🐙 https://github.com/mthcht
🐦 https://x.com/mthcht
📰 https://mthcht.medium.com
🐙 release: github.com/mthcht/Threa...
🌐 Site: mthcht.github.io/ThreatHuntin...
🧬 yara: github.com/mthcht/Threa...
🐾 Specific artifact lists: github.com/mthcht/aweso...
🐙 release: github.com/mthcht/Threa...
🌐 Site: mthcht.github.io/ThreatHuntin...
🧬 yara: github.com/mthcht/Threa...
🐾 Specific artifact lists: github.com/mthcht/aweso...

Interesting technique, if you're hunting for this, you can directly search the unicode characters in Splunk 🥷
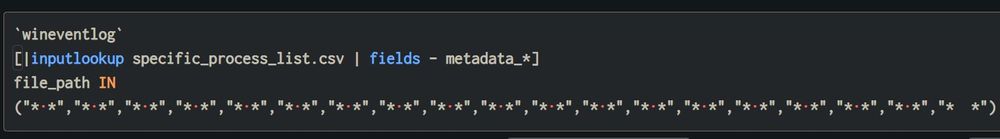
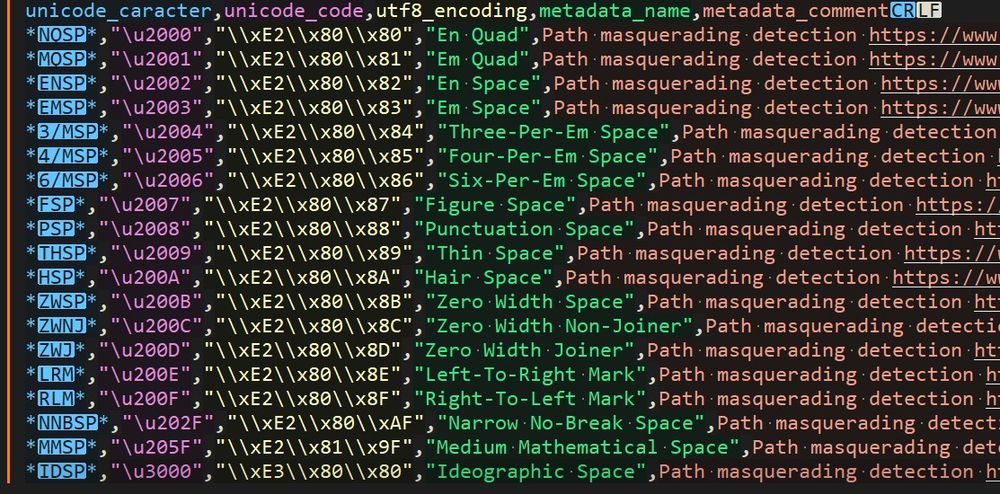
Interesting technique, if you're hunting for this, you can directly search the unicode characters in Splunk 🥷
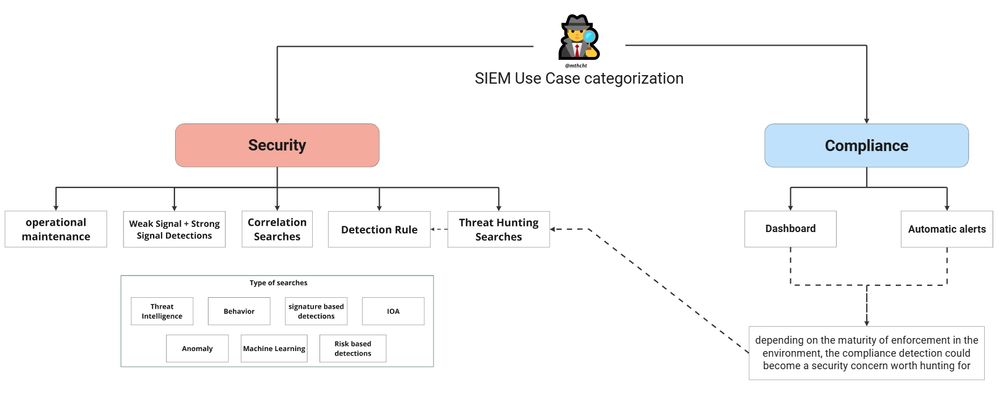
Identifiy hexadecimal IP addresses format in command lines with a "simple" regex (some default behaviors to exclude)
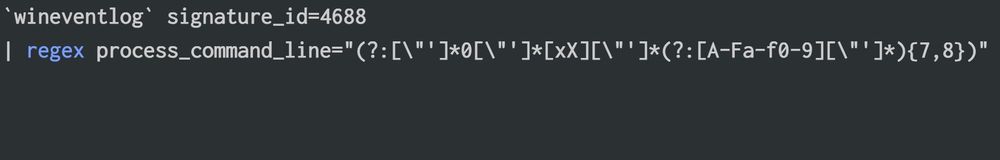
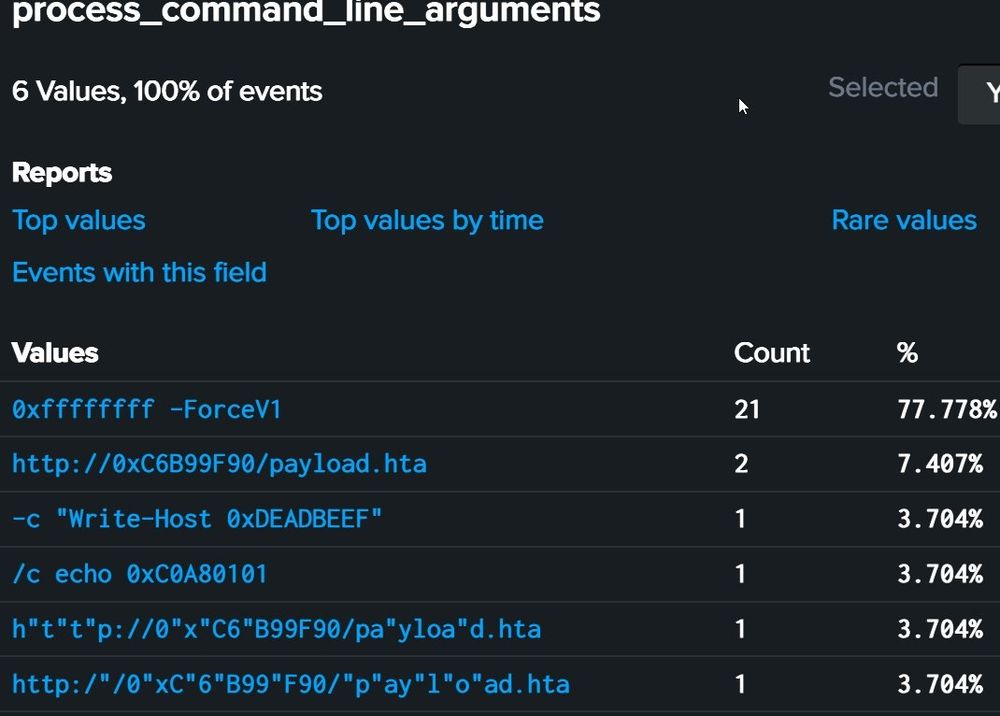
Identifiy hexadecimal IP addresses format in command lines with a "simple" regex (some default behaviors to exclude)
This query Extracts common special caracters from the process command line, counts occurrences, calculates ratio, and return commands with more than 20% specials caracters in it, could catch the quote insertions and url transformers techniques
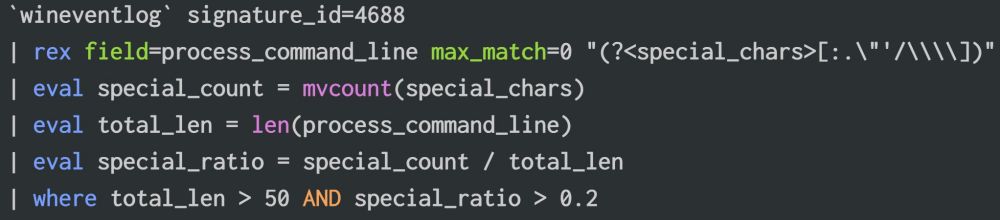
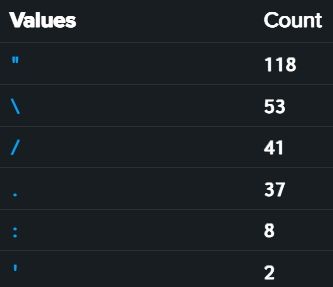
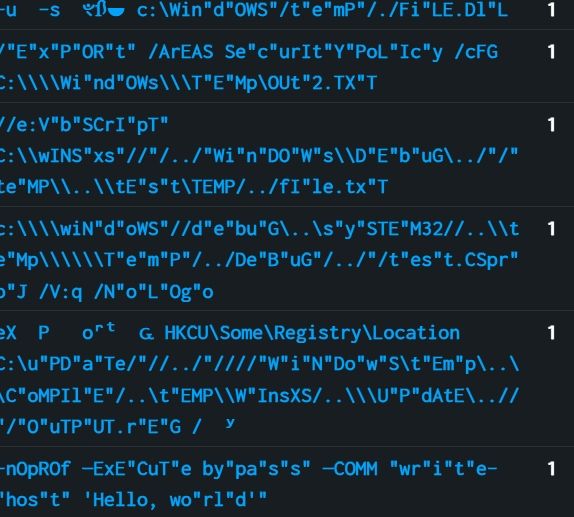
This query Extracts common special caracters from the process command line, counts occurrences, calculates ratio, and return commands with more than 20% specials caracters in it, could catch the quote insertions and url transformers techniques
(examples with EID 4688)
Mixed Case Randomization Detection:
This query counts uppercase/lowercase letters and return command lines with a near-equal ratio
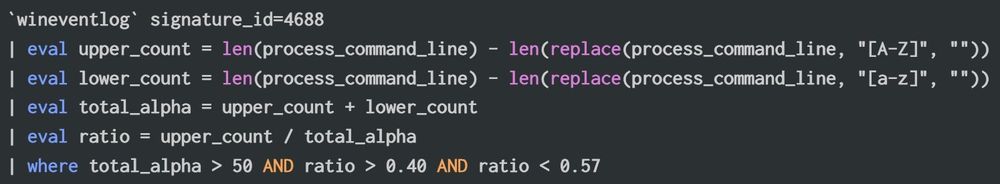
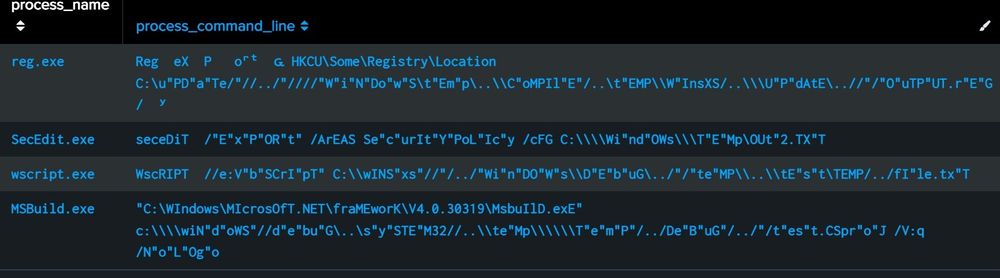
(examples with EID 4688)
Mixed Case Randomization Detection:
This query counts uppercase/lowercase letters and return command lines with a near-equal ratio
I'm searching for the domains, on my server I can resolve a record type for ~400 million domains per day with github.com/blechschmidt/m��� 😃 Massive improvement compared to other solutions!
I'm searching for the domains, on my server I can resolve a record type for ~400 million domains per day with github.com/blechschmidt/m��� 😃 Massive improvement compared to other solutions!
🐙 release: github.com/mthcht/Threa...
🌐 Site: mthcht.github.io/ThreatHuntin...
🧬yara: github.com/mthcht/Threa...
🐾Specific artifact lists: github.com/mthcht/aweso...

🐙 release: github.com/mthcht/Threa...
🌐 Site: mthcht.github.io/ThreatHuntin...
🧬yara: github.com/mthcht/Threa...
🐾Specific artifact lists: github.com/mthcht/aweso...
app.validin.com

app.validin.com



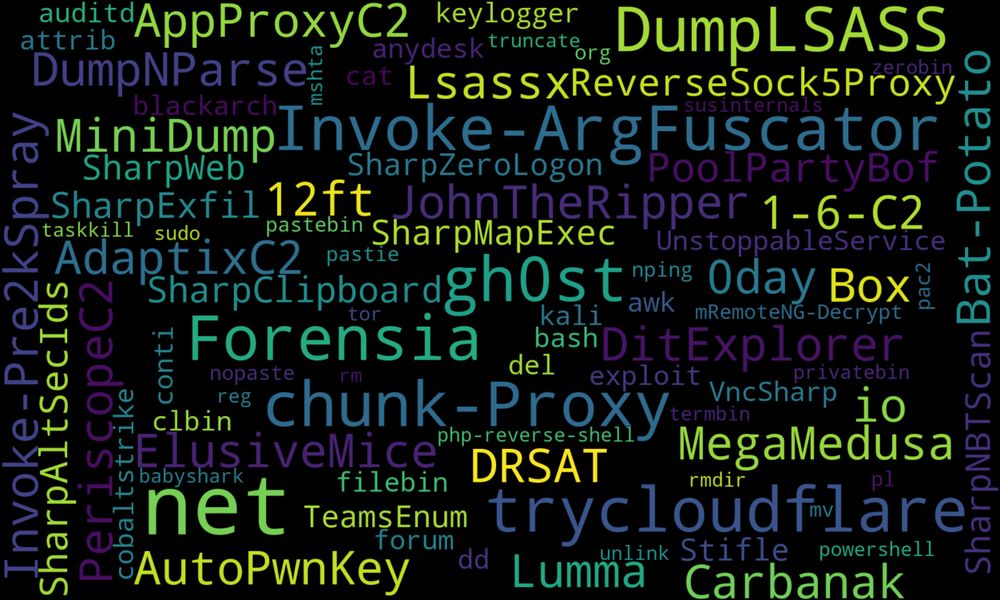
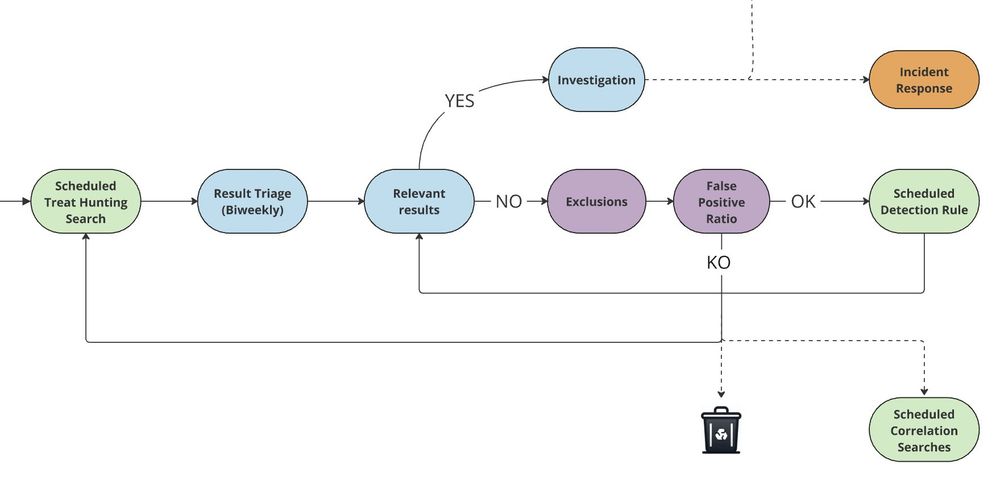
Prepare your #ThreatHunting sessions by gathering intelligence reports on specific topics - could be tools, patterns, or threat actor groups
🏛️ mthcht.github.io/ThreatIntel-...
Now featuring more than 1,000 search results in over 11,000 Intelligence Reports updated regularly!
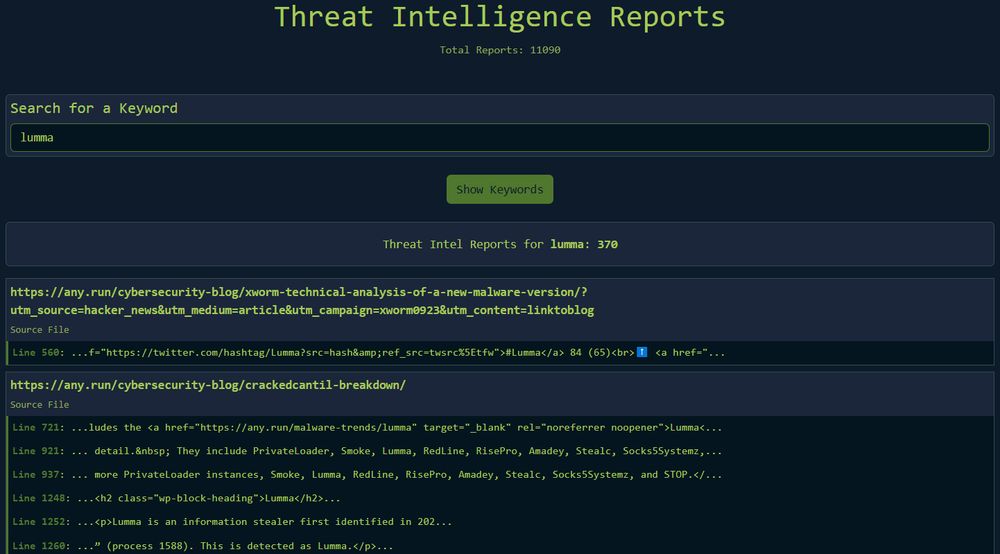


Prepare your #ThreatHunting sessions by gathering intelligence reports on specific topics - could be tools, patterns, or threat actor groups
🏛️ mthcht.github.io/ThreatIntel-...
Now featuring more than 1,000 search results in over 11,000 Intelligence Reports updated regularly!


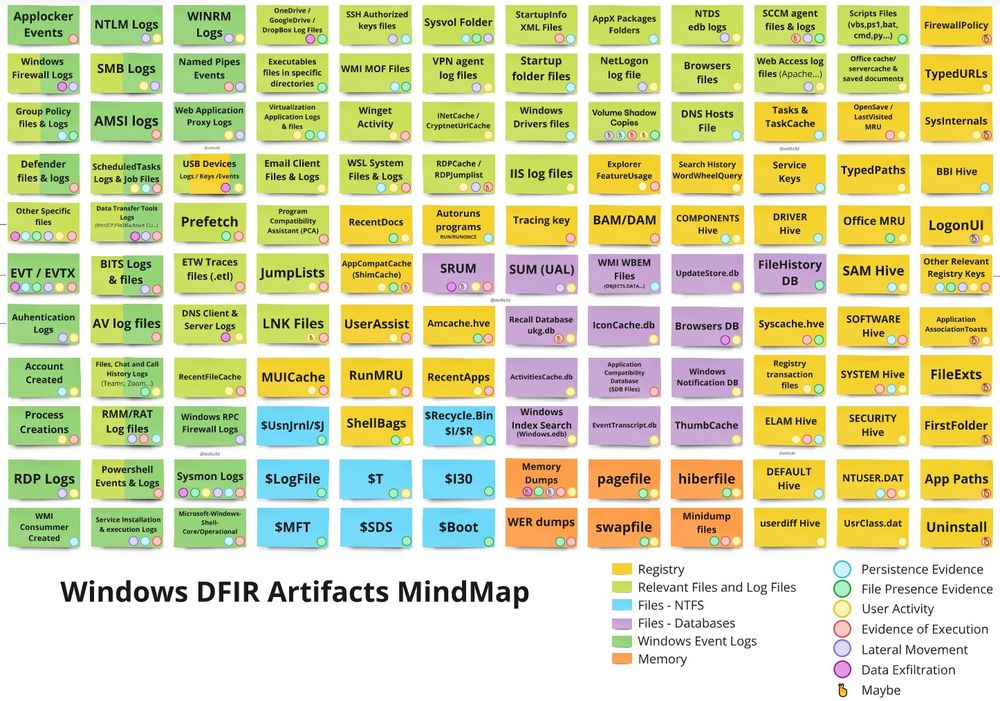
github.com/mthcht/aweso...



github.com/mthcht/aweso...