Up now at #hacklu2025 is a talk on OpenWRT and LuCI vulnerability research -> Stanislav Dashevskyi and Francesco la Spina with “No way to enable SSH access to your router? The vendor might have something to hide”

October 21, 2025 at 2:05 PM
Up now at #hacklu2025 is a talk on OpenWRT and LuCI vulnerability research -> Stanislav Dashevskyi and Francesco la Spina with “No way to enable SSH access to your router? The vendor might have something to hide”
After the break second up is Antoine Goichot with “OverLAPS, Overriding LAPS Logic” here at #hacklu2025 !!
They managed to get full root and AD control by desyncing the LAPS password
They managed to get full root and AD control by desyncing the LAPS password

October 21, 2025 at 3:11 PM
After the break second up is Antoine Goichot with “OverLAPS, Overriding LAPS Logic” here at #hacklu2025 !!
They managed to get full root and AD control by desyncing the LAPS password
They managed to get full root and AD control by desyncing the LAPS password
Now its time for something that looks like an Intel-ops type of talk: “Persōna theory: Infiltration & Deception of emerging threats groups” and its @tammyharper on stage presenting at #hacklu2025
The recruitment phase is a really good point to infiltrate […]
[Original post on mastodon.social]
The recruitment phase is a really good point to infiltrate […]
[Original post on mastodon.social]



October 24, 2025 at 8:47 AM
Now its time for something that looks like an Intel-ops type of talk: “Persōna theory: Infiltration & Deception of emerging threats groups” and its @tammyharper on stage presenting at #hacklu2025
The recruitment phase is a really good point to infiltrate […]
[Original post on mastodon.social]
The recruitment phase is a really good point to infiltrate […]
[Original post on mastodon.social]
Next up is Rémi Matasse and Pierre Martin with “Livewire: remote command execution through unmarshalling”
#hacklu2025
#hacklu2025


October 23, 2025 at 1:40 PM
Next up is Rémi Matasse and Pierre Martin with “Livewire: remote command execution through unmarshalling”
#hacklu2025
#hacklu2025
Bad stuff hidingin Chinese cloud. Ever tried takedown requests to Alibaba? I wonder that works. #hacklu2025

October 22, 2025 at 9:34 AM
Bad stuff hidingin Chinese cloud. Ever tried takedown requests to Alibaba? I wonder that works. #hacklu2025
Next up is another #hacklu “frequent flyer” Vladimir Kropotov with “Russian speaking underground- changes in the risks, attack surface and modus operandi”
At #hacklu2025
At #hacklu2025


October 24, 2025 at 9:27 AM
Next up is another #hacklu “frequent flyer” Vladimir Kropotov with “Russian speaking underground- changes in the risks, attack surface and modus operandi”
At #hacklu2025
At #hacklu2025
Hack.lu talks are already coming online, follow @ministraitor !
#hacklu2025 https://infosec.exchange/@ministraitor/115412139541011752
#hacklu2025 https://infosec.exchange/@ministraitor/115412139541011752
Cooper (@ministraitor@infosec.exchange)
@hack_lu Anti-Forensics - You Are Doing It Wrong (Believe Me, I'm An IR Consultant) - Stephan Berger https://youtu.be/LjCnCetbfBc #HackLu
infosec.exchange
October 21, 2025 at 1:54 PM
Hack.lu talks are already coming online, follow @ministraitor !
#hacklu2025 https://infosec.exchange/@ministraitor/115412139541011752
#hacklu2025 https://infosec.exchange/@ministraitor/115412139541011752
At #hacklu2025, Jiří Vinopal has identified a massive attack campaign from the Chinese Silver Fox APT targeting Windows endpoints using a combination if methods and Microsoft bugs plus vulnerabilities in the truesight.sys known vulnerable driver.



October 22, 2025 at 9:32 AM
At #hacklu2025, Jiří Vinopal has identified a massive attack campaign from the Chinese Silver Fox APT targeting Windows endpoints using a combination if methods and Microsoft bugs plus vulnerabilities in the truesight.sys known vulnerable driver.
As #hacklu2025 draws slowly towards a happy ending and many many presentations and conversations later, by and with so many fantastic people, I’d like to propose to you to meet up again in the spring, instead of waiting all until #hacklu2026.
If you’re interested you can continue the […]
If you’re interested you can continue the […]
Original post on mastodon.social
mastodon.social
October 24, 2025 at 12:53 PM
As #hacklu2025 draws slowly towards a happy ending and many many presentations and conversations later, by and with so many fantastic people, I’d like to propose to you to meet up again in the spring, instead of waiting all until #hacklu2026.
If you’re interested you can continue the […]
If you’re interested you can continue the […]
First up at #hacklu2025 after an Epoch and the afternoon break (get your devices and applications made 2038 safe) we have Alain Mowat on stage digging into the Dell thin client called “Wyse Management Suite” which can manage Wyse devices but also a ton of other devices!


October 23, 2025 at 3:13 PM
First up at #hacklu2025 after an Epoch and the afternoon break (get your devices and applications made 2038 safe) we have Alain Mowat on stage digging into the Dell thin client called “Wyse Management Suite” which can manage Wyse devices but also a ton of other devices!
Kaitai Struct: A Tool For Dealing With Binary Formats - Petr Pucil & Mikhail Yakshin
www.youtube.com ->
#hacklu2025
Original->
www.youtube.com ->
#hacklu2025
Original->
November 5, 2025 at 9:13 PM
Kaitai Struct: A Tool For Dealing With Binary Formats - Petr Pucil & Mikhail Yakshin
www.youtube.com ->
#hacklu2025
Original->
www.youtube.com ->
#hacklu2025
Original->
Did you know that the water level in Amsterdam is controlled by an automated flood gate system that reacts to canal-based sensor input. Amsterdam once almost partially drowned
Marina Bochenkova is saying very scarinteresting things at #hacklu2025 !!
Marina Bochenkova is saying very scarinteresting things at #hacklu2025 !!

October 21, 2025 at 12:43 PM
Did you know that the water level in Amsterdam is controlled by an automated flood gate system that reacts to canal-based sensor input. Amsterdam once almost partially drowned
Marina Bochenkova is saying very scarinteresting things at #hacklu2025 !!
Marina Bochenkova is saying very scarinteresting things at #hacklu2025 !!
Next up is @elyssaboulila presenting “Slipping through the cracks: How malicious emails evade detection”
Day 2 of #hacklu2025
Day 2 of #hacklu2025

October 22, 2025 at 8:56 AM
Next up is @elyssaboulila presenting “Slipping through the cracks: How malicious emails evade detection”
Day 2 of #hacklu2025
Day 2 of #hacklu2025
#hacklu2025 Remi and Pierre managed to build first a working RCE, and then a stealthy version of the same. They then demoed using the exploit on an OSS project that uses Livewire -> the Snipe-IT cmdb. Funnily I always followed Snipe on Twitter back before the exodus. @snipe ah maybe she IS here.
October 23, 2025 at 2:02 PM
#hacklu2025 Remi and Pierre managed to build first a working RCE, and then a stealthy version of the same. They then demoed using the exploit on an OSS project that uses Livewire -> the Snipe-IT cmdb. Funnily I always followed Snipe on Twitter back before the exodus. @snipe ah maybe she IS here.
Next up a team from #pwc is presenting an overview of the #bitlocker security landscape-> which attacks work, where, how, under which circumstances.
By Edouard D’hoedt and Hayk Gevorgyan
“Field guide to physical attacks against full-disk encryption” at #hacklu2025
By Edouard D’hoedt and Hayk Gevorgyan
“Field guide to physical attacks against full-disk encryption” at #hacklu2025


October 23, 2025 at 8:56 AM
Next up a team from #pwc is presenting an overview of the #bitlocker security landscape-> which attacks work, where, how, under which circumstances.
By Edouard D’hoedt and Hayk Gevorgyan
“Field guide to physical attacks against full-disk encryption” at #hacklu2025
By Edouard D’hoedt and Hayk Gevorgyan
“Field guide to physical attacks against full-disk encryption” at #hacklu2025
First up after the LTs: Revisiting Widewine L3: DRM as a playground for hackers with Felipe Custodio Romero!
#hacklu2025
#hacklu2025


October 23, 2025 at 12:40 PM
First up after the LTs: Revisiting Widewine L3: DRM as a playground for hackers with Felipe Custodio Romero!
#hacklu2025
#hacklu2025
Its now @Regit and Peter Manev presenting the detection and performance improvements released with the recent #suricata8 release
#hacklu2025
#hacklu2025



October 23, 2025 at 3:59 PM
Its now @Regit and Peter Manev presenting the detection and performance improvements released with the recent #suricata8 release
#hacklu2025
#hacklu2025
October 23, 2025 at 10:09 AM
So we’ve kicked off this year’s @hack_lu !
On stage is Walter Belgers with his opening keynote on the early days hacking scene, his time at university with the “Time Wasters”, finding Unix, the war between TCP/IP and other protocols for supremacy and much much more!
#hacklu #hacklu2025
On stage is Walter Belgers with his opening keynote on the early days hacking scene, his time at university with the “Time Wasters”, finding Unix, the war between TCP/IP and other protocols for supremacy and much much more!
#hacklu #hacklu2025

October 21, 2025 at 7:17 AM
So we’ve kicked off this year’s @hack_lu !
On stage is Walter Belgers with his opening keynote on the early days hacking scene, his time at university with the “Time Wasters”, finding Unix, the war between TCP/IP and other protocols for supremacy and much much more!
#hacklu #hacklu2025
On stage is Walter Belgers with his opening keynote on the early days hacking scene, his time at university with the “Time Wasters”, finding Unix, the war between TCP/IP and other protocols for supremacy and much much more!
#hacklu #hacklu2025
Lightning talks over. Went too fast, couldn’t toot, sorry folks. Watch the recordings from @ministraitor !!
They’ll be out imminently if not already
#hacklu2025
They’ll be out imminently if not already
#hacklu2025
October 22, 2025 at 12:24 PM
Lightning talks over. Went too fast, couldn’t toot, sorry folks. Watch the recordings from @ministraitor !!
They’ll be out imminently if not already
#hacklu2025
They’ll be out imminently if not already
#hacklu2025
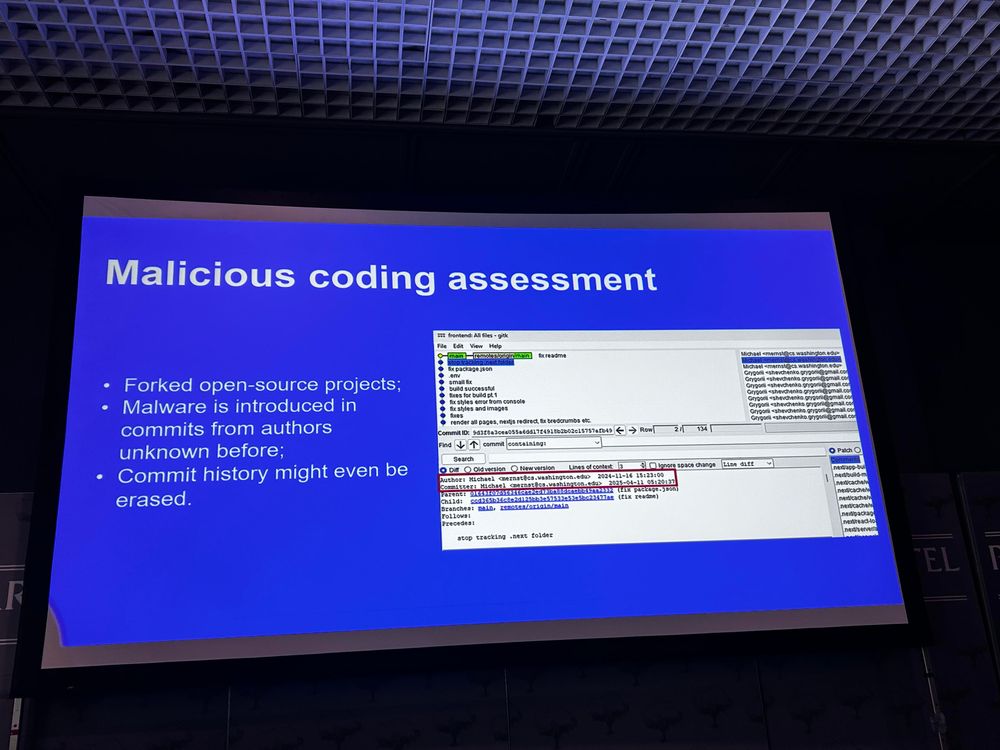
How to spot malicious software submitted as “job application code assessment examples” -> @ionutbaltariu is on stage at #hacklu2025 presenting “Fake jobs, real malware. Uncovering how cybercriminals are exploiting the job market”
October 21, 2025 at 1:00 PM
How to spot malicious software submitted as “job application code assessment examples” -> @ionutbaltariu is on stage at #hacklu2025 presenting “Fake jobs, real malware. Uncovering how cybercriminals are exploiting the job market”
On stage now is another set of repeat #hacklu speakers -> @ddu and @cvandeplas are on stage with “Building a pipeline to analyse iOS devices at scale”
#hacklu2025
#hacklu2025



October 23, 2025 at 10:07 AM
On stage now is another set of repeat #hacklu speakers -> @ddu and @cvandeplas are on stage with “Building a pipeline to analyse iOS devices at scale”
#hacklu2025
#hacklu2025
Next up is Will Moffat with “The S in IoT: Tales from inside the IoT industry”. A non-recorded presentation


October 22, 2025 at 2:06 PM
Next up is Will Moffat with “The S in IoT: Tales from inside the IoT industry”. A non-recorded presentation



October 23, 2025 at 6:11 AM
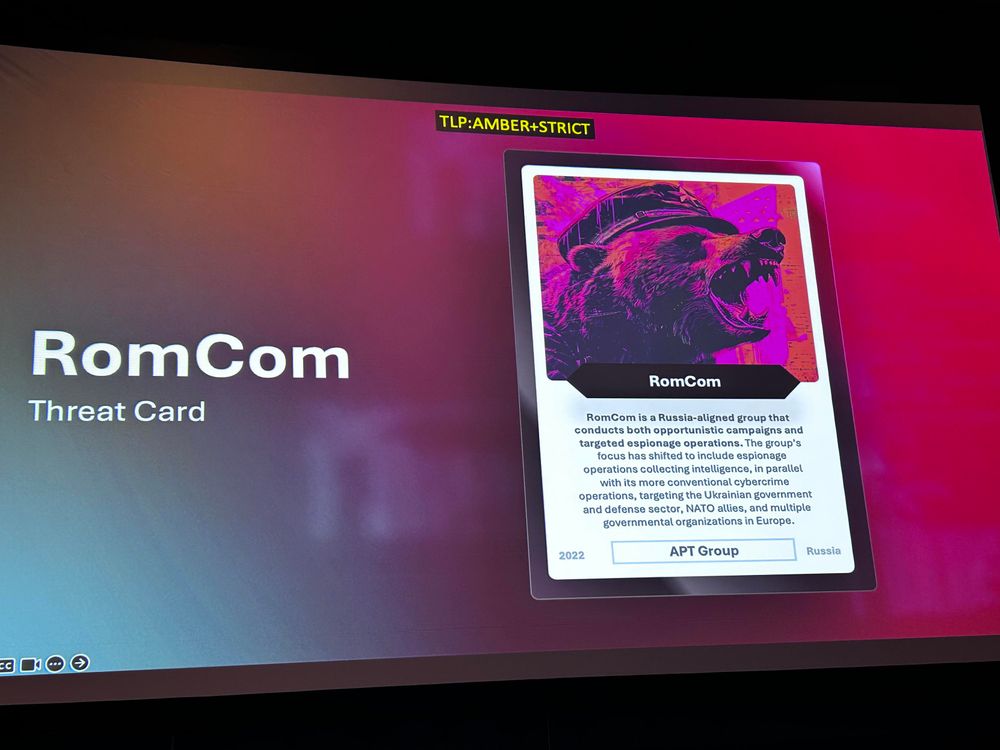
Second to last of #hacklu2025 day 1 is Damien Schaeffer of ESET talking about a Russian threat actor that ESET tracks as #romcom
This is a serious ATP that habitually uses 0days in their campaigns.
This is a serious ATP that habitually uses 0days in their campaigns.
October 21, 2025 at 4:06 PM
Second to last of #hacklu2025 day 1 is Damien Schaeffer of ESET talking about a Russian threat actor that ESET tracks as #romcom
This is a serious ATP that habitually uses 0days in their campaigns.
This is a serious ATP that habitually uses 0days in their campaigns.

