We’re adding CSS scroll-triggered animations for smoother UI, a native Sanitizer API to stop XSS, and WebGPU Compatibility mode for older hardware. Plus, new text-indent keywords for better typography.
We’re adding CSS scroll-triggered animations for smoother UI, a native Sanitizer API to stop XSS, and WebGPU Compatibility mode for older hardware. Plus, new text-indent keywords for better typography.
That led to the security layers for Closure Templates, Golang's html/template & polymer/lit, and to zero XSS over the last decade in Gmail and other projects.
bughunters.google.com/blog/secure-...
![Two rows from a three column table. The column headers, not shown, are [Control, Risk Category, Description].
SafeResponse Types
Injection
An automated conformance check should ensure that all HTTP responses are built via API abstractions that guarantee that they are constructed in an XSS-free way, for example via a safe auto-escaping template system.
Contextual Auto-Escaping Template System
Injection
All HTML responses should be built by a template system that supports contextual auto-escaping to guarantee the response is free of XSS vulnerabilities.](https://cdn.bsky.app/img/feed_thumbnail/plain/did:plc:xnx52zdoyuf777kntfughiwa/bafkreieyg6vmtuhrsccv23onjz7cwedvk2kyq5itczff7lr2m5fwqxvtje@jpeg)
That led to the security layers for Closure Templates, Golang's html/template & polymer/lit, and to zero XSS over the last decade in Gmail and other projects.
bughunters.google.com/blog/secure-...
…とはいえ、こんな初歩的な脆弱性も対策できてないのか、生成系は…
いや、あまねく文を取り込む学習という性質上、対策のしようがないのかもなぁ
なんかこう、すごいな
…とはいえ、こんな初歩的な脆弱性も対策できてないのか、生成系は…
いや、あまねく文を取り込む学習という性質上、対策のしようがないのかもなぁ
なんかこう、すごいな
- Site needs a content security policy to limit access to queries
- Site needs a frame security policy
- JS, CSS, Webmail, cPanel need to be secured/hidden
- "X-Content-Type-Options" header needs a "nosniff" value to make future XSS attacks difficult
- Site needs a content security policy to limit access to queries
- Site needs a frame security policy
- JS, CSS, Webmail, cPanel need to be secured/hidden
- "X-Content-Type-Options" header needs a "nosniff" value to make future XSS attacks difficult
blog.antoniusblock.net/posts/dom-cl...

blog.antoniusblock.net/posts/dom-cl...


Browse them here: portswigger.net/web-security...

Browse them here: portswigger.net/web-security...

cyberscoop.com/cisa-secure-...

cyberscoop.com/cisa-secure-...


They can steal data, inject malicious content, and damage your reputation.
Want to avoid that? Scan your website now for free with the C3S beta
Link in bio ⚡️
#CyberSecurity #VulnerabilityScanning #web #AI

They can steal data, inject malicious content, and damage your reputation.
Want to avoid that? Scan your website now for free with the C3S beta
Link in bio ⚡️
#CyberSecurity #VulnerabilityScanning #web #AI
📊 n/a
🏢 Noor alam
📝 Improper Neutralization of Script-Related HTML Tags in a Web Page (Basic XSS) vulnerability in Noor Alam Easy Media Download easy-media-download allows Refle...
🔗 https://euvd.enisa.europa.eu/vulnerability/EUVD-2026-1579
#cybersecurity #infosec #cve #euvd
📊 n/a
🏢 Noor alam
📝 Improper Neutralization of Script-Related HTML Tags in a Web Page (Basic XSS) vulnerability in Noor Alam Easy Media Download easy-media-download allows Refle...
🔗 https://euvd.enisa.europa.eu/vulnerability/EUVD-2026-1579
#cybersecurity #infosec #cve #euvd
CVE ID : CVE-2025-40975
Published : Jan. 12, 2026, 12:16 p.m. | 1 hour, 13 minutes ago
Description : Stored Cross-Site Scripting (XSS) vulnerability in WorkDo's HRMGo, consisting of a lack of proper validation ...
CVE ID : CVE-2025-40975
Published : Jan. 12, 2026, 12:16 p.m. | 1 hour, 13 minutes ago
Description : Stored Cross-Site Scripting (XSS) vulnerability in WorkDo's HRMGo, consisting of a lack of proper validation ...
But, I imagine most people who spread shit like this either don't know what an XSS exploit is, or they're willingly spreading misinformation for clout.
But, I imagine most people who spread shit like this either don't know what an XSS exploit is, or they're willingly spreading misinformation for clout.
also XSS exploits are kinda valuable things and would not be wasted on a fake survey site
also XSS exploits are kinda valuable things and would not be wasted on a fake survey site
The record can be seen here: pdsls.dev/at://did:plc...
The record can be seen here: pdsls.dev/at://did:plc...
i need embeds running arbitrary third party interfaces on bsky
i need XSS injection on the atmosphere
i want little widgets on my feed!!!
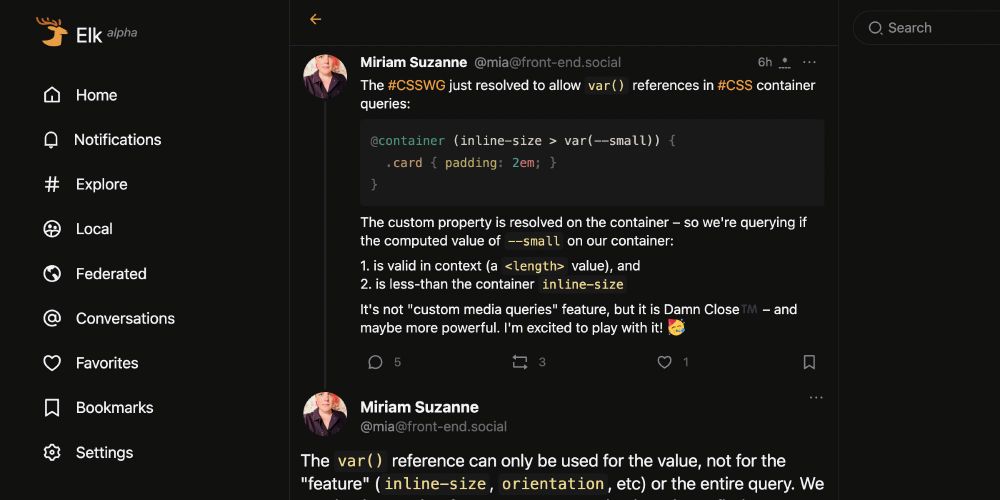
i need embeds running arbitrary third party interfaces on bsky
i need XSS injection on the atmosphere
i want little widgets on my feed!!!
It is never fun to find a vulnerability that could put users at risk that trust you as a dev, and for that I apologize and feel awful about it.
It is never fun to find a vulnerability that could put users at risk that trust you as a dev, and for that I apologize and feel awful about it.

Don't just render an , always sanitize.
Don't just render an , always sanitize.

