
The other side is at @a (photography, art and free software at large) […]
[bridged from https://infosec.exchange/@adulau on the fediverse by https://fed.brid.gy/ ]
Was staring into the expanse that is the untagged sessions in our fleet and eventually plotted a course towards the ICMP system, which eventually led me to a planet that was beaconing with some oddly […]
[Original post on mastodon.social]


Was staring into the expanse that is the untagged sessions in our fleet and eventually plotted a course towards the ICMP system, which eventually led me to a planet that was beaconing with some oddly […]
[Original post on mastodon.social]

It seems Firefox blocks access to a predefined list of TCP ports, and this has been in place for […]
It seems Firefox blocks access to a predefined list of TCP ports, and this has been in place for […]
The standard is similar to the @cve record format with some extensions (via the `X_` prefixes) for GCVE format and the reference implementation vulnerability-lookup. This […]
The standard is similar to the @cve record format with some extensions (via the `X_` prefixes) for GCVE format and the reference implementation vulnerability-lookup. This […]
#cve #vulnerability #opensource #vulnerabilitymanagement #cybersecurity
🔗 https://www.vulnerability-lookup.org/2025/11/08/unlock-your-brain-2025/
#cve #vulnerability #opensource #vulnerabilitymanagement #cybersecurity
🔗 https://www.vulnerability-lookup.org/2025/11/08/unlock-your-brain-2025/
Pretty cool stuff seen at the @UYBHYS workshop
#5g #fuzzing #opensource #cybersecurity
🔗 https://github.com/ANSSI-FR/py5sig

Pretty cool stuff seen at the @UYBHYS workshop
#5g #fuzzing #opensource #cybersecurity
🔗 https://github.com/ANSSI-FR/py5sig
Pretty cool stuff seen at the @UYBHYS workshop
#5g #fuzzing #opensource #cybersecurity
🔗 https://github.com/ANSSI-FR/py5sig

Pretty cool stuff seen at the @UYBHYS workshop
#5g #fuzzing #opensource #cybersecurity
🔗 https://github.com/ANSSI-FR/py5sig
It comes with detailed attributes such as manufacturer, cost, and technical specs.
You can now easily classify, model, and share […]
[Original post on infosec.exchange]


It comes with detailed attributes such as manufacturer, cost, and technical specs.
You can now easily classify, model, and share […]
[Original post on infosec.exchange]
Distributed publishing is not weakening the security advisory publication but it’s providing additional valuable sources.
#gcve #cve
🔗 https://www.openwall.com/lists/oss-security/2025/10/27/1
Distributed publishing is not weakening the security advisory publication but it’s providing additional valuable sources.
#gcve #cve
🔗 https://www.openwall.com/lists/oss-security/2025/10/27/1
The open source project providing real-time ransomware intelligence.
Thanks to @F_kZ_ for the incredible work.
#ransomware #threatintelligence #threatintel #opensource
🔗 https://www.ransomlook.io/

The open source project providing real-time ransomware intelligence.
Thanks to @F_kZ_ for the incredible work.
#ransomware #threatintelligence #threatintel #opensource
🔗 https://www.ransomlook.io/
The open source project providing real-time ransomware intelligence.
Thanks to @F_kZ_ for the incredible work.
#ransomware #threatintelligence #threatintel #opensource
🔗 https://www.ransomlook.io/

The open source project providing real-time ransomware intelligence.
Thanks to @F_kZ_ for the incredible work.
#ransomware #threatintelligence #threatintel #opensource
🔗 https://www.ransomlook.io/
is from Peter Gutmann in the cryptography mailing-list.
Given that after 20 years and hundreds of millions of dollars spent
researchers have yet to demonstrate a single legitimate […]
[Original post on infosec.exchange]

is from Peter Gutmann in the cryptography mailing-list.
Given that after 20 years and hundreds of millions of dollars spent
researchers have yet to demonstrate a single legitimate […]
[Original post on infosec.exchange]
[Original post on infosec.exchange]

[Original post on infosec.exchange]
🔗 […]
[Original post on infosec.exchange]

🔗 […]
[Original post on infosec.exchange]
- Poorly scraped #wikipedia pages, sometimes even merging unrelated disambiguation content
- A single-pass LLM prompted without care or validation
The result is a pile of […]
- Poorly scraped #wikipedia pages, sometimes even merging unrelated disambiguation content
- A single-pass LLM prompted without care or validation
The result is a pile of […]
This talk from @wr is a masterpiece if you want to dive into all the gory details of the X.509 certificate format.
#hacklu #cybersecurity #certificate #threatintel
This talk from @wr is a masterpiece if you want to dive into all the gory details of the X.509 certificate format.
#hacklu #cybersecurity #certificate #threatintel
We published all the materials from the workshop given at #hacklu 2025
#gcve #vulnerabilitymanagement #opensource #cybersecurity […]
[Original post on infosec.exchange]

We published all the materials from the workshop given at #hacklu 2025
#gcve #vulnerabilitymanagement #opensource #cybersecurity […]
[Original post on infosec.exchange]


#hacklu2025



#hacklu2025
Curious about a developer’s vibe-coding journey? @iglocska is sharing his experiments and insights at hack.lu 2025!
#vibecoding #ai #cybersecurity #hacklu
Curious about a developer’s vibe-coding journey? @iglocska is sharing his experiments and insights at hack.lu 2025!
#vibecoding #ai #cybersecurity #hacklu
If you need to document or describe or decode binary format, Kaitai is clearly there to help.
https://kaitai.io/ @kaitai
#hacklu #kaitai #dfir #cybersecurity
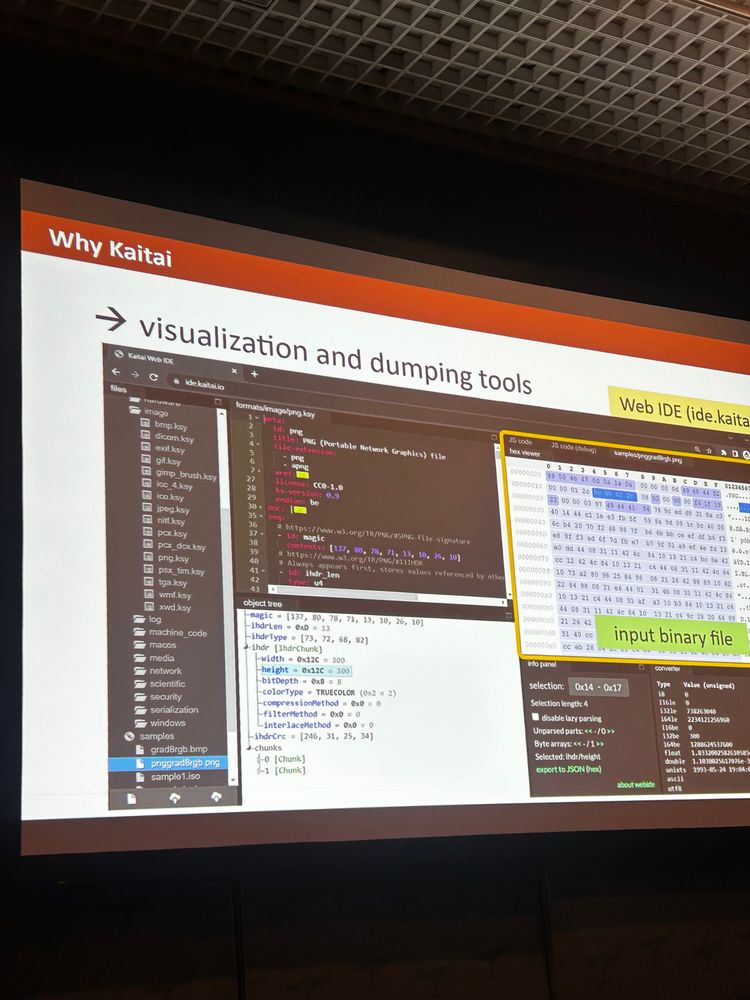
If you need to document or describe or decode binary format, Kaitai is clearly there to help.
https://kaitai.io/ @kaitai
#hacklu #kaitai #dfir #cybersecurity
Smart contracts can directly store malware!

Smart contracts can directly store malware!
#yaml #cybersecurity #hacklu
#yaml #cybersecurity #hacklu

