
Cloud security research

Valdemar Carøe drops info on Certify 2.0, including a suite of new capabilities and refined usability improvements. ghst.ly/45IrBxI

Valdemar Carøe drops info on Certify 2.0, including a suite of new capabilities and refined usability improvements. ghst.ly/45IrBxI
Meet DeepPass2, our new secret scanning tool that goes beyond structured tokens to catch those tricky free-form passwords too. Read Neeraj Gupta's blog post for more. ghst.ly/40HLNNA
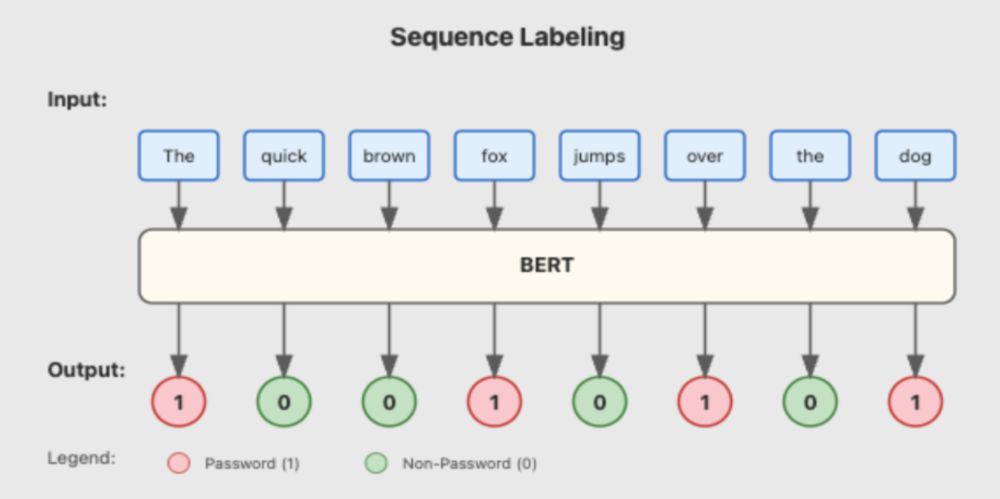
Meet DeepPass2, our new secret scanning tool that goes beyond structured tokens to catch those tricky free-form passwords too. Read Neeraj Gupta's blog post for more. ghst.ly/40HLNNA
specterops.io/blog/2025/07...
specterops.io/blog/2025/07...
specterops.io/blog/2025/07...

specterops.io/blog/2025/07...
github.com/SadProcessor...

github.com/SadProcessor...
They've also added some great guidance on suppressing the camera permission prompt for iOS :)
learn.microsoft.com/...
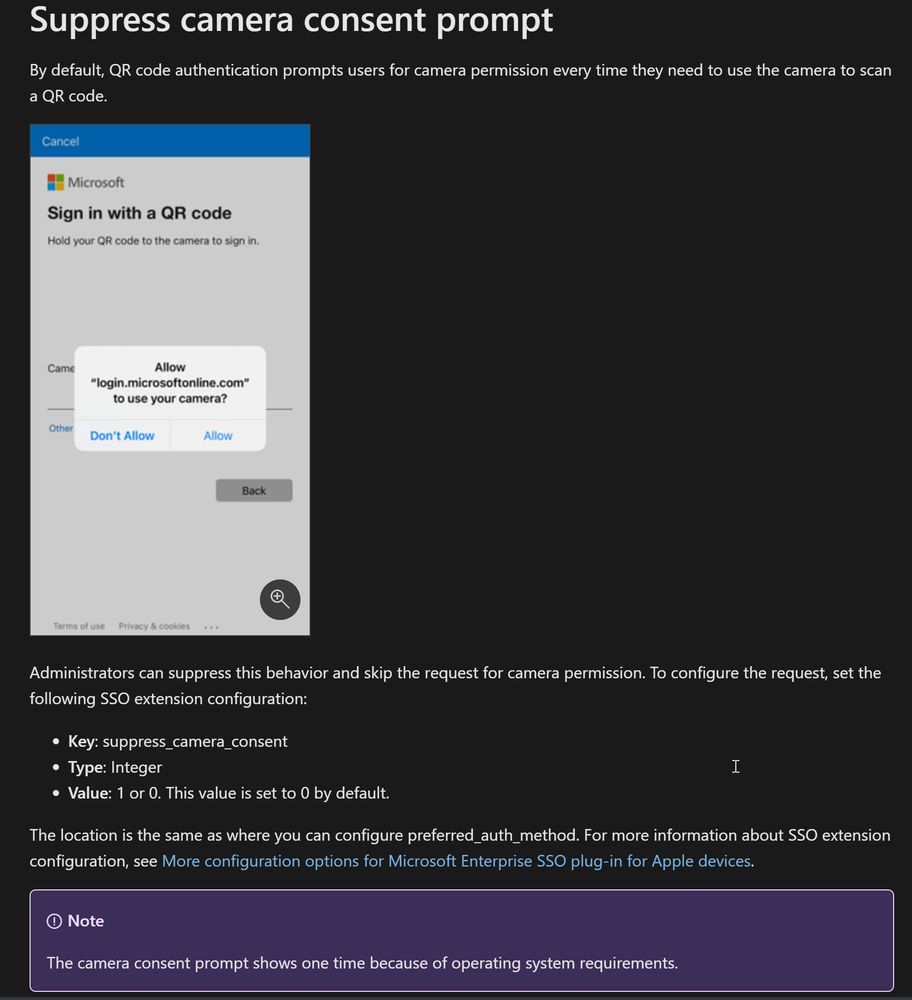
They've also added some great guidance on suppressing the camera permission prompt for iOS :)
learn.microsoft.com/...
support.microsoft.com/en-us/topic/...
support.microsoft.com/en-us/topic/...
First dives into how we're improving the way BloodHound models attack paths through AD trusts: specterops.io/blog/2025/06...
Second covers an attack technique I came across while exploring AD trust abuse: specterops.io/blog/2025/06...
Hope you enjoy the read 🥳
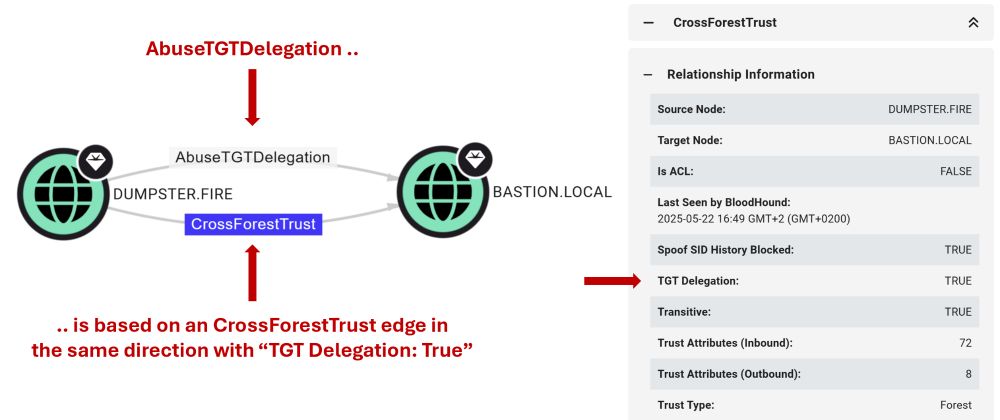
First dives into how we're improving the way BloodHound models attack paths through AD trusts: specterops.io/blog/2025/06...
Second covers an attack technique I came across while exploring AD trust abuse: specterops.io/blog/2025/06...
Hope you enjoy the read 🥳
@xpnsec.com covers the architecture, access controls, and why some legacy UAC bypass techniques remain effective in his latest blog post. ghst.ly/44mw5JM

posts.specterops.io/update-dumpi...

posts.specterops.io/update-dumpi...
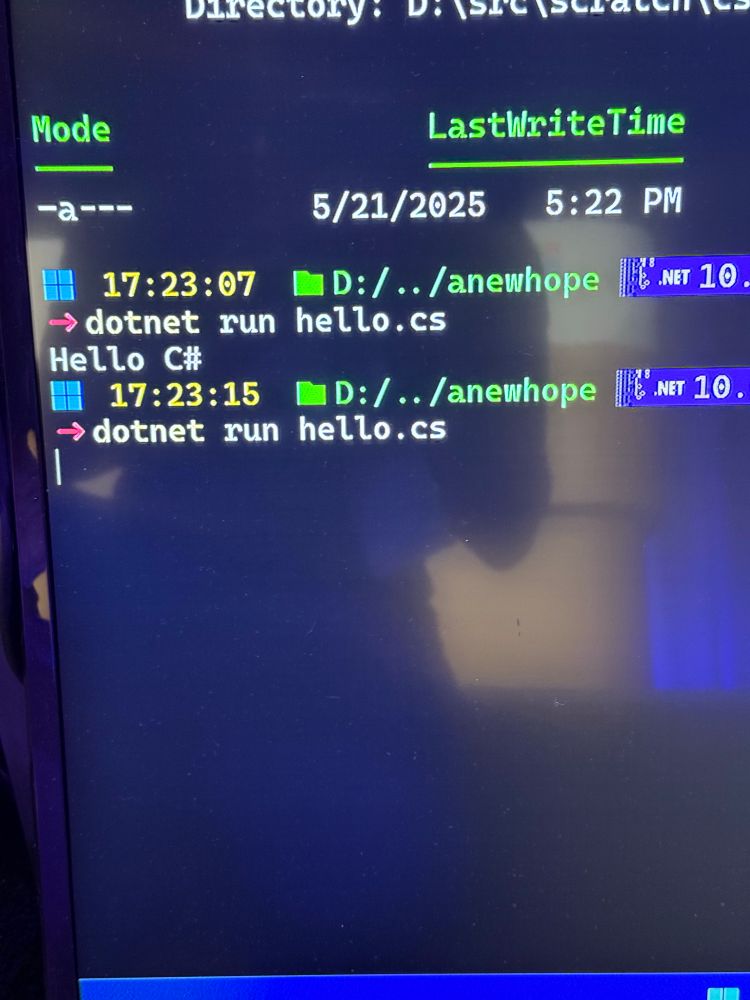
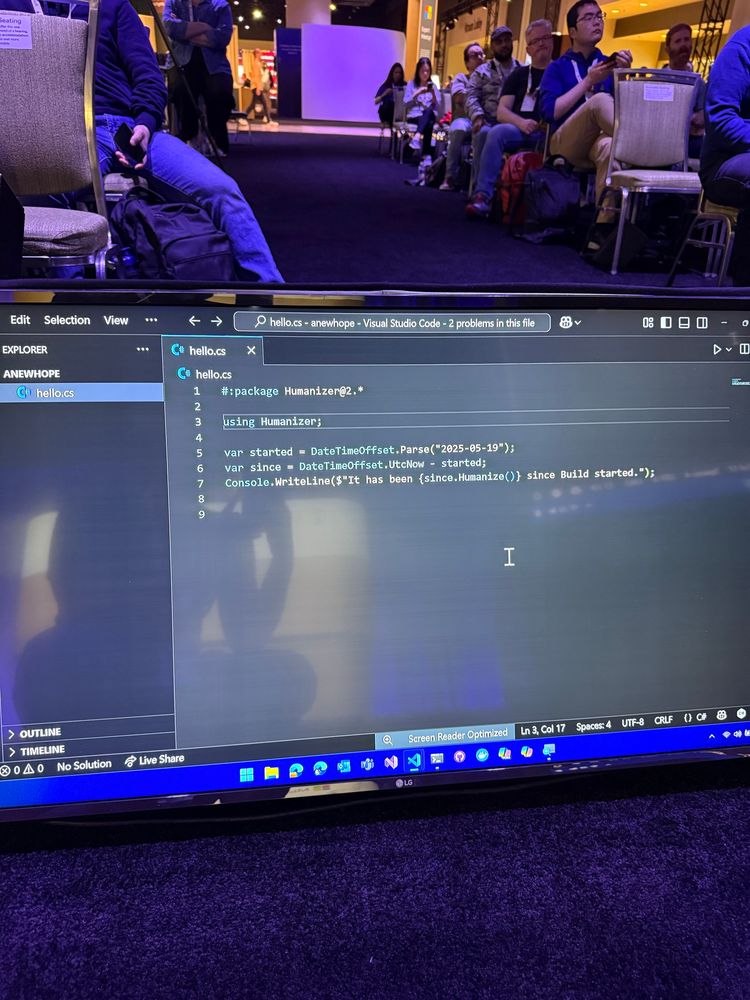
🎥 All presentations from SO-CON 2025 are now live at ghst.ly/socon25-talks.
💻 Slides for each talk are available at ghst.ly/socon25-slides.
🎥 All presentations from SO-CON 2025 are now live at ghst.ly/socon25-talks.
💻 Slides for each talk are available at ghst.ly/socon25-slides.
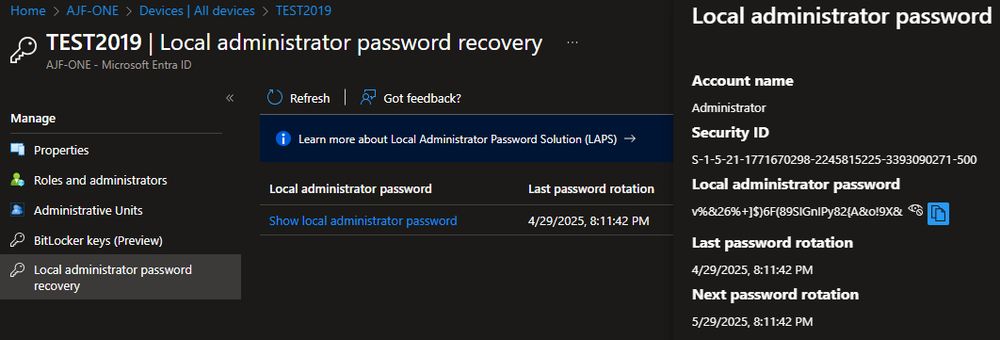
This is a welcome change to prevent the compromise of this high privileged account.
#Entra #Certificate

This is a welcome change to prevent the compromise of this high privileged account.
#Entra #Certificate
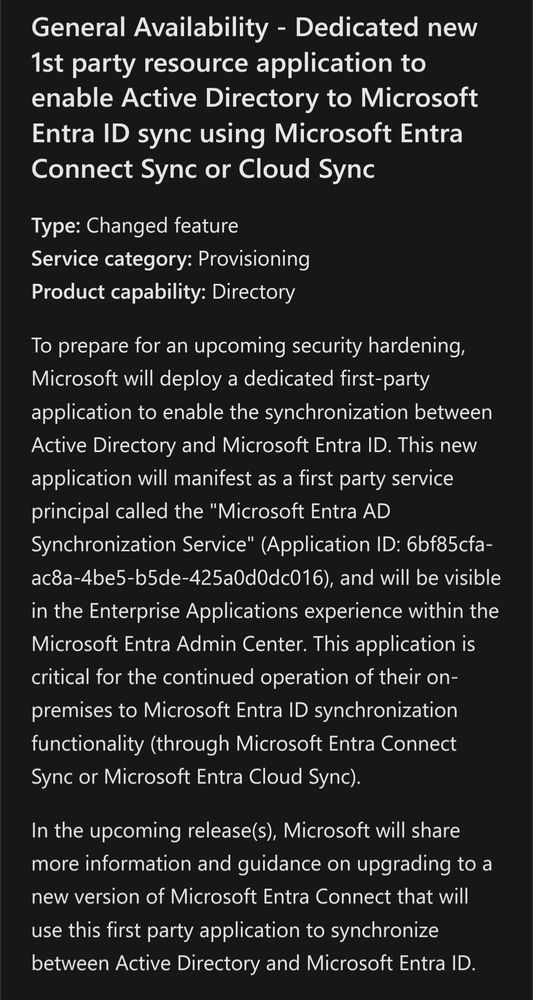
In the announcement the mentioned reason is "upcoming security hardening"...
6bf85cfa-ac8a-4be5-b5de-425a0d0dc016
#EntraID
In the announcement the mentioned reason is "upcoming security hardening"...
6bf85cfa-ac8a-4be5-b5de-425a0d0dc016
#EntraID
Yes, people will be in the streets again. Others will be organizing food drives, volunteering at shelters, hosting teach-ins, and more.
Hundreds of events are already listed at www.FiftyFifty.one/events.
Yes, people will be in the streets again. Others will be organizing food drives, volunteering at shelters, hosting teach-ins, and more.
Hundreds of events are already listed at www.FiftyFifty.one/events.
Check out the schedule to learn more ➡️ ghst.ly/4jzjlnI

Check out the schedule to learn more ➡️ ghst.ly/4jzjlnI
@dru1d.bsky.social for writing a BOF out of the POC
tl;dr get admin on PDQ box, decrypt privileged creds
@dru1d.bsky.social for writing a BOF out of the POC
tl;dr get admin on PDQ box, decrypt privileged creds

Relay attacks are more complicated than many people realize. Check out this deep dive from Elad Shamir on NTLM relay attacks & the new edges we recently added to BloodHound. ghst.ly/4lv3E31

Relay attacks are more complicated than many people realize. Check out this deep dive from Elad Shamir on NTLM relay attacks & the new edges we recently added to BloodHound. ghst.ly/4lv3E31
medium.com/specter-ops-...

medium.com/specter-ops-...


