Sole founder of Host Unknown

blog.knowbe4.com/one-size-fit...

blog.knowbe4.com/one-size-fit...
Dear British Airways, I saw your latest business class sale advert. Beautiful photography, tasteful fonts, the usual tasteful smattering of champagne, winglets and folded duvets. Very on brand. And yet, in a strange way, it…
Dear British Airways, I saw your latest business class sale advert. Beautiful photography, tasteful fonts, the usual tasteful smattering of champagne, winglets and folded duvets. Very on brand. And yet, in a strange way, it…
-Yanluowang ransomware IAB pleads guilty
-US CBO hacked by foreign APT
-Singapore to punish scammers with cane beatings
-Chrome will remove XSLT support for security reasons
Podcast: risky.biz/RBNEWS502/
Newsletter: news.risky.biz/risky-bullet...

www.bbc.co.uk/news/article...

www.bbc.co.uk/news/article...
#CyberSecurity #RetailTech

#CyberSecurity #RetailTech

api.cyfluencer.com/s/a-ciso-s-g...

api.cyfluencer.com/s/a-ciso-s-g...
go.aembit.io/s/what-is-mc...

go.aembit.io/s/what-is-mc...
cybersec.picussecurity.com/s/the-louvre...

cybersec.picussecurity.com/s/the-louvre...
"..like saying that my house cat and a 650 pound wild tiger are the same because they’re both felines."
api.cyfluencer.com/s/what-s-the...

"..like saying that my house cat and a 650 pound wild tiger are the same because they’re both felines."
api.cyfluencer.com/s/what-s-the...
cybersec.pillar.security/s/agentic-ai...

cybersec.pillar.security/s/agentic-ai...
go.aembit.io/s/securing-a...

go.aembit.io/s/securing-a...
There’s an old story about a village that finally got electricity. Everyone bought fridges. A few months later, the elders gathered and suggested the unthinkable… “get rid of them!” Before the fridges, leftover food was shared. No one went to bed…
There’s an old story about a village that finally got electricity. Everyone bought fridges. A few months later, the elders gathered and suggested the unthinkable… “get rid of them!” Before the fridges, leftover food was shared. No one went to bed…
api.cyfluencer.com/s/how-the-br...

api.cyfluencer.com/s/how-the-br...
Have you got something original and interesting to share, but need somewhere to do it?
➡️ #BSidesLDN2025
More information and to submit your proposal: cfp.bsides.london/bsides-londo...
#Security #BSides #London

Have you got something original and interesting to share, but need somewhere to do it?
➡️ #BSidesLDN2025
More information and to submit your proposal: cfp.bsides.london/bsides-londo...
#Security #BSides #London
api.cyfluencer.com/s/will-ai-re...

api.cyfluencer.com/s/will-ai-re...
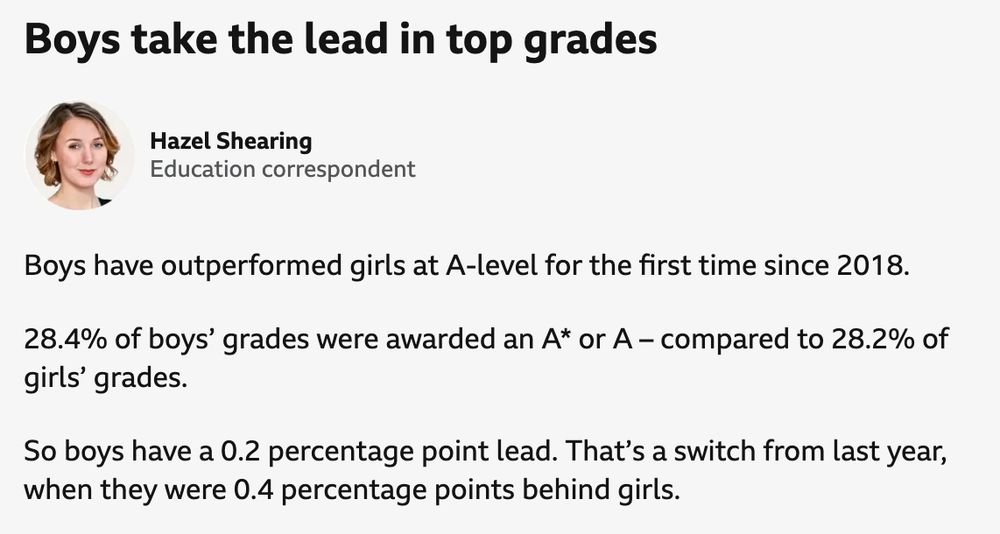
go.j4vv4d.com/0Qv100

go.j4vv4d.com/0Qv100
www.bbc.co.uk/news/article...

www.bbc.co.uk/news/article...
Main Link | Techmeme Permalink
Worth a read if you're in manufacturing or just enjoy a good 'robots meet reality' story.
blog.knowbe4.com/digital-fact...

Worth a read if you're in manufacturing or just enjoy a good 'robots meet reality' story.
blog.knowbe4.com/digital-fact...


