

- automatic OEP finding, reconstructing IAT, avoiding antidebugs and fixing imports broken by shims
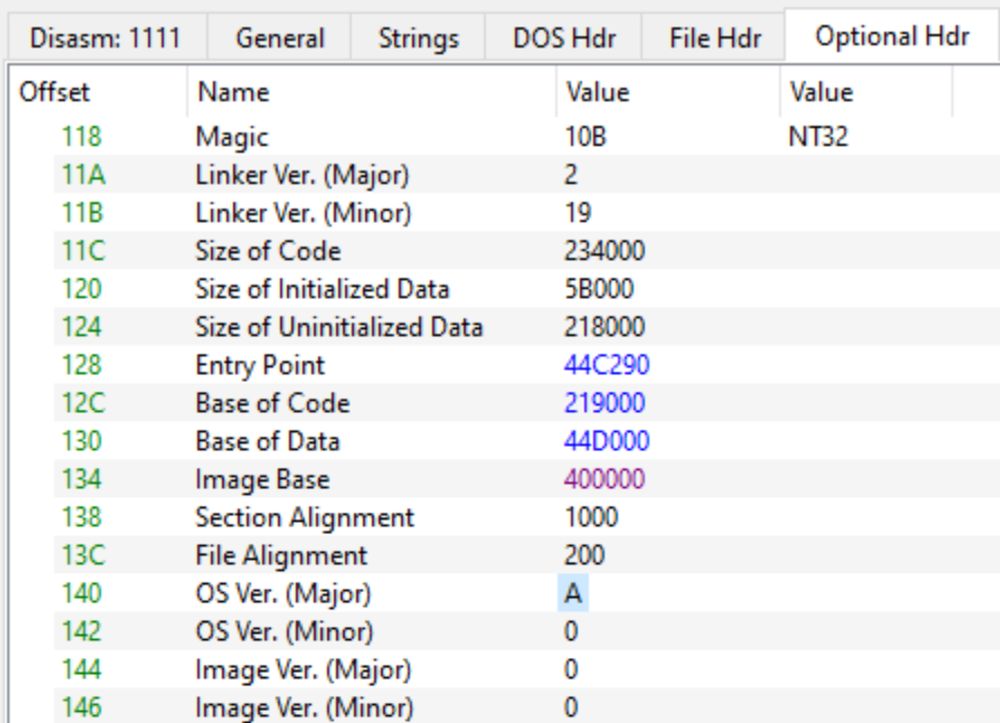
- automatic OEP finding, reconstructing IAT, avoiding antidebugs and fixing imports broken by shims
PDFs support Javascript, so Emscripten is used to compile the TinyEMU emulator to asm.js, which runs in the PDF. It boots in about 30 seconds and emulates a riscv32 buildroot system.
linux.doompdf.dev/linux.pdf
github.com/ading2210/li...
PDFs support Javascript, so Emscripten is used to compile the TinyEMU emulator to asm.js, which runs in the PDF. It boots in about 30 seconds and emulates a riscv32 buildroot system.
linux.doompdf.dev/linux.pdf
github.com/ading2210/li...

googleprojectzero.blogspot.com/2024/12/qual...
googleprojectzero.blogspot.com/2024/12/qual...
We are now targeting an end of January release.
If you have any Linux/ELF related research, projects, or papers, we would love to publish them!
Huge thank you to everyone who has already submitted!
tmpout.sh/blog/vol4-cf...
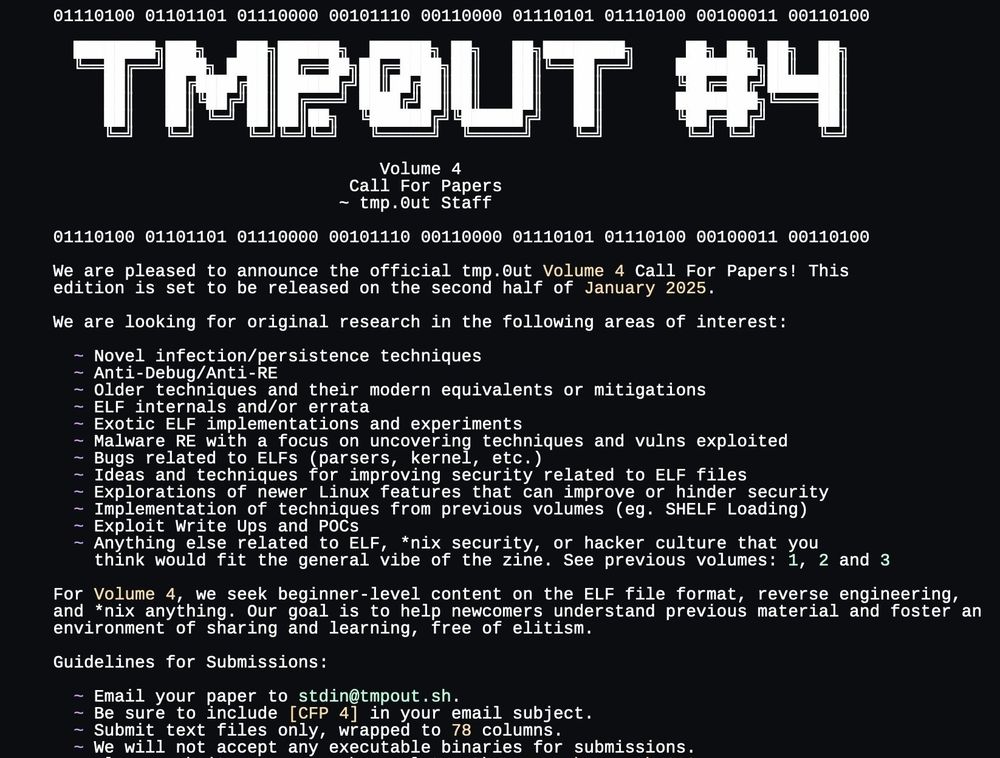
We are now targeting an end of January release.
If you have any Linux/ELF related research, projects, or papers, we would love to publish them!
Huge thank you to everyone who has already submitted!
tmpout.sh/blog/vol4-cf...
Even if you have the SeLoadPrivilege you would still require the Admin group to write the required regkey.
Some more technical details below 👇
Even if you have the SeLoadPrivilege you would still require the Admin group to write the required regkey.
Some more technical details below 👇
Hopefully, this should provide a better understanding of the whole "PrintNightmare" situation to both defenders and red teamers. 🤞
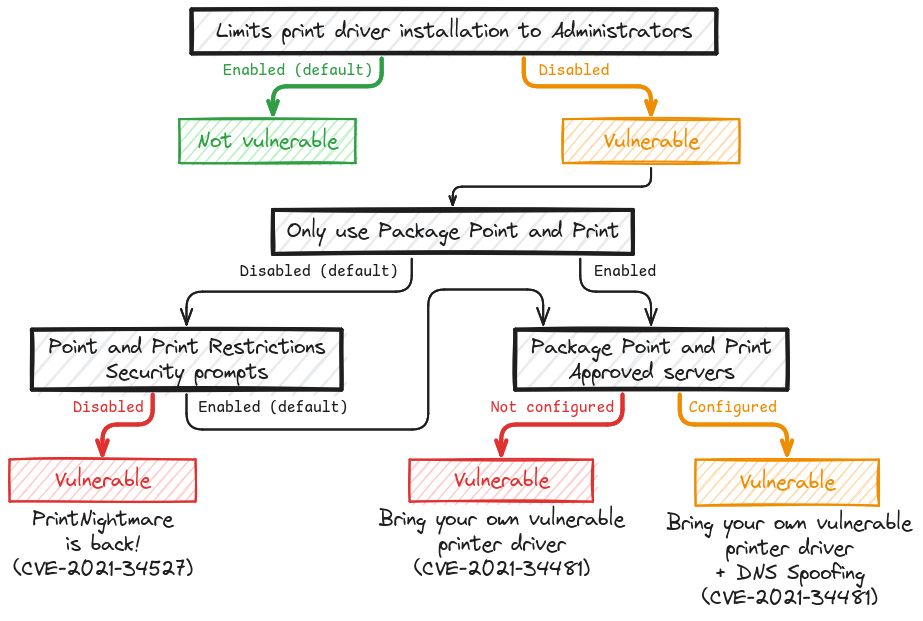
Hopefully, this should provide a better understanding of the whole "PrintNightmare" situation to both defenders and red teamers. 🤞
This post summarises how to tie Cobalt Strike's UDRL, SleepMask, and BeaconGate together for your syscall and call stack spoofing needs.
rastamouse.me/udrl-sleepma...

This post summarises how to tie Cobalt Strike's UDRL, SleepMask, and BeaconGate together for your syscall and call stack spoofing needs.
rastamouse.me/udrl-sleepma...
youtu.be/JERBqoTllaE?...

youtu.be/JERBqoTllaE?...









