challenge is simple - write a YARA rule every day for 100 days
Any #CTI or #detectionengineering folks looking for a self-paced challenge to start the year with a laid back & fun community? Look no further!
The challenge is simple - write a YARA rule every day for 100 days
Reposted by Nick Johnson
It’s too common to not have a record of why decisions were made. Getting the logic documented can help justify change or remind future decision makers about anticipated challenges that might otherwise be forgotten with time.
December 27, 2024 at 4:18 PM
It’s too common to not have a record of why decisions were made. Getting the logic documented can help justify change or remind future decision makers about anticipated challenges that might otherwise be forgotten with time.
Reposted by Nick Johnson
As 2024 comes to a close it's time to look back on the year. For the first time ever "SSRF to the metadata service" was NOT the top article on Hacking the Cloud! What was? You'll have to read the post to find out :) Happy holidays everyone!
hackingthe.cloud/blog/2024_wr...
hackingthe.cloud/blog/2024_wr...

2024 Cloud Security Highlights: Hacking the Cloud’s Year in Review - Hacking The Cloud
An end of year summary for Hacking the Cloud in 2024.
hackingthe.cloud
December 23, 2024 at 3:17 PM
As 2024 comes to a close it's time to look back on the year. For the first time ever "SSRF to the metadata service" was NOT the top article on Hacking the Cloud! What was? You'll have to read the post to find out :) Happy holidays everyone!
hackingthe.cloud/blog/2024_wr...
hackingthe.cloud/blog/2024_wr...
Reposted by Nick Johnson
Me and every parent I know right now

December 18, 2024 at 6:02 PM
Me and every parent I know right now
Reposted by Nick Johnson
New on Hacking the Cloud: Misconfigured OIDC trusting roles in AWS? Easy initial access. Eduard Agavriloae shares how to exploit IAM roles that are misconfigured to trust Terraform Cloud. As in....anyone's Terraform cloud. Happy holidays and happy hacking!
hackingthe.cloud/aws/exploita...
hackingthe.cloud/aws/exploita...

Exploiting Misconfigured Terraform Cloud OIDC AWS IAM Roles - Hacking The Cloud
Discover how to identify and exploit misconfigured AWS IAM roles using Terraform Cloud OIDC
hackingthe.cloud
December 13, 2024 at 3:26 PM
New on Hacking the Cloud: Misconfigured OIDC trusting roles in AWS? Easy initial access. Eduard Agavriloae shares how to exploit IAM roles that are misconfigured to trust Terraform Cloud. As in....anyone's Terraform cloud. Happy holidays and happy hacking!
hackingthe.cloud/aws/exploita...
hackingthe.cloud/aws/exploita...
Reposted by Nick Johnson
This blog is wild. “Secret Blizzard (Turla) has used the tools and infrastructure of at least 6 other threat actors during the past 7 years.”
www.microsoft.com/en-us/securi...
www.microsoft.com/en-us/securi...

Frequent freeloader part I: Secret Blizzard compromising Storm-0156 infrastructure for espionage | Microsoft Security Blog
Microsoft has observed Secret Blizzard compromising the infrastructure and backdoors of the Pakistan-based threat actor we track as Storm-0156 for espionage against the Afghanistan government and Indi...
www.microsoft.com
December 4, 2024 at 7:20 PM
This blog is wild. “Secret Blizzard (Turla) has used the tools and infrastructure of at least 6 other threat actors during the past 7 years.”
www.microsoft.com/en-us/securi...
www.microsoft.com/en-us/securi...
Reposted by Nick Johnson
It's Baaaaaack!!
Our Credit Card Canarytokens are out of beta and on your Canarytoken servers..
- Grab one;
- Stash it somewhere "safe";
- We will notify you if it's ever used!
Read more about it at blog.thinkst.com/2024/12/its-...
Our Credit Card Canarytokens are out of beta and on your Canarytoken servers..
- Grab one;
- Stash it somewhere "safe";
- We will notify you if it's ever used!
Read more about it at blog.thinkst.com/2024/12/its-...

December 2, 2024 at 5:56 PM
It's Baaaaaack!!
Our Credit Card Canarytokens are out of beta and on your Canarytoken servers..
- Grab one;
- Stash it somewhere "safe";
- We will notify you if it's ever used!
Read more about it at blog.thinkst.com/2024/12/its-...
Our Credit Card Canarytokens are out of beta and on your Canarytoken servers..
- Grab one;
- Stash it somewhere "safe";
- We will notify you if it's ever used!
Read more about it at blog.thinkst.com/2024/12/its-...
Reposted by Nick Johnson
One of the highest importance things in Security is thinking as a Graph not a List. Owning Twitter doesn't get you Twitter. It gets you everything that trusts Twitter.
John Lambert, one of the seniormost Microsoft people who has his hand fighting their greatest battles.
medium.com/@johnlatwc/d...
John Lambert, one of the seniormost Microsoft people who has his hand fighting their greatest battles.
medium.com/@johnlatwc/d...
Defender’s Mindset
This is a collection of thoughts, quips, and quotes from tweets, blogs, and presentations over the years. If you find them helpful, drop me…
medium.com
December 1, 2024 at 9:35 PM
One of the highest importance things in Security is thinking as a Graph not a List. Owning Twitter doesn't get you Twitter. It gets you everything that trusts Twitter.
John Lambert, one of the seniormost Microsoft people who has his hand fighting their greatest battles.
medium.com/@johnlatwc/d...
John Lambert, one of the seniormost Microsoft people who has his hand fighting their greatest battles.
medium.com/@johnlatwc/d...
Reposted by Nick Johnson
I wrote some guidance on how to use AWS's new RCP feature: www.wiz.io/blog/how-to-...

How to use AWS Resource Control Policies | Wiz Blog
Unlock the Power of AWS Resource Control Policies: Enforce Security and Streamline Governance Across Your Organization.
www.wiz.io
November 28, 2024 at 2:38 PM
I wrote some guidance on how to use AWS's new RCP feature: www.wiz.io/blog/how-to-...
Reposted by Nick Johnson
The self described “Shodan of AWS” is now live! This is an amazing project from Daniel Grzelak that helps democratize cloud resource enumeration for the masses. Very excited about this!
awseye.com
awseye.com

Awseye - See Inside AWS Accounts
Awseye tracks publicly accessible AWS data to help identify and secure known and exposed AWS resources. Empowering defenders with open-source intelligence.
awseye.com
November 26, 2024 at 2:31 AM
The self described “Shodan of AWS” is now live! This is an amazing project from Daniel Grzelak that helps democratize cloud resource enumeration for the masses. Very excited about this!
awseye.com
awseye.com
Reposted by Nick Johnson
This is huge! Cognito now supports passkeys!
aws.amazon.com/about-aws/wh...
aws.amazon.com/about-aws/wh...

Amazon Cognito now supports passwordless authentication for low-friction and secure logins - AWS
Discover more about what's new at AWS with Amazon Cognito now supports passwordless authentication for low-friction and secure logins
aws.amazon.com
November 25, 2024 at 4:59 PM
This is huge! Cognito now supports passkeys!
aws.amazon.com/about-aws/wh...
aws.amazon.com/about-aws/wh...
Reposted by Nick Johnson
DualCore and I spoke at the Red Team Village this year. Here are the slides. QR code with link to gist with all the reference links on last page. Unfortunately it wasn't recorded.
docs.google.com/presentation...
#redteam #purpleteam #redteamvillage
docs.google.com/presentation...
#redteam #purpleteam #redteamvillage
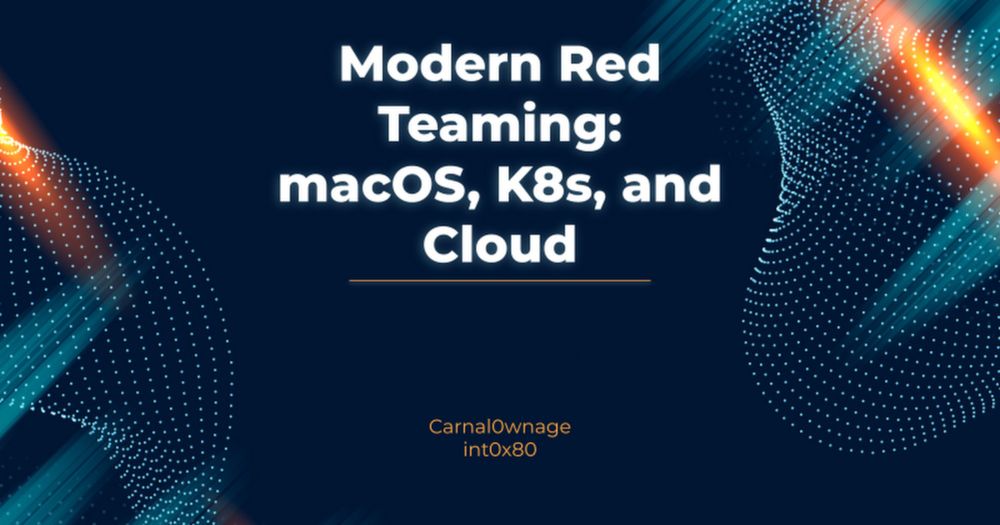
Modern Red Teaming: macOS, K8s, and Cloud - RTV 24 (Public)
Modern Red Teaming: macOS, K8s, and Cloud Carnal0wnage int0x80
docs.google.com
November 24, 2024 at 7:35 PM
DualCore and I spoke at the Red Team Village this year. Here are the slides. QR code with link to gist with all the reference links on last page. Unfortunately it wasn't recorded.
docs.google.com/presentation...
#redteam #purpleteam #redteamvillage
docs.google.com/presentation...
#redteam #purpleteam #redteamvillage
Reposted by Nick Johnson
We have a serious problem with vulnerable gateway/edge devices. Andrew Morris from Greynoise says exploitation of these types of vulns is at crisis levels. Get this stuff off your network boundary!
Full show: www.youtube.com/watch?v=Rxye...
Full show: www.youtube.com/watch?v=Rxye...
November 22, 2024 at 12:32 AM
We have a serious problem with vulnerable gateway/edge devices. Andrew Morris from Greynoise says exploitation of these types of vulns is at crisis levels. Get this stuff off your network boundary!
Full show: www.youtube.com/watch?v=Rxye...
Full show: www.youtube.com/watch?v=Rxye...
Reposted by Nick Johnson
Nzyme is a tool i'm excited to play with in alpha. @lennart.0x58ed.com is doing some incredible things.
github.com/nzymedefense...
github.com/nzymedefense...

November 24, 2024 at 7:19 PM
Nzyme is a tool i'm excited to play with in alpha. @lennart.0x58ed.com is doing some incredible things.
github.com/nzymedefense...
github.com/nzymedefense...
Reposted by Nick Johnson
I'm at the age where i'm sending my friends videos of my lawn, claiming how good it looks.
November 22, 2024 at 6:04 AM
I'm at the age where i'm sending my friends videos of my lawn, claiming how good it looks.
Reposted by Nick Johnson
Update your systems before someone else does it for you www.securityweek.com/apple-confir...

Apple Confirms Zero-Day Attacks Hitting macOS Systems
Apple rushes out out major macOS and iOS security updates to cover a pair of vulnerabilities already being exploited in the wild.
www.securityweek.com
November 21, 2024 at 6:04 PM
Update your systems before someone else does it for you www.securityweek.com/apple-confir...
Reposted by Nick Johnson
Overall a great read: www.cisa.gov/news-events/...
However this bit stands out to me - #infosec has become too dependent/reliant on EDR and has ignored network visibility and architectural controls, resulting in defeat if EDR is blind or bypassed.
However this bit stands out to me - #infosec has become too dependent/reliant on EDR and has ignored network visibility and architectural controls, resulting in defeat if EDR is blind or bypassed.

November 21, 2024 at 5:41 PM
Overall a great read: www.cisa.gov/news-events/...
However this bit stands out to me - #infosec has become too dependent/reliant on EDR and has ignored network visibility and architectural controls, resulting in defeat if EDR is blind or bypassed.
However this bit stands out to me - #infosec has become too dependent/reliant on EDR and has ignored network visibility and architectural controls, resulting in defeat if EDR is blind or bypassed.
Reposted by Nick Johnson
Turns out this little trick with enumerating OIDC providers for an account is actually easier than I thought. The backend is only checking the issuer field, and you can provide your own self signed JWTs, making it MUCH faster and MUCH easier to brute force. I’ll writeup for Hacking the Cloud soon.

November 21, 2024 at 3:00 AM
Turns out this little trick with enumerating OIDC providers for an account is actually easier than I thought. The backend is only checking the issuer field, and you can provide your own self signed JWTs, making it MUCH faster and MUCH easier to brute force. I’ll writeup for Hacking the Cloud soon.

