https://www.nattothoughts.com/
www.nattothoughts.com/p/the-tianfu...

www.nattothoughts.com/p/the-tianfu...
www.nattothoughts.com/p/provincial...

www.nattothoughts.com/p/provincial...
nattothoughts.substack.com/p/chinas-202...

nattothoughts.substack.com/p/chinas-202...
nattothoughts.substack.com/p/a-look-bac...

nattothoughts.substack.com/p/a-look-bac...
nattothoughts.substack.com/p/the-many-a...

nattothoughts.substack.com/p/the-many-a...
nattothoughts.substack.com/p/knownsec-t...

nattothoughts.substack.com/p/knownsec-t...
nattothoughts.substack.com/p/chinas-cyb...

nattothoughts.substack.com/p/chinas-cyb...
New analysis from Natto Thoughts - how a single disclosure reshaped China’s approach to cybersecurity and control.
nattothoughts.substack.com/p/what-a-nar...

New analysis from Natto Thoughts - how a single disclosure reshaped China’s approach to cybersecurity and control.
nattothoughts.substack.com/p/what-a-nar...
nattothoughts.substack.com/p/beyond-the...

nattothoughts.substack.com/p/beyond-the...
A beacon of clarity? Or just more questions in the storm?
nattothoughts.substack.com/p/salt-typho...

A beacon of clarity? Or just more questions in the storm?
nattothoughts.substack.com/p/salt-typho...
#Cybersecurity #TalentPipeline #CyberOperations
nattothoughts.substack.com/p/few-and-fa...

#Cybersecurity #TalentPipeline #CyberOperations
nattothoughts.substack.com/p/few-and-fa...
In this new piece for Natto,
@dakotaindc.bsky.social, @meidanowski.bsky.social & I dig into:
🏛️ China's vuln reporting rules
📉 Which firms joined/left MAPP since 2018
⚠️ The risks today’s members pose

In this new piece for Natto,
@dakotaindc.bsky.social, @meidanowski.bsky.social & I dig into:
🏛️ China's vuln reporting rules
📉 Which firms joined/left MAPP since 2018
⚠️ The risks today’s members pose
nattothoughts.substack.com/p/hafnium-li...
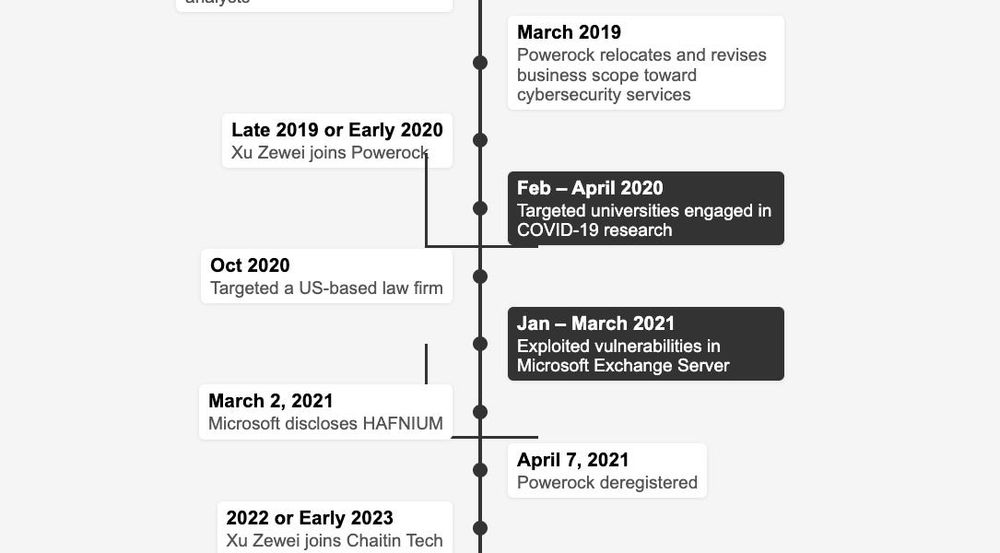
nattothoughts.substack.com/p/hafnium-li...
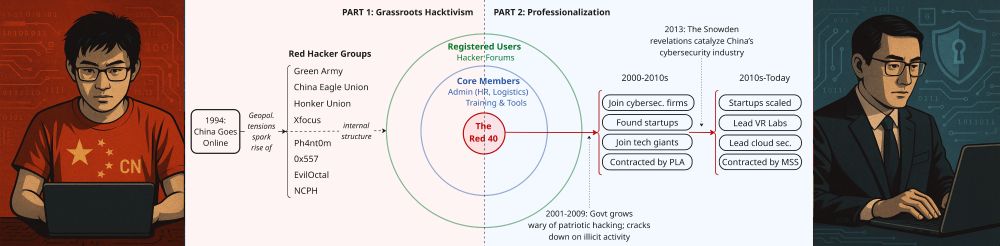
nattothoughts.substack.com/p/debating-c...
nattothoughts.substack.com/p/debating-c...
nattothoughts.substack.com/p/butian-vul...

nattothoughts.substack.com/p/butian-vul...
New piece for @nattothoughts.bsky.social
nattothoughts.substack.com/p/defense-th...

Thanks to @euben.bsky.social @dakotaindc.bsky.social Kristin Del Rosso for their previous research on the topic
nattothoughts.substack.com/p/when-a-voc...

Thanks to @euben.bsky.social @dakotaindc.bsky.social Kristin Del Rosso for their previous research on the topic
nattothoughts.substack.com/p/when-a-voc...
nattothoughts.substack.com/p/stories-of...

nattothoughts.substack.com/p/stories-of...
nattothoughts.substack.com/p/ransom-war...
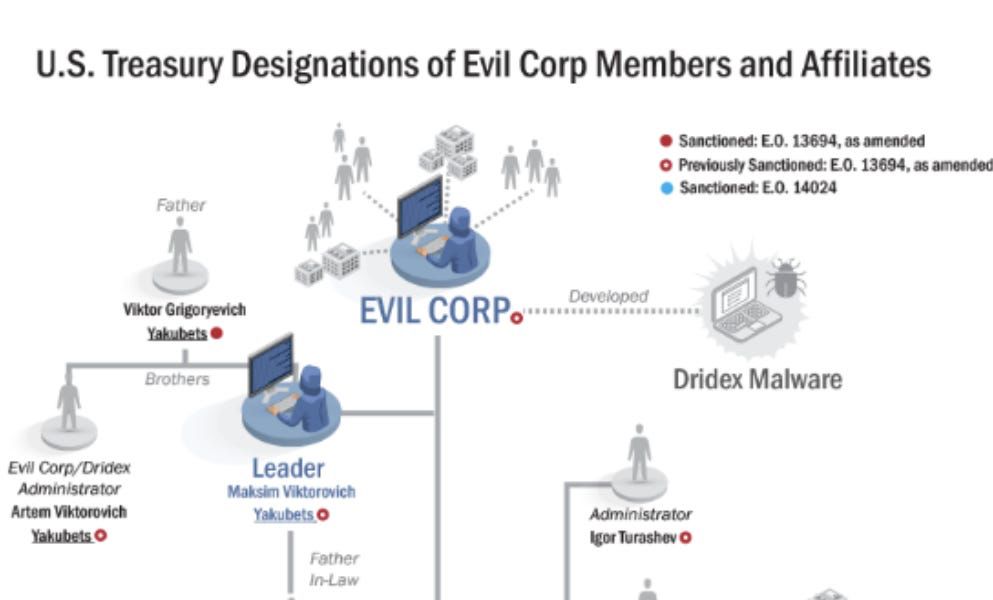
nattothoughts.substack.com/p/ransom-war...
nattothoughts.substack.com/p/wars-witho...

nattothoughts.substack.com/p/wars-witho...
nattothoughts.substack.com/p/indictment...
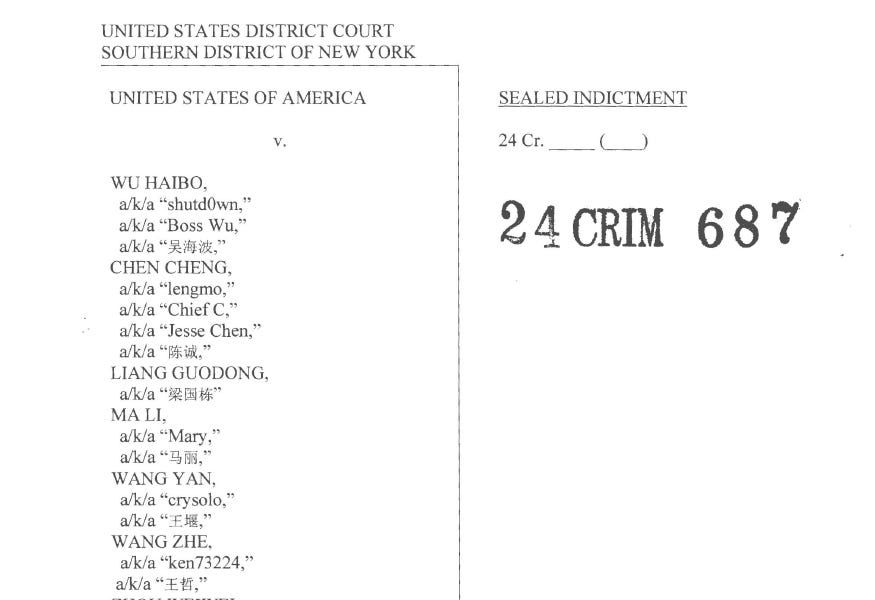
nattothoughts.substack.com/p/indictment...
nattothoughts.substack.com/p/zhou-shuai...
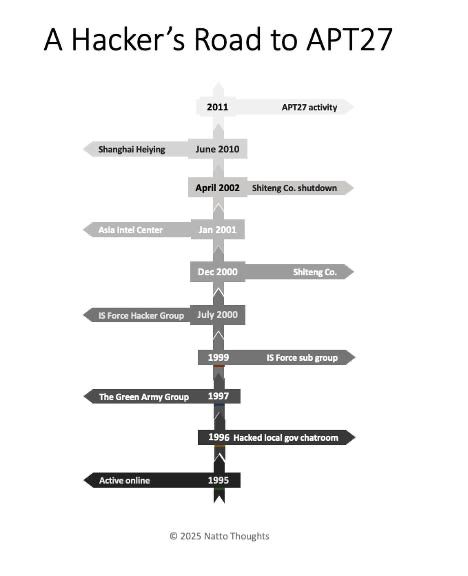
nattothoughts.substack.com/p/zhou-shuai...
nattothoughts.substack.com/p/where-is-i...

nattothoughts.substack.com/p/where-is-i...