export MANPAGER='vim +MANPAGER --not-a-term -'
to use vim as your man pager.
It has syntax highlighting. You can jump to other man pages by pressing 'K' <3
export MANPAGER='vim +MANPAGER --not-a-term -'
to use vim as your man pager.
It has syntax highlighting. You can jump to other man pages by pressing 'K' <3
I'll publish all solutions next Monday, but will be keeping the challenge online indefinitely.
blog.ajxchapman.com/xss/challeng...

I'll publish all solutions next Monday, but will be keeping the challenge online indefinitely.
keynoting @re-verse.io

keynoting @re-verse.io
www.ambionics.io/blog/scalpel
Piper may be enough for message viewers, but if you need **editors**, give it a try!
www.ambionics.io/blog/scalpel
Piper may be enough for message viewers, but if you need **editors**, give it a try!
A decade ago, #clickjacking was the hot new #attack—tricking users into clicking invisible #frames layered over legit websites, unknowingly performing actions on their social media, corporate accounts, or even banks.
1/3

A decade ago, #clickjacking was the hot new #attack—tricking users into clicking invisible #frames layered over legit websites, unknowingly performing actions on their social media, corporate accounts, or even banks.
1/3
portswigger.net/research/byp...

portswigger.net/research/byp...
https://blog.doyensec.com/2025/01/09/cspt-file-upload.html
#BBRENewsletter87
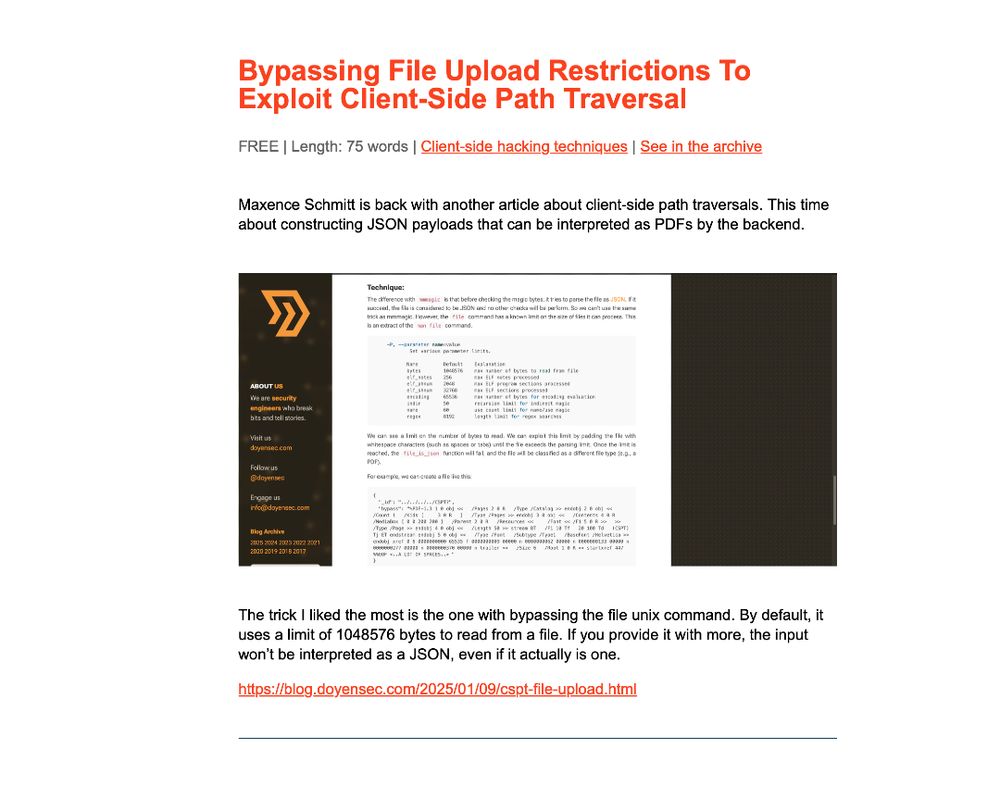
https://blog.doyensec.com/2025/01/09/cspt-file-upload.html
#BBRENewsletter87
Responding instead of reacting is powerful.

Responding instead of reacting is powerful.
probably one of the few ai-image generation tasks that human artists cannot really do right now
https://www.reddit.com/r/StableDiffusion/comments/141hg9x/controlnet_for_qr_code/




probably one of the few ai-image generation tasks that human artists cannot really do right now
https://www.reddit.com/r/StableDiffusion/comments/141hg9x/controlnet_for_qr_code/

