All things Cyber Security Ops, Threat Hunting, Threat Intel and Incident Mgmt.
2/2
2/2
Or does it still count as cyber if I used a computer to write the letter? 😉
Or does it still count as cyber if I used a computer to write the letter? 😉
Fin.
Fin.
Want to know if anybody is researching an IOC? Want to know what other steps they've made in the investigation? VirusTotal public graphs will tell you.

Want to know if anybody is researching an IOC? Want to know what other steps they've made in the investigation? VirusTotal public graphs will tell you.
Much like the classic Always Sunny in Philadelphia / Pepe Silvia meme:

Much like the classic Always Sunny in Philadelphia / Pepe Silvia meme:


Probably not a great approach in hindsight.
Probably not a great approach in hindsight.
In this case, by a single user based in the US (by IP-GEO) and uploaded via API.
This means that it either formed part of a script, or via an integration with another tool.

In this case, by a single user based in the US (by IP-GEO) and uploaded via API.
This means that it either formed part of a script, or via an integration with another tool.

In this case, the only unique strings in the parent XLSX files are the IOCs we already know about. Maybe not the most exciting in this case, but worth a check!

In this case, the only unique strings in the parent XLSX files are the IOCs we already know about. Maybe not the most exciting in this case, but worth a check!
Then, realising that they made a mistake, requested that VirusTotal take down the original XLSX file.
Unfortunately, that still left behind the constituent files
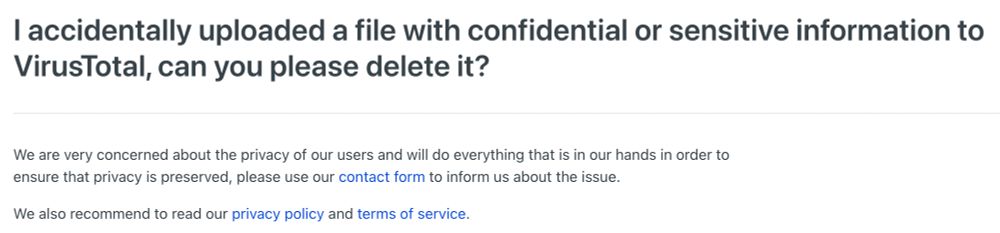
Then, realising that they made a mistake, requested that VirusTotal take down the original XLSX file.
Unfortunately, that still left behind the constituent files

