
In this new piece for Natto,
@dakotaindc.bsky.social, @meidanowski.bsky.social & I dig into:
🏛️ China's vuln reporting rules
📉 Which firms joined/left MAPP since 2018
⚠️ The risks today’s members pose

In this new piece for Natto,
@dakotaindc.bsky.social, @meidanowski.bsky.social & I dig into:
🏛️ China's vuln reporting rules
📉 Which firms joined/left MAPP since 2018
⚠️ The risks today’s members pose


This part made me giggle: "This was the first hacker attack in my life, and my teacher was my own hormones."


This part made me giggle: "This was the first hacker attack in my life, and my teacher was my own hormones."
("Same Same, but Different" by @winnona.bsky.social)
5/6

("Same Same, but Different" by @winnona.bsky.social)
5/6
2/6

2/6
"by harnessing hacking contest vulnerabilities for strategic use by security agencies*"
There, fixed it for them.
Analyses backing this up 👇 (1/6)
(Source: www.newsweek.com/us-indicts-h...)

"by harnessing hacking contest vulnerabilities for strategic use by security agencies*"
There, fixed it for them.
Analyses backing this up 👇 (1/6)
(Source: www.newsweek.com/us-indicts-h...)

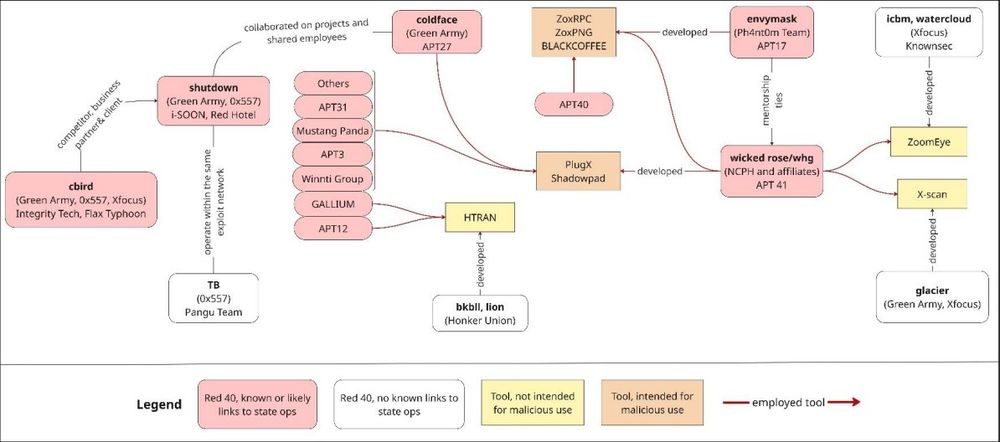
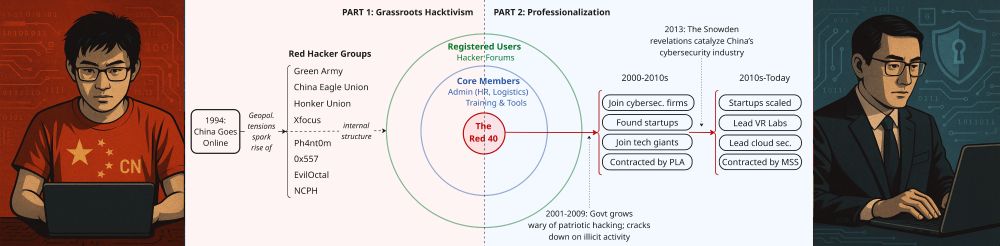
This graph shows my understanding of it.
Insights in short thread: threadreaderapp.com/thread/17964...
Full Report: shorturl.at/WsjFa

This graph shows my understanding of it.
Insights in short thread: threadreaderapp.com/thread/17964...
Full Report: shorturl.at/WsjFa


