Debloat Discord: http://discord.gg/dvGXKaY5qr
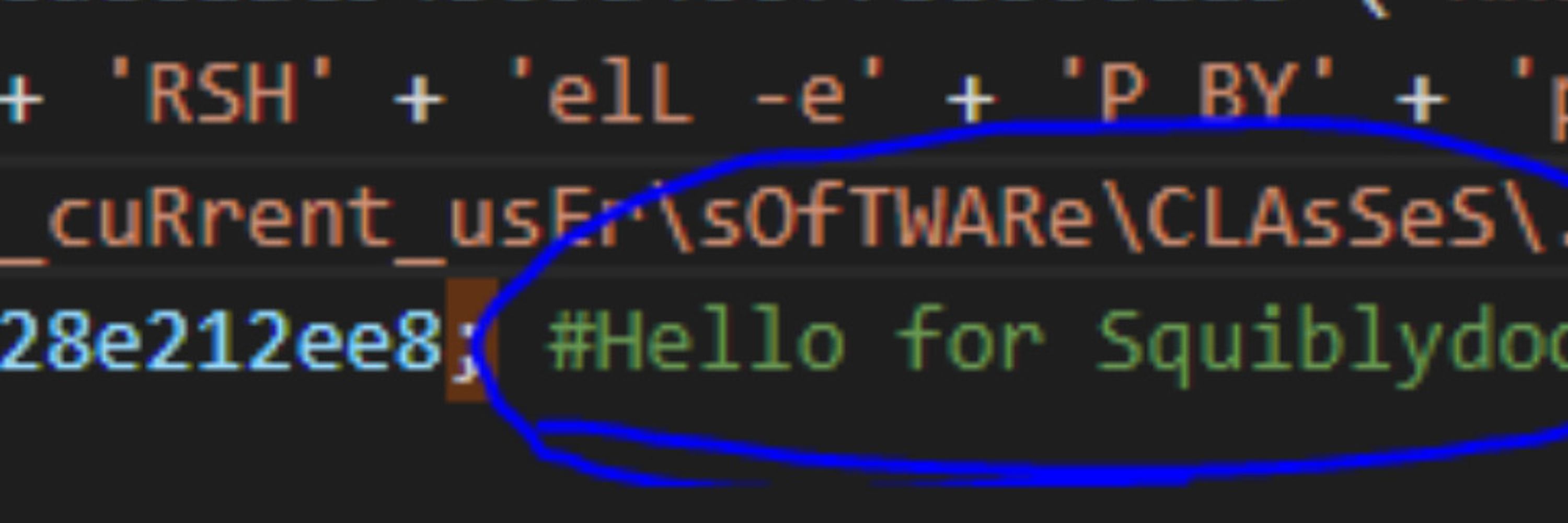
squiblydoo.blog
b409adb785f58f1de1cdf12e5c7c51a2
C2: 185.174.133.12
https://tria[.]ge/260211-2qa1ascw9d/behavioral1
#StealC
h/t @malwrhunterteam

b409adb785f58f1de1cdf12e5c7c51a2
C2: 185.174.133.12
https://tria[.]ge/260211-2qa1ascw9d/behavioral1
#StealC
h/t @malwrhunterteam
C2: boriserton27[.]anondns[.]net
e69c9a6742466a2770711804291f3fcf
FUD fake PDF, new serial #:
705f570e89ccbbcb32b8bb304537a2e9 suspected Romcom
"XRYUS TECHNOLOGIES CORPORATION" was used by RomCom
1/2


C2: boriserton27[.]anondns[.]net
e69c9a6742466a2770711804291f3fcf
FUD fake PDF, new serial #:
705f570e89ccbbcb32b8bb304537a2e9 suspected Romcom
"XRYUS TECHNOLOGIES CORPORATION" was used by RomCom
1/2
Loads ScreenConnect configured to connect to the domain zkyhgfvluyvjh[.]im
edbb4d8d6b549ea5ec04e8a43e51d5fffad9276a52dacad8bba4ea09d9b41063
h/t @malwrhunterteam
1/2
Loads ScreenConnect configured to connect to the domain zkyhgfvluyvjh[.]im
edbb4d8d6b549ea5ec04e8a43e51d5fffad9276a52dacad8bba4ea09d9b41063
h/t @malwrhunterteam
1/2
a08293e23e09d53692aca4b20974f270e48c58c53532c6cc715993d24e928e35
Probably not a purchasing agreement and probably not a CrowdStrike Falcon sensor.
Cert was reported for revocation
h/t @malwrhunterteam

a08293e23e09d53692aca4b20974f270e48c58c53532c6cc715993d24e928e35
Probably not a purchasing agreement and probably not a CrowdStrike Falcon sensor.
Cert was reported for revocation
h/t @malwrhunterteam

7ab39ede4268a615c04ef39b1b30cee3
Reaches out to zabbxsoftware[.]com
Interesting lures:
oficio20452026PCAP.exe
PCAP Police Request Response.exe
h/t @g0njxa

7ab39ede4268a615c04ef39b1b30cee3
Reaches out to zabbxsoftware[.]com
Interesting lures:
oficio20452026PCAP.exe
PCAP Police Request Response.exe
h/t @g0njxa
The real website, multibit[.]org, mentions that multibit was discontinued in 2017
The fake installer is signed by "Anhui Shanxian Tongxin Technology Co., Ltd."
More details in thread
h/t @malwrhunterteam
1/2


The real website, multibit[.]org, mentions that multibit was discontinued in 2017
The fake installer is signed by "Anhui Shanxian Tongxin Technology Co., Ltd."
More details in thread
h/t @malwrhunterteam
1/2
An actor using signer "CÔNG TY TNHH XB FLOW TECHNOLOGIES" leveraged a range of RMM tools and regularly contested abuse complaints.
Blogpost in thread
1/2

An actor using signer "CÔNG TY TNHH XB FLOW TECHNOLOGIES" leveraged a range of RMM tools and regularly contested abuse complaints.
Blogpost in thread
1/2
rifteyy.org/report/a...
Certificate has been reported and added to the CertGraveyard.

rifteyy.org/report/a...
Certificate has been reported and added to the CertGraveyard.
Seems identical to the last one.
Reaches out to the same domain: mstiserviceconfig[.]com
2c70e3b4af65679fc4f4c135dc1c03bd7ec2ae8065e2e5c50db3aaec0effc11f


Seems identical to the last one.
Reaches out to the same domain: mstiserviceconfig[.]com
2c70e3b4af65679fc4f4c135dc1c03bd7ec2ae8065e2e5c50db3aaec0effc11f
MagicSword makes use of certificates we report and blocks them within your environment.
I was really amazed by the work they do to block RMM and bad drivers. Now this further enables orgs to block malicious signers.
x.com/magicswordio/s...
MagicSword makes use of certificates we report and blocks them within your environment.
I was really amazed by the work they do to block RMM and bad drivers. Now this further enables orgs to block malicious signers.
x.com/magicswordio/s...
The 2,000th entry was "Auto Posto Silvestre Comercio de Combustiveis LTDA" (fuel sales), a certificate issued to a cybercriminal, used to target Brazil with a fake PDF "Requisitos_para_regularizar_sua_empresa.exe".
1/2

The 2,000th entry was "Auto Posto Silvestre Comercio de Combustiveis LTDA" (fuel sales), a certificate issued to a cybercriminal, used to target Brazil with a fake PDF "Requisitos_para_regularizar_sua_empresa.exe".
1/2
I feel like we could be friends, if we aren't already.
They consistently leave comments and downvote stuff that I then see a day or two later.
www[.]virustotal[.]com/gui/user/bsforvt727
I feel like we could be friends, if we aren't already.
They consistently leave comments and downvote stuff that I then see a day or two later.
www[.]virustotal[.]com/gui/user/bsforvt727
Checkpoint published research on VoidLink C2 framework.
They call it "advanced malware framework"; but maybe I'm not sure what "advanced" means in this context.
Rule at end
1/2

Checkpoint published research on VoidLink C2 framework.
They call it "advanced malware framework"; but maybe I'm not sure what "advanced" means in this context.
Rule at end
1/2
Came across a low detection malware which seems YARA resistant. Currently in use by ransomware actor.
I'll post some thoughts, but would love suggestions from others.
I'll explain the malware and show the best I could come up with.
Rule at bottom
1/7

Came across a low detection malware which seems YARA resistant. Currently in use by ransomware actor.
I'll post some thoughts, but would love suggestions from others.
I'll explain the malware and show the best I could come up with.
Rule at bottom
1/7
Came across a low detection malware which seems YARA resistant. Currently in use by ransomware actor.
I'll post some thoughts, but would love suggestions from others.
I'll explain the malware and show the best I could come up with.
Rule at bottom
1/7

Came across a low detection malware which seems YARA resistant. Currently in use by ransomware actor.
I'll post some thoughts, but would love suggestions from others.
I'll explain the malware and show the best I could come up with.
Rule at bottom
1/7
Came across a low detection malware which seems YARA resistant. Currently in use by ransomware actor.
I'll post some thoughts, but would love suggestions from others.
I'll explain the malware and show the best I could come up with.
Rule at bottom
1/7

Came across a low detection malware which seems YARA resistant. Currently in use by ransomware actor.
I'll post some thoughts, but would love suggestions from others.
I'll explain the malware and show the best I could come up with.
Rule at bottom
1/7
VirusTotal uses CAPE sandbox to identify many malware families and determine if they can extract the malware's configuration. Since they use CAPE, we can often see their logic. Today, we'll suggest edits to a rule for AgentTesla.
Rule at end.
1/10

VirusTotal uses CAPE sandbox to identify many malware families and determine if they can extract the malware's configuration. Since they use CAPE, we can often see their logic. Today, we'll suggest edits to a rule for AgentTesla.
Rule at end.
1/10
In looking at automatic YARA generation, yarGen-Go is a must. Just released by @cyb3rops, it is a rewrite and advancement from the original yarGen.
We'll look at the same malware from day 10; a targeted HavocC2 loader with decoy.
rule at bottom
1/5

In looking at automatic YARA generation, yarGen-Go is a must. Just released by @cyb3rops, it is a rewrite and advancement from the original yarGen.
We'll look at the same malware from day 10; a targeted HavocC2 loader with decoy.
rule at bottom
1/5
There are a few lines of thinking around automatic YARA generation. I'm exploring these as part of this challenge. Today's we'll look at MCRIT.
MCRIT asks what do we learn by comparing samples? Can we find functions unique to the family?
rule at end
1/5

There are a few lines of thinking around automatic YARA generation. I'm exploring these as part of this challenge. Today's we'll look at MCRIT.
MCRIT asks what do we learn by comparing samples? Can we find functions unique to the family?
rule at end
1/5
YARA looks for the header used in a .SCPT file used by BlueNoroff (DPRK) to target MacOS systems.
Script is delivered to victims disguised as a Zoom meeting launcher.
e.g. a7c7d75c33aa809c231f1b22521ae680248986c980b45aa0881e19c19b7b1892
Rule at end
1/3

YARA looks for the header used in a .SCPT file used by BlueNoroff (DPRK) to target MacOS systems.
Script is delivered to victims disguised as a Zoom meeting launcher.
e.g. a7c7d75c33aa809c231f1b22521ae680248986c980b45aa0881e19c19b7b1892
Rule at end
1/3
For many years, many attackers tried to keep their binaries small. However, the others found the opposite works too: extremely large binaries can cause problems with analysis.
What can be done about these large executables?
Rule at end
1/6

For many years, many attackers tried to keep their binaries small. However, the others found the opposite works too: extremely large binaries can cause problems with analysis.
What can be done about these large executables?
Rule at end
1/6
@malwrhunterteam identified a suspicious file signed by "Xiamen Jialan Guang Information Technology Service Co., Ltd."
While we have a pretty good idea it'll be abused, it hasn't been yet.
So, lets watch for it to be abused.
Rule at end
1/5
@malwrhunterteam identified a suspicious file signed by "Xiamen Jialan Guang Information Technology Service Co., Ltd."
While we have a pretty good idea it'll be abused, it hasn't been yet.
So, lets watch for it to be abused.
Rule at end
1/5
In December and again in January, an unknown actor replaced the download on EmEditor's website with a malicious installer. Each time, the download was a trojan installer with a valid code-signing signature.
How can we detect this?
Rule at end
1/6

In December and again in January, an unknown actor replaced the download on EmEditor's website with a malicious installer. Each time, the download was a trojan installer with a valid code-signing signature.
How can we detect this?
Rule at end
1/6
The Cert Graveyard project reports and documents abuse code-signing including Apple issued certificates.
When reporting a certificate, we want to ensure Apple has all the identifiers they need to investigate and act.
Rule at end
1/7

The Cert Graveyard project reports and documents abuse code-signing including Apple issued certificates.
When reporting a certificate, we want to ensure Apple has all the identifiers they need to investigate and act.
Rule at end
1/7

