therecord.media/ukraine-clai...

therecord.media/ukraine-clai...
www.recordedfuture.com/research/rus...

www.recordedfuture.com/research/rus...

🇫🇮🚢
The captain of a Russia-linked oil tanker that damaged five subsea cables in the Baltic Sea on Christmas Day was instructed by his shipping company to destroy evidence after the ship was seized by Finnish authorities, according to a wiretap transcript.

🇫🇮🚢
The captain of a Russia-linked oil tanker that damaged five subsea cables in the Baltic Sea on Christmas Day was instructed by his shipping company to destroy evidence after the ship was seized by Finnish authorities, according to a wiretap transcript.


Had to sneak in the UNK_RemoteRogue RDP shenanigans as well - a thus far unattributed group we assess to be Russia-aligned, using a pretty fun set of email tactics

Had to sneak in the UNK_RemoteRogue RDP shenanigans as well - a thus far unattributed group we assess to be Russia-aligned, using a pretty fun set of email tactics
Check your Compromised Website Report for critical events tagged “fortinet-compromised” and follow Fortinet's mitigation advice on compromised devices:
fortinet.com/blog/psirt-b...
Data available from 2025-04-11+
shadowserver.org/what-we-do/n...
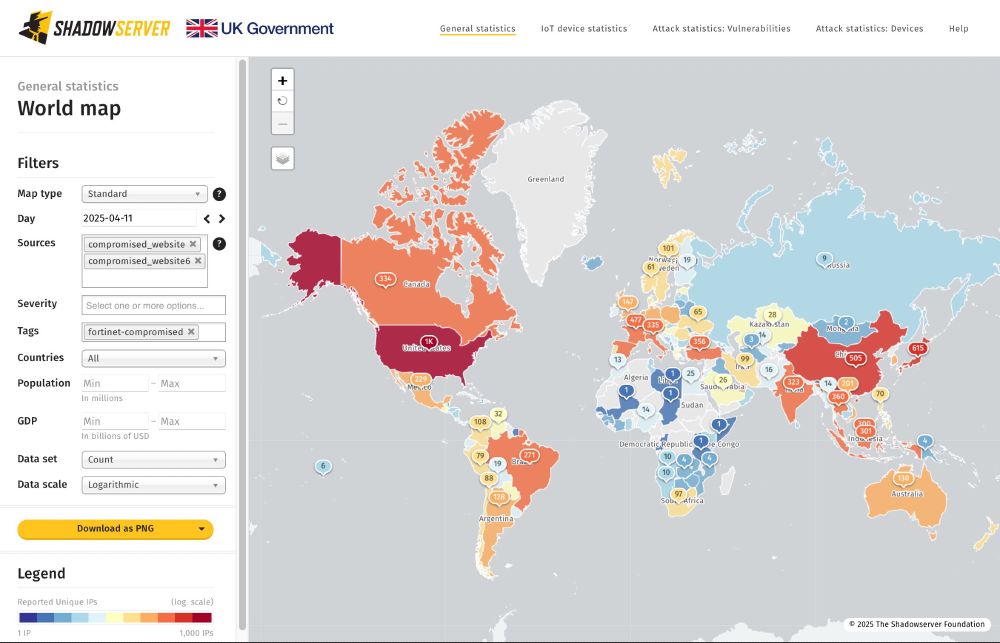
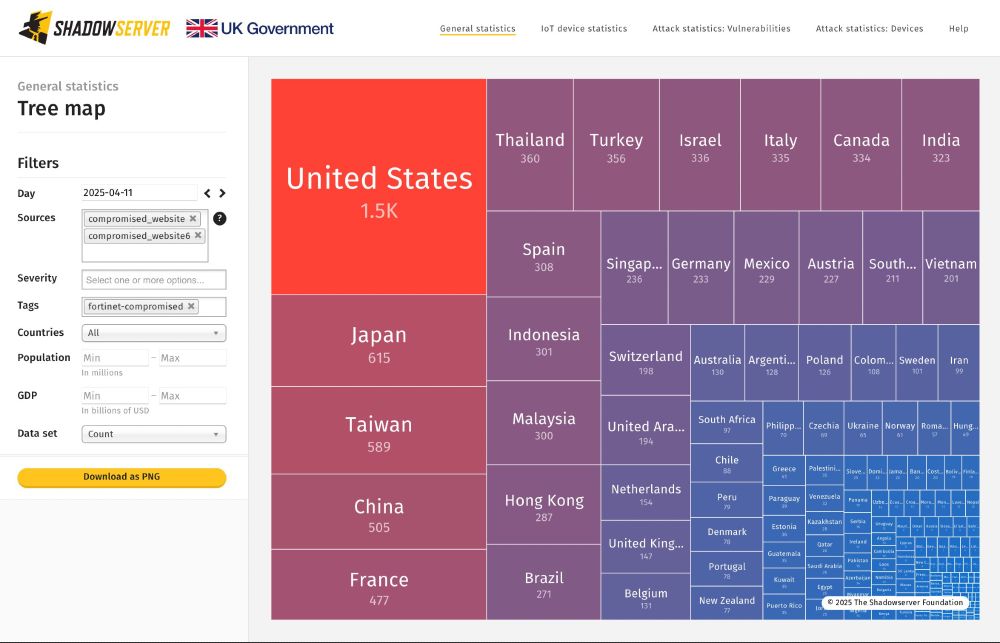
Check your Compromised Website Report for critical events tagged “fortinet-compromised” and follow Fortinet's mitigation advice on compromised devices:
fortinet.com/blog/psirt-b...
Data available from 2025-04-11+
shadowserver.org/what-we-do/n...
snoop.ro/pe-urmele-ba...
snoop.ro/pe-urmele-ba...
Blog: www.recordedfuture.com/research/202... (1/10)
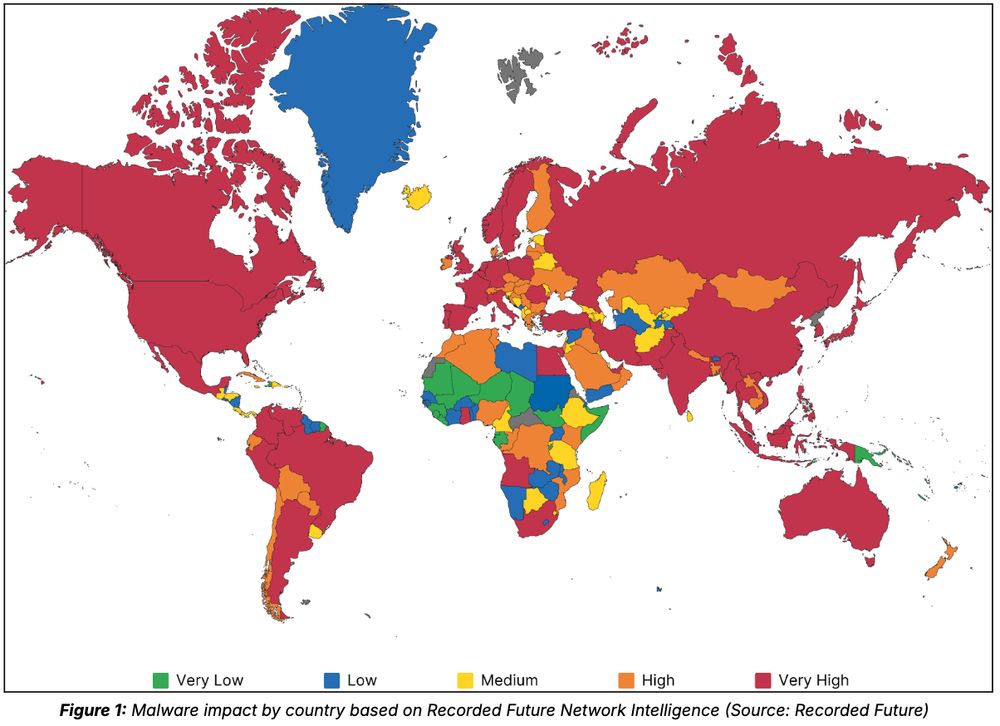
Blog: www.recordedfuture.com/research/202... (1/10)
#dfir #threatintel #m365security
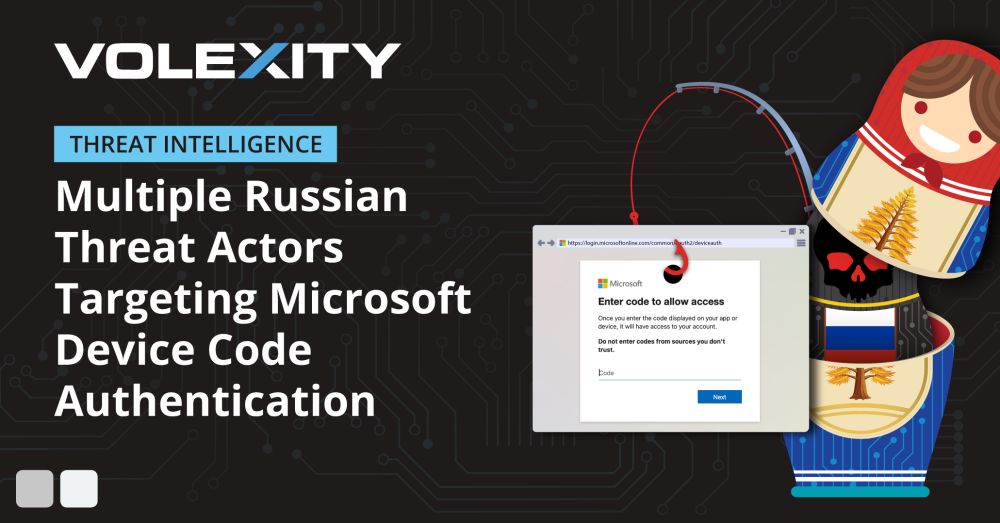
#dfir #threatintel #m365security
www.recordedfuture.com/research/red...
www.recordedfuture.com/research/red...
https://buff.ly/4gukMSN
🗓️ Thursday at 2pm CST

https://buff.ly/4gukMSN
🗓️ Thursday at 2pm CST
kyivindependent.com/ukraine-cons...

kyivindependent.com/ukraine-cons...
This research examines the operations of Crazy Evil — a Russian-speaking “traffer team” and cryptoscam gang — which has victimized thousands of people with infostealer malware.
Blog: www.recordedfuture.com/research/cra...
PDF: go.recordedfuture.com/hubfs/report...

This research examines the operations of Crazy Evil — a Russian-speaking “traffer team” and cryptoscam gang — which has victimized thousands of people with infostealer malware.
Blog: www.recordedfuture.com/research/cra...
PDF: go.recordedfuture.com/hubfs/report...
blog.bushidotoken.net/2025/01/trac...

blog.bushidotoken.net/2025/01/trac...

This research examines the global proliferation of Russian surveillance technologies, their use by repressive governments, and possible data-sharing with Russian intelligence.
Blog: www.recordedfuture.com/research/tra...
PDF: go.recordedfuture.com/hubfs/report...

This research examines the global proliferation of Russian surveillance technologies, their use by repressive governments, and possible data-sharing with Russian intelligence.
Blog: www.recordedfuture.com/research/tra...
PDF: go.recordedfuture.com/hubfs/report...
www.cybercrimediaries.com/post/russia-...

www.cybercrimediaries.com/post/russia-...
This research examines the role of Chinese international communication centers (ICCs) in amplifying propaganda via inauthentic social media activity, foreign influencers, and more.
Blog: www.recordedfuture.com/research/bre...
PDF: go.recordedfuture.com/hubfs/report...
This research examines the role of Chinese international communication centers (ICCs) in amplifying propaganda via inauthentic social media activity, foreign influencers, and more.
Blog: www.recordedfuture.com/research/bre...
PDF: go.recordedfuture.com/hubfs/report...