@muruenya@infosec.exchange

Well done...

Well done...
We have received many amazing talks already, but still room for more! 🤩
Https://PasswordsCon.org/
We have received many amazing talks already, but still room for more! 🤩
Https://PasswordsCon.org/
Contains a banger of an email 😅
doublepulsar.com/colt-technic...

Contains a banger of an email 😅
doublepulsar.com/colt-technic...
USB 2 vs USB 3, USB-A vs USB-C, the PD standard… this talk is full of interesting details 💎
And now I even understand why my USB-C power bank doesn’t work with *this* cable unless flipped 🙃
media.ccc.de/v/why2025-25...

USB 2 vs USB 3, USB-A vs USB-C, the PD standard… this talk is full of interesting details 💎
And now I even understand why my USB-C power bank doesn’t work with *this* cable unless flipped 🙃
media.ccc.de/v/why2025-25...
Cyberattacks against water is a troubling trend. Access to clean water is fundamental, and these types of attacks are direct threats to public health and safety.
#ICS #OTsecurity
www.reuters.com/en/p...
Cyberattacks against water is a troubling trend. Access to clean water is fundamental, and these types of attacks are direct threats to public health and safety.
#ICS #OTsecurity
www.reuters.com/en/p...
Bcrypt has a 72 char limit.
Django released patches back in 2013 that reduced max pwd length to 4095 chars (!), for good reasons: Pwd auth DoS attack.
www.helpnetsecurity.com/2013/09/17/t...

Bcrypt has a 72 char limit.
Django released patches back in 2013 that reduced max pwd length to 4095 chars (!), for good reasons: Pwd auth DoS attack.
www.helpnetsecurity.com/2013/09/17/t...
www.linkedin.com/pulse/harder...

www.linkedin.com/pulse/harder...
unit42.paloaltonetworks.com/unit-42-attr...

unit42.paloaltonetworks.com/unit-42-attr...
I won't be there this time around, but I know organizers, speakers & friends will make it great!
I won't be there this time around, but I know organizers, speakers & friends will make it great!

Read more in our press release ⤵️
www.europol.europa.eu/media-press/...

Read more in our press release ⤵️
www.europol.europa.eu/media-press/...
-2 arrests (1 preliminary arrest in France and 1 in Spain)
-7 arrest warrants issued (6 by Germany, and 1 by Spain)
-DDoS infrastructure taken down
-1k+ supporters identified and notified
www.europol.europa.eu/media-press/...

-2 arrests (1 preliminary arrest in France and 1 in Spain)
-7 arrest warrants issued (6 by Germany, and 1 by Spain)
-DDoS infrastructure taken down
-1k+ supporters identified and notified
www.europol.europa.eu/media-press/...
- LAPSUS$ www.cisa.gov/sites/defaul...
- and Scattered Spider www.cisa.gov/sites/defaul...

- LAPSUS$ www.cisa.gov/sites/defaul...
- and Scattered Spider www.cisa.gov/sites/defaul...
Just add /account/[email address] to the end of the haveibeenpwned URL.

Just add /account/[email address] to the end of the haveibeenpwned URL.

Meet Vladimir Vedeneev 👇

Meet Vladimir Vedeneev 👇
https://censys.com/blog/turning-off-the-information-flow-working-with-the-epa-to-secure-hundreds-of-exposed-water-hmis
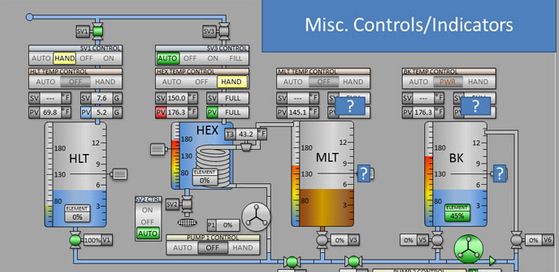
blog.talosintelligence.com/pathwiper-ta...

blog.talosintelligence.com/pathwiper-ta...
We can now reveal that the researchers who investigated it were confident that the Spanish government was behind it.

We can now reveal that the researchers who investigated it were confident that the Spanish government was behind it.
blogs.microsoft.com/on-the-issue...

blogs.microsoft.com/on-the-issue...
www.akamai.com/blog/securit...
www.akamai.com/blog/securit...


