
The other side is at @a (photography, art and free software at large) […]
[bridged from https://infosec.exchange/@adulau on the fediverse by https://fed.brid.gy/ ]

It comes with detailed attributes such as manufacturer, cost, and technical specs.
You can now easily classify, model, and share […]
[Original post on infosec.exchange]


It comes with detailed attributes such as manufacturer, cost, and technical specs.
You can now easily classify, model, and share […]
[Original post on infosec.exchange]
The open source project providing real-time ransomware intelligence.
Thanks to @F_kZ_ for the incredible work.
#ransomware #threatintelligence #threatintel #opensource
🔗 https://www.ransomlook.io/

The open source project providing real-time ransomware intelligence.
Thanks to @F_kZ_ for the incredible work.
#ransomware #threatintelligence #threatintel #opensource
🔗 https://www.ransomlook.io/
is from Peter Gutmann in the cryptography mailing-list.
Given that after 20 years and hundreds of millions of dollars spent
researchers have yet to demonstrate a single legitimate […]
[Original post on infosec.exchange]

is from Peter Gutmann in the cryptography mailing-list.
Given that after 20 years and hundreds of millions of dollars spent
researchers have yet to demonstrate a single legitimate […]
[Original post on infosec.exchange]
[Original post on infosec.exchange]

[Original post on infosec.exchange]
🔗 […]
[Original post on infosec.exchange]

🔗 […]
[Original post on infosec.exchange]
We published all the materials from the workshop given at #hacklu 2025
#gcve #vulnerabilitymanagement #opensource #cybersecurity […]
[Original post on infosec.exchange]

We published all the materials from the workshop given at #hacklu 2025
#gcve #vulnerabilitymanagement #opensource #cybersecurity […]
[Original post on infosec.exchange]
If you need to document or describe or decode binary format, Kaitai is clearly there to help.
https://kaitai.io/ @kaitai
#hacklu #kaitai #dfir #cybersecurity
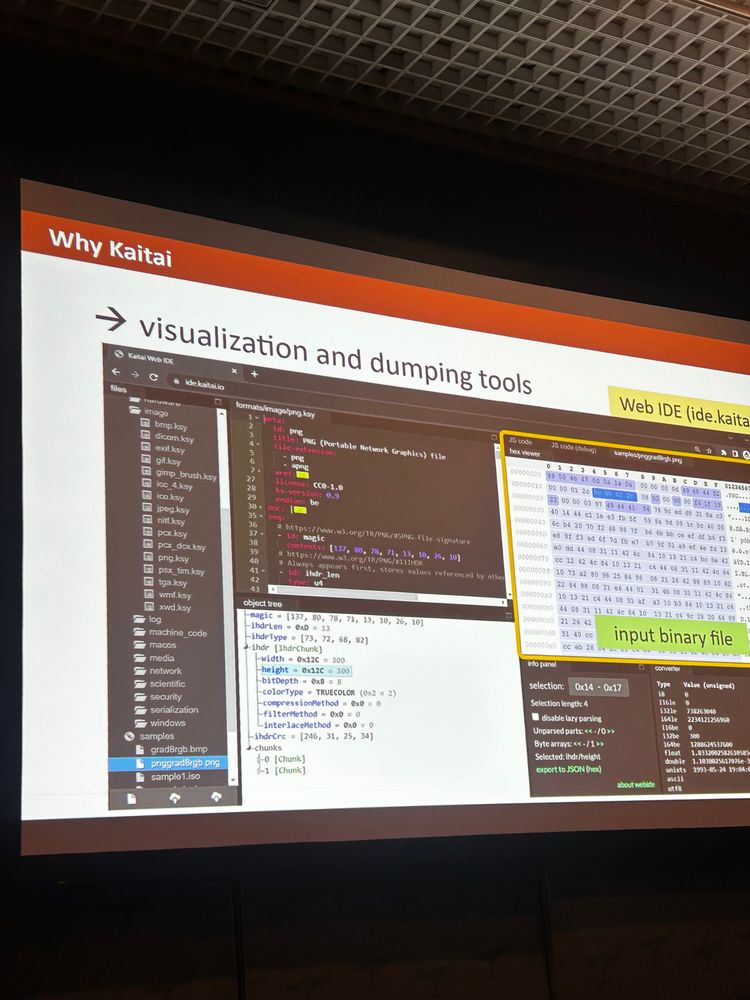
If you need to document or describe or decode binary format, Kaitai is clearly there to help.
https://kaitai.io/ @kaitai
#hacklu #kaitai #dfir #cybersecurity
[Original post on infosec.exchange]


[Original post on infosec.exchange]
The service is available both through a web interface and an API, allowing users to convert […]
[Original post on infosec.exchange]

The service is available both through a web interface and an API, allowing users to convert […]
[Original post on infosec.exchange]
https://arxiv.org/pdf/2509.17253
#car #safety #lidar

https://arxiv.org/pdf/2509.17253
#car #safety #lidar
[Original post on infosec.exchange]

[Original post on infosec.exchange]
[Original post on infosec.exchange]

[Original post on infosec.exchange]
[Original post on infosec.exchange]

[Original post on infosec.exchange]
The page was a bit dated, so it now has cleaner references, better structure, and direct links to practical models (including MISP taxonomies).
🔗 […]
[Original post on infosec.exchange]
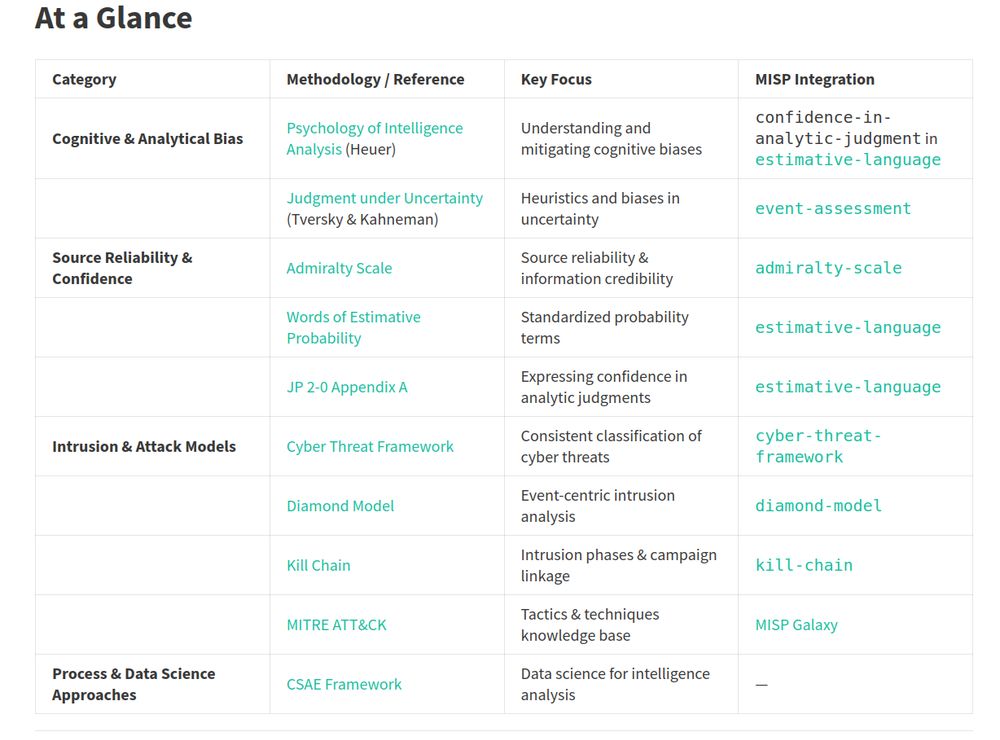
The page was a bit dated, so it now has cleaner references, better structure, and direct links to practical models (including MISP taxonomies).
🔗 […]
[Original post on infosec.exchange]
BCP Document https://gcve.eu/bcp/gcve-bcp-04/
PDF https://gcve.eu/files/bcp/gcve-bcp-04.pdf
Comments and feedback […]
[Original post on infosec.exchange]

BCP Document https://gcve.eu/bcp/gcve-bcp-04/
PDF https://gcve.eu/files/bcp/gcve-bcp-04.pdf
Comments and feedback […]
[Original post on infosec.exchange]
[Original post on infosec.exchange]
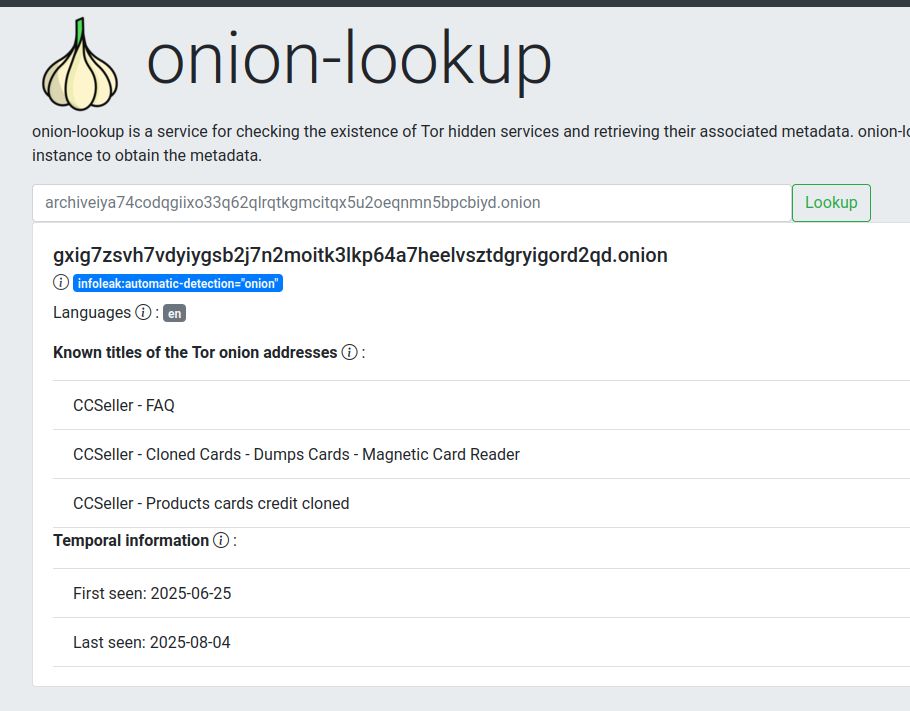
[Original post on infosec.exchange]
Thanks to @wendynather for the discovery.
#cybersecurity #vulnerability
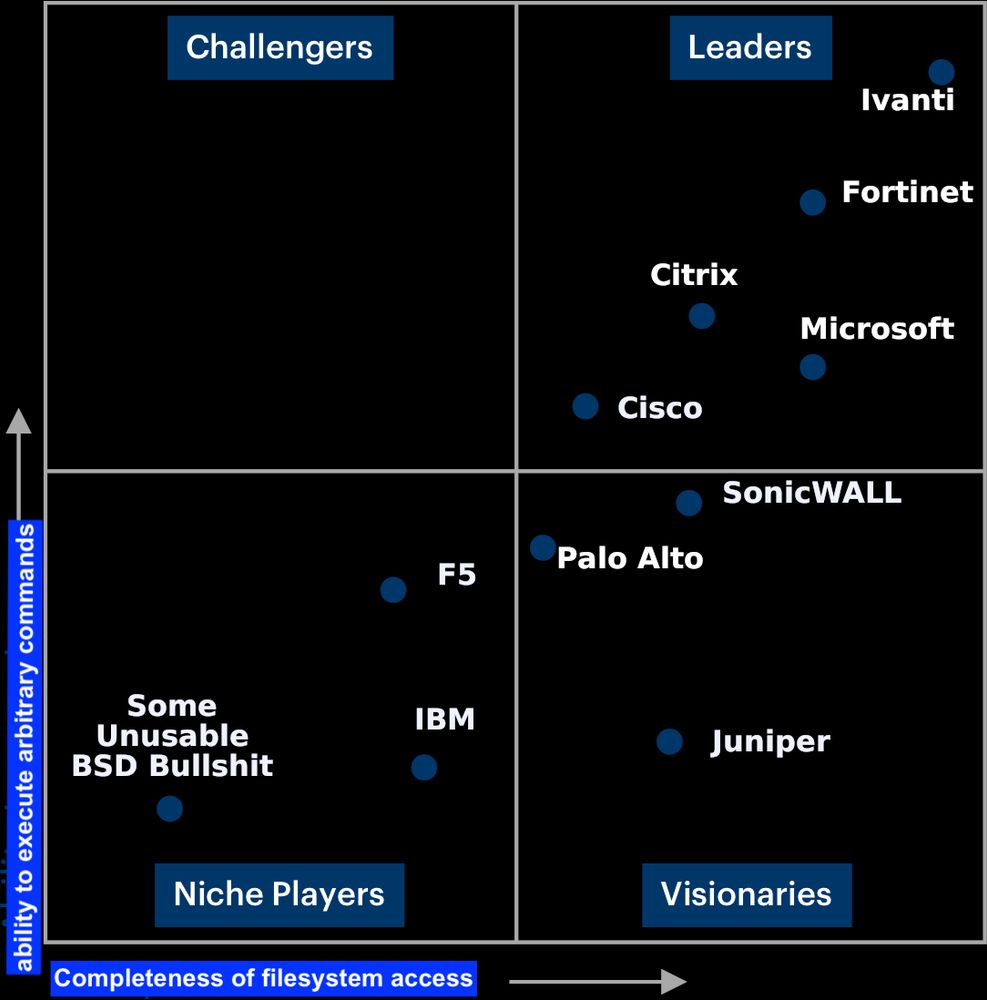
Thanks to @wendynather for the discovery.
#cybersecurity #vulnerability
It seems one of the Snowflake bridge is down (but should not impact obfs4):
https://gitlab.torproject.org/tpo/anti-censorship/pluggable-transports/snowflake/-/issues/40475
but from the number of relays […]
[Original post on infosec.exchange]
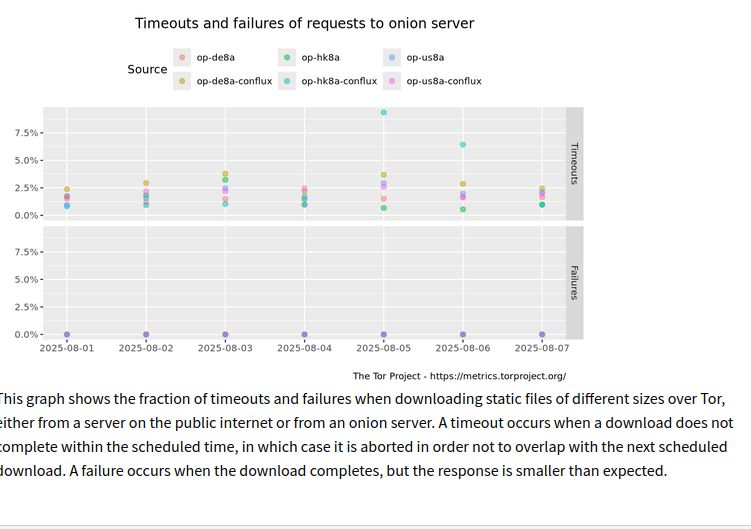
It seems one of the Snowflake bridge is down (but should not impact obfs4):
https://gitlab.torproject.org/tpo/anti-censorship/pluggable-transports/snowflake/-/issues/40475
but from the number of relays […]
[Original post on infosec.exchange]
[Original post on infosec.exchange]
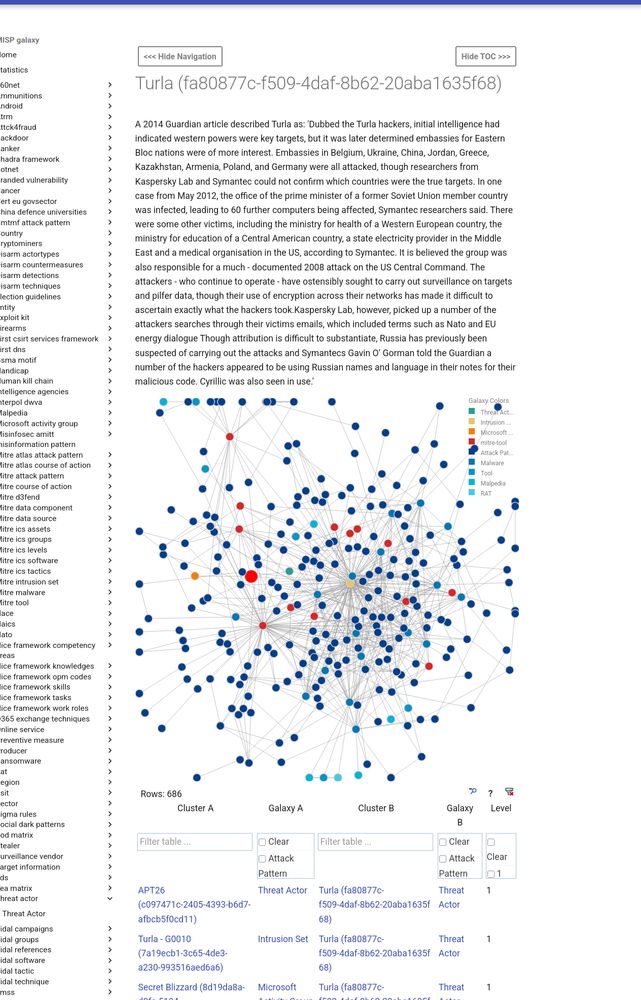
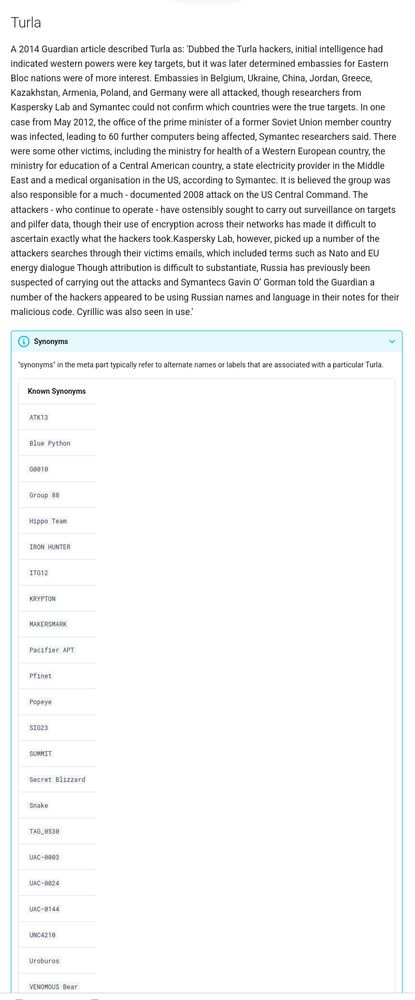
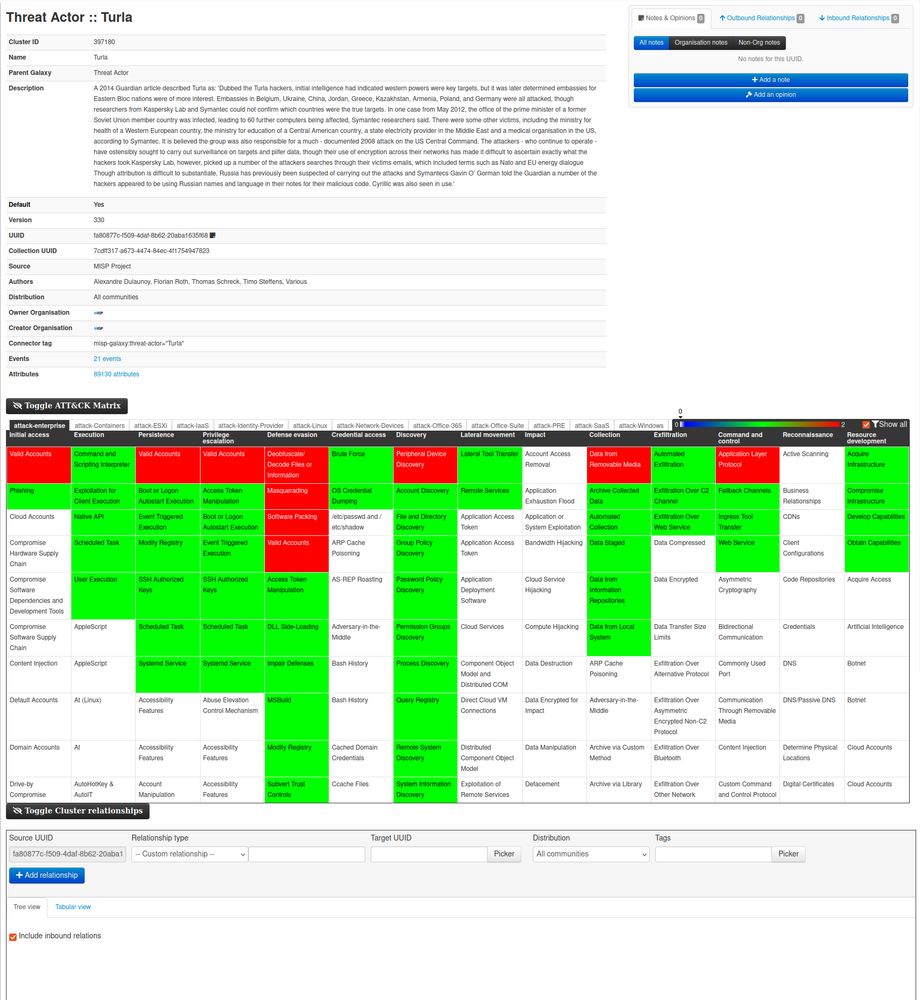
[Original post on infosec.exchange]
It’s clearly much more insightful than just having a bare ID marked as "rejected […]
[Original post on infosec.exchange]
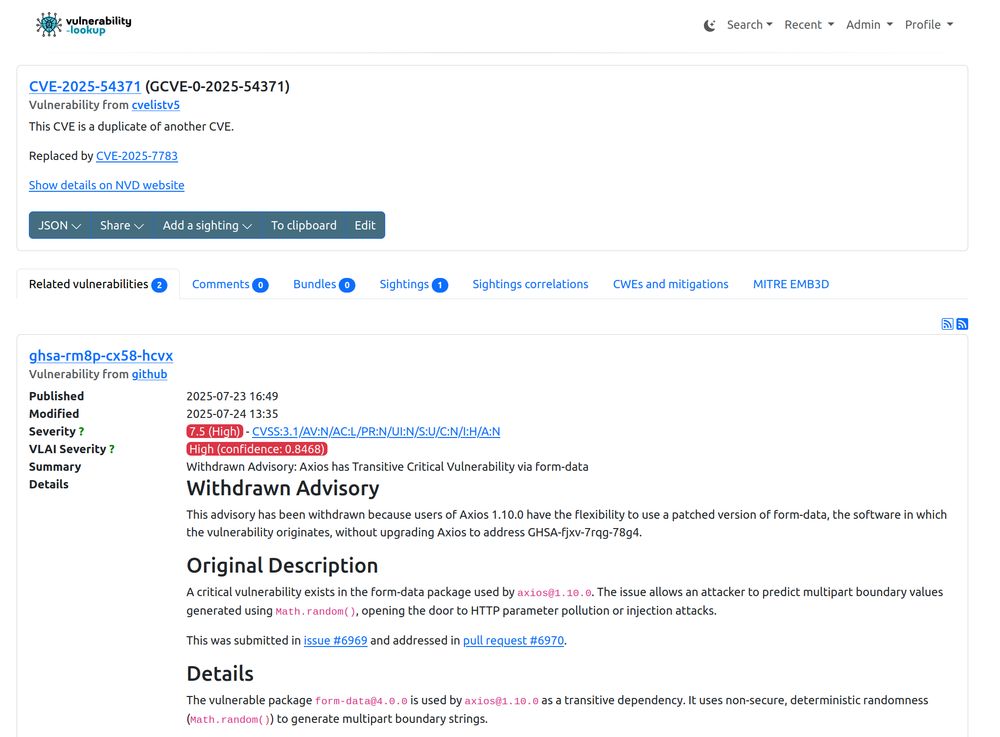
It’s clearly much more insightful than just having a bare ID marked as "rejected […]
[Original post on infosec.exchange]
CIRCL Open Source tools powering SOC & CSIRT teams.
#opensource #cybersecurity #soc #csirt #threatintel #threatintelligence
🔗 https://hdoc.cnw.circl.lu/JJKFoeHrS9Wf28L4tAyCNg?view#
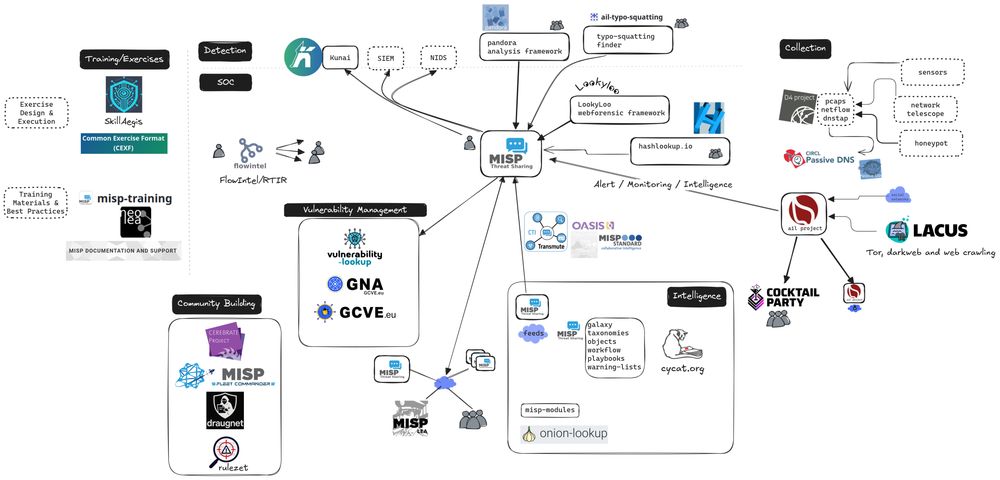
CIRCL Open Source tools powering SOC & CSIRT teams.
#opensource #cybersecurity #soc #csirt #threatintel #threatintelligence
🔗 https://hdoc.cnw.circl.lu/JJKFoeHrS9Wf28L4tAyCNg?view#




