https://github.com/werdhaihai
@werdhaihai.bsky.social just dropped research on a new lateral movement technique using Windows Installer Custom Action Server, complete with working BOF code. ghst.ly/4pN03PG

@werdhaihai.bsky.social just dropped research on a new lateral movement technique using Windows Installer Custom Action Server, complete with working BOF code. ghst.ly/4pN03PG
specterops.io/blog/2025/07...

specterops.io/blog/2025/07...
@hotnops.bsky.social explores cross-domain compromise tradecraft within the same tenant.
Read more: ghst.ly/3ISMGN9

@hotnops.bsky.social explores cross-domain compromise tradecraft within the same tenant.
Read more: ghst.ly/3ISMGN9
First dives into how we're improving the way BloodHound models attack paths through AD trusts: specterops.io/blog/2025/06...
Second covers an attack technique I came across while exploring AD trust abuse: specterops.io/blog/2025/06...
Hope you enjoy the read 🥳
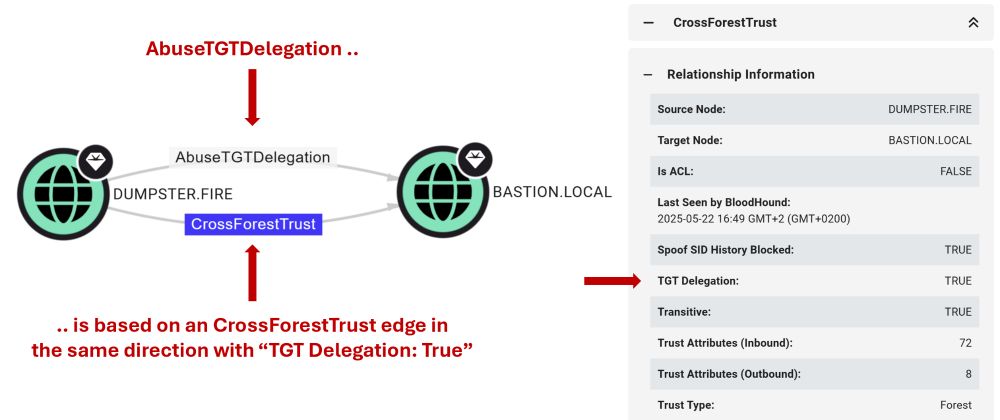
First dives into how we're improving the way BloodHound models attack paths through AD trusts: specterops.io/blog/2025/06...
Second covers an attack technique I came across while exploring AD trust abuse: specterops.io/blog/2025/06...
Hope you enjoy the read 🥳
Relay attacks are more complicated than many people realize. Check out this deep dive from Elad Shamir on NTLM relay attacks & the new edges we recently added to BloodHound. ghst.ly/4lv3E31

Relay attacks are more complicated than many people realize. Check out this deep dive from Elad Shamir on NTLM relay attacks & the new edges we recently added to BloodHound. ghst.ly/4lv3E31
medium.com/specter-ops-...

medium.com/specter-ops-...

x.com/0xC0rnbread/...

x.com/0xC0rnbread/...
Check out our latest blog post from @unsignedsh0rt.bsky.social to learn more. ghst.ly/4buoISp
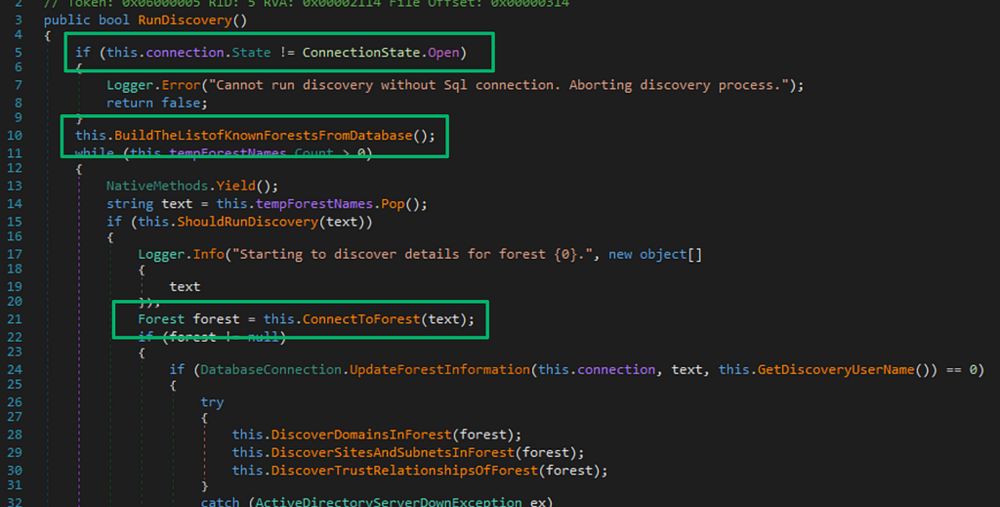
Check out our latest blog post from @unsignedsh0rt.bsky.social to learn more. ghst.ly/4buoISp
#IdentitySecurity #CyberSecurity
(1/6)

#IdentitySecurity #CyberSecurity
(1/6)
We're starting off with default support for Apollo and Athena. Check it out! :)

We're starting off with default support for Apollo and Athena. Check it out! :)
posts.specterops.io/entra-connec...

posts.specterops.io/entra-connec...

We are accepting talks focused on identity-based security and Attack Paths. Submit yours today!
➡️ ghst.ly/cfp-socon25

We are accepting talks focused on identity-based security and Attack Paths. Submit yours today!
➡️ ghst.ly/cfp-socon25




