
highlights a powerful new feature you might’ve missed: Cypher Selectors for Privilege Zones.
Why powerful? Unlike classic objectid selectors, Cypher selectors use complex conditions & can be created before the node exists.
🧵: 1/3

highlights a powerful new feature you might’ve missed: Cypher Selectors for Privilege Zones.
Why powerful? Unlike classic objectid selectors, Cypher selectors use complex conditions & can be created before the node exists.
🧵: 1/3




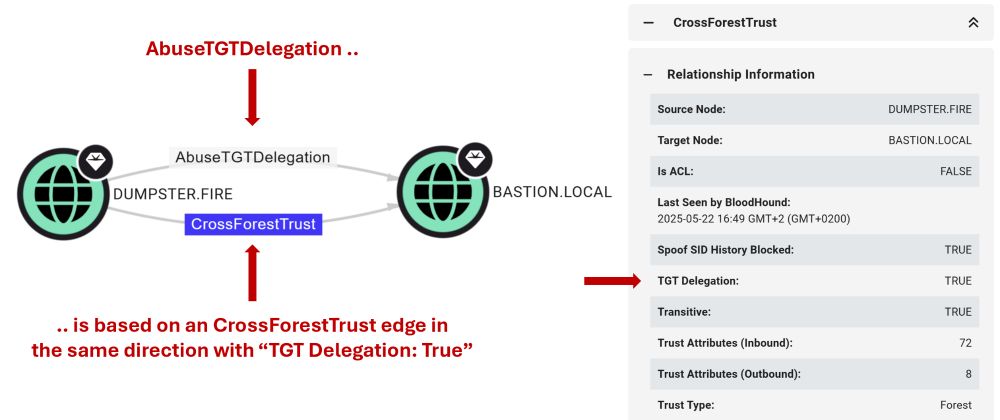
First dives into how we're improving the way BloodHound models attack paths through AD trusts: specterops.io/blog/2025/06...
Second covers an attack technique I came across while exploring AD trust abuse: specterops.io/blog/2025/06...
Hope you enjoy the read 🥳
First dives into how we're improving the way BloodHound models attack paths through AD trusts: specterops.io/blog/2025/06...
Second covers an attack technique I came across while exploring AD trust abuse: specterops.io/blog/2025/06...
Hope you enjoy the read 🥳

@atomicchonk.bsky.social digs into what happens if we employ this in adversarial text attacks against AI models.
Read more 👉 ghst.ly/4kW2D37

@atomicchonk.bsky.social digs into what happens if we employ this in adversarial text attacks against AI models.
Read more 👉 ghst.ly/4kW2D37
Alex Parrill & @printingprops.com discuss the new real-time collaborative editing for observations, findings, & report fields, enabling multiple users to edit simultaneously without overwriting each other. ghst.ly/4jVqdvG

Alex Parrill & @printingprops.com discuss the new real-time collaborative editing for observations, findings, & report fields, enabling multiple users to edit simultaneously without overwriting each other. ghst.ly/4jVqdvG
@xpnsec.com drops knowledge on LLM security w/ his latest post showing how attackers can by pass LLM WAFs by confusing the tokenization process to smuggle tokens to back-end LLMs.
Read more: ghst.ly/4koUJiz

@xpnsec.com drops knowledge on LLM security w/ his latest post showing how attackers can by pass LLM WAFs by confusing the tokenization process to smuggle tokens to back-end LLMs.
Read more: ghst.ly/4koUJiz
Register today! ➡️ ghst.ly/ntlm-web-bsky
Register today! ➡️ ghst.ly/ntlm-web-bsky
Relay attacks are more complicated than many people realize. Check out this deep dive from Elad Shamir on NTLM relay attacks & the new edges we recently added to BloodHound. ghst.ly/4lv3E31

Relay attacks are more complicated than many people realize. Check out this deep dive from Elad Shamir on NTLM relay attacks & the new edges we recently added to BloodHound. ghst.ly/4lv3E31
Read more 👉 ghst.ly/4iXFTyF
Read more 👉 ghst.ly/4iXFTyF
Register today! ➡️ ghst.ly/ntlm-web

Register today! ➡️ ghst.ly/ntlm-web
Grab your badge & t-shirt and join your fellow conference attendees for breakfast. Follow along here for today’s schedule of events & use our hashtag to share your own updates!
Grab your badge & t-shirt and join your fellow conference attendees for breakfast. Follow along here for today’s schedule of events & use our hashtag to share your own updates!
Read more: ghst.ly/3QORQdF
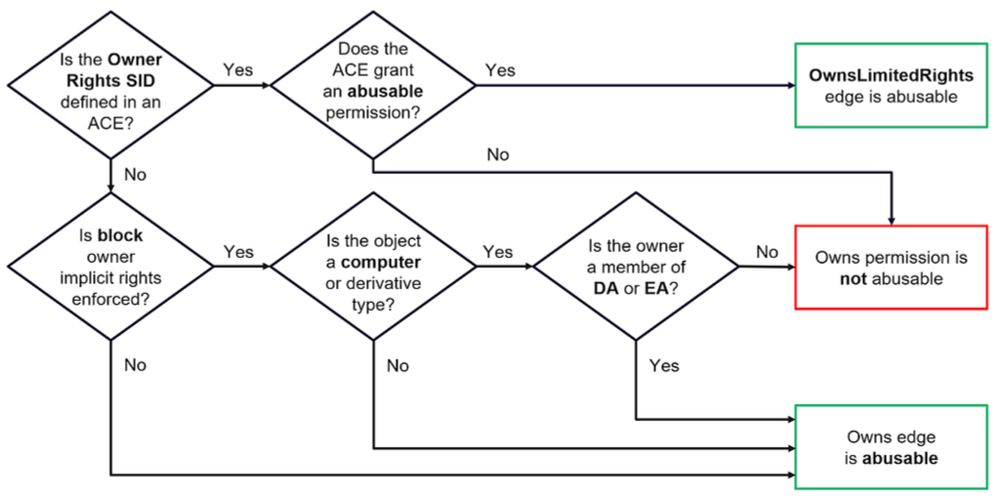
Read more: ghst.ly/3QORQdF
www.cobaltstrike.com/blog/update-...
LONG road. I partnered with Microsoft. 2018. I had TI process to track non-attrib CS servers. 2019. Fortra's novel lawfare. 2022
www.cobaltstrike.com/blog/update-...
LONG road. I partnered with Microsoft. 2018. I had TI process to track non-attrib CS servers. 2019. Fortra's novel lawfare. 2022
Check out our latest blog post from @unsignedsh0rt.bsky.social to learn more. ghst.ly/4buoISp
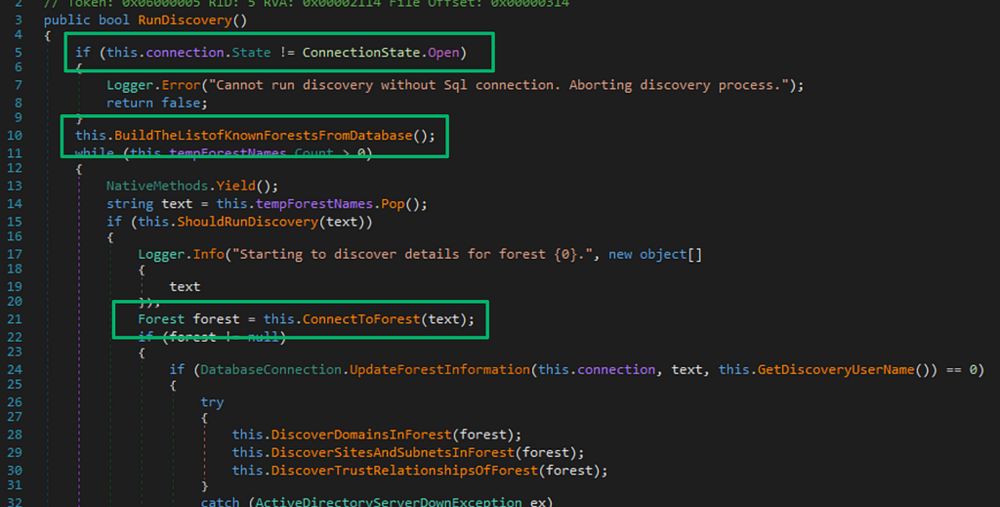
Check out our latest blog post from @unsignedsh0rt.bsky.social to learn more. ghst.ly/4buoISp
I had a series in mind like "Rubeus' Hidden Secrets" or something like that. Basically, highlighting features of the tool that seem less well known. I'm starting off with a basic one for getting crackable hashes from cached service tickets.
rastamouse.me/kerberoastin...

I had a series in mind like "Rubeus' Hidden Secrets" or something like that. Basically, highlighting features of the tool that seem less well known. I'm starting off with a basic one for getting crackable hashes from cached service tickets.
rastamouse.me/kerberoastin...



