
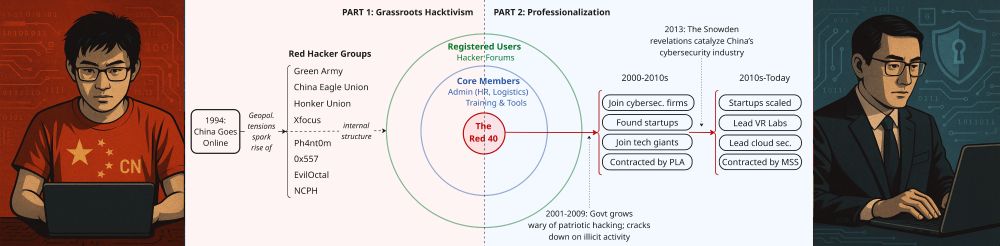
www.nattothoughts.com/p/the-tianfu...

www.nattothoughts.com/p/the-tianfu...
www.nattothoughts.com/p/provincial...

www.nattothoughts.com/p/provincial...
nattothoughts.substack.com/p/the-many-a...

nattothoughts.substack.com/p/the-many-a...
#Cybersecurity #TalentPipeline #CyberOperations
nattothoughts.substack.com/p/few-and-fa...

#Cybersecurity #TalentPipeline #CyberOperations
nattothoughts.substack.com/p/few-and-fa...
In this new piece for Natto,
@dakotaindc.bsky.social, @meidanowski.bsky.social & I dig into:
🏛️ China's vuln reporting rules
📉 Which firms joined/left MAPP since 2018
⚠️ The risks today’s members pose

In this new piece for Natto,
@dakotaindc.bsky.social, @meidanowski.bsky.social & I dig into:
🏛️ China's vuln reporting rules
📉 Which firms joined/left MAPP since 2018
⚠️ The risks today’s members pose




nattothoughts.substack.com/p/debating-c...
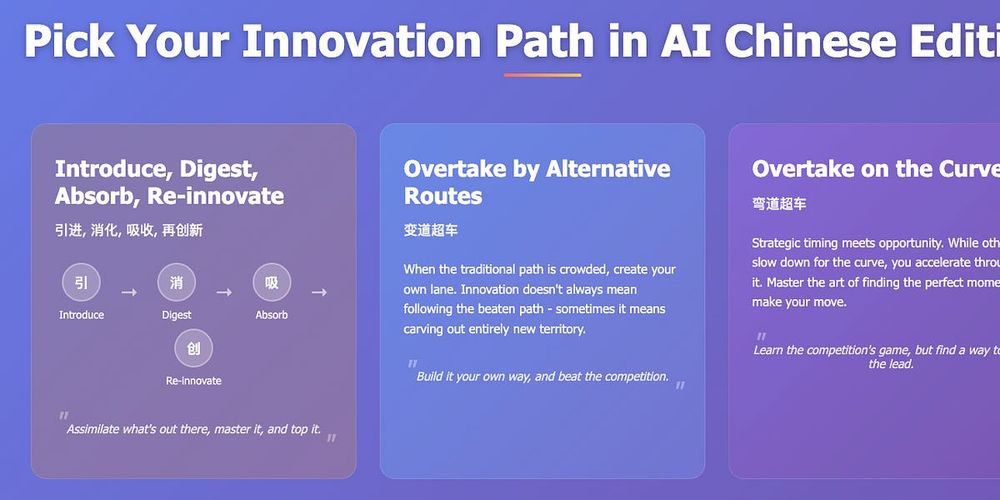
nattothoughts.substack.com/p/debating-c...
NEW Phenomenal report on Chinese civil military fusion and cyber militias by Kieran Green: margin.re/mobilizing-c...

NEW Phenomenal report on Chinese civil military fusion and cyber militias by Kieran Green: margin.re/mobilizing-c...
I gathered open source data & interviewed Gov employees, VR and china researchers to figure out what the zero day marketplace looks like in the U.S. and how it compares to China.
key findings below ⬇️- 0/🧵 www.atlanticcouncil.org/in-depth-res...
I gathered open source data & interviewed Gov employees, VR and china researchers to figure out what the zero day marketplace looks like in the U.S. and how it compares to China.
key findings below ⬇️- 0/🧵 www.atlanticcouncil.org/in-depth-res...
New piece for @nattothoughts.bsky.social
nattothoughts.substack.com/p/defense-th...

New piece for @nattothoughts.bsky.social
nattothoughts.substack.com/p/defense-th...
Thanks to @euben.bsky.social @dakotaindc.bsky.social Kristin Del Rosso for their previous research on the topic
nattothoughts.substack.com/p/when-a-voc...

Thanks to @euben.bsky.social @dakotaindc.bsky.social Kristin Del Rosso for their previous research on the topic
nattothoughts.substack.com/p/when-a-voc...
nattothoughts.substack.com/p/stories-of...

nattothoughts.substack.com/p/stories-of...

www.diplomatie.gouv.fr/fr/dossiers-...

www.diplomatie.gouv.fr/fr/dossiers-...

nattothoughts.substack.com/p/wars-witho...

nattothoughts.substack.com/p/wars-witho...
www.sentinelone.com/labs/labscon...
www.sentinelone.com/labs/labscon...

He's one of the most hardworking, dedicated and smart people I'm lucky enough to know, and he showed a LOT of courage when he fought back against attempts to undermine the 2020 election result
I hope Americans will stand behind him
He's one of the most hardworking, dedicated and smart people I'm lucky enough to know, and he showed a LOT of courage when he fought back against attempts to undermine the 2020 election result
I hope Americans will stand behind him

