All things Cyber Security Ops, Threat Hunting, Threat Intel and Incident Mgmt.
Want to know if anybody is researching an IOC? Want to know what other steps they've made in the investigation? VirusTotal public graphs will tell you.

Want to know if anybody is researching an IOC? Want to know what other steps they've made in the investigation? VirusTotal public graphs will tell you.
In this case, by a single user based in the US (by IP-GEO) and uploaded via API.
This means that it either formed part of a script, or via an integration with another tool.

In this case, by a single user based in the US (by IP-GEO) and uploaded via API.
This means that it either formed part of a script, or via an integration with another tool.
In this case, the only unique strings in the parent XLSX files are the IOCs we already know about. Maybe not the most exciting in this case, but worth a check!

In this case, the only unique strings in the parent XLSX files are the IOCs we already know about. Maybe not the most exciting in this case, but worth a check!
Then, realising that they made a mistake, requested that VirusTotal take down the original XLSX file.
Unfortunately, that still left behind the constituent files
Then, realising that they made a mistake, requested that VirusTotal take down the original XLSX file.
Unfortunately, that still left behind the constituent files
VirusTotal's "Compressed Parents" field reveals a SHA256 hash of a file.... which doesn't exist on VirusTotal.
Or at least, it doesn't any more.

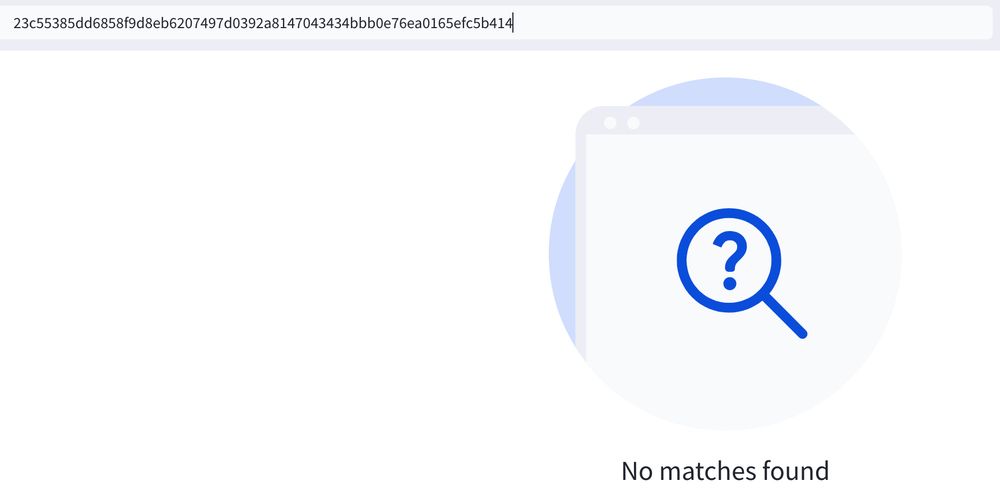
VirusTotal's "Compressed Parents" field reveals a SHA256 hash of a file.... which doesn't exist on VirusTotal.
Or at least, it doesn't any more.
This blog is a good breakdown if you're interested in diving in more:
henrikmassow.medium.com/hacking-exce...

This blog is a good breakdown if you're interested in diving in more:
henrikmassow.medium.com/hacking-exce...

(H/T to @GossiTheDog.cyberplace.social.ap.brid.gy for first spotting this)
Having a search for some of the IOCs from the BeyondTrust blog, reveals that they appear in a file uploaded to VirusTotal on the 19th December

(H/T to @GossiTheDog.cyberplace.social.ap.brid.gy for first spotting this)
Having a search for some of the IOCs from the BeyondTrust blog, reveals that they appear in a file uploaded to VirusTotal on the 19th December
24.144.114[.]85
142.93.119[.]175
157.230.183[.]1
192.81.209[.]168
As well as some additional IPv6 addresses:

24.144.114[.]85
142.93.119[.]175
157.230.183[.]1
192.81.209[.]168
As well as some additional IPv6 addresses:
1) In a letter to US Senators, it is revealed that attackers were able to gain access to a service at BeyondTrust that gave them remote access to US Treasury workstations.
legacy.www.documentcloud.org/documents/25...

1) In a letter to US Senators, it is revealed that attackers were able to gain access to a service at BeyondTrust that gave them remote access to US Treasury workstations.
legacy.www.documentcloud.org/documents/25...


All it would take is some imaginative "Breaking News" to hit public confidence.
Can the real BBC News please stand up?
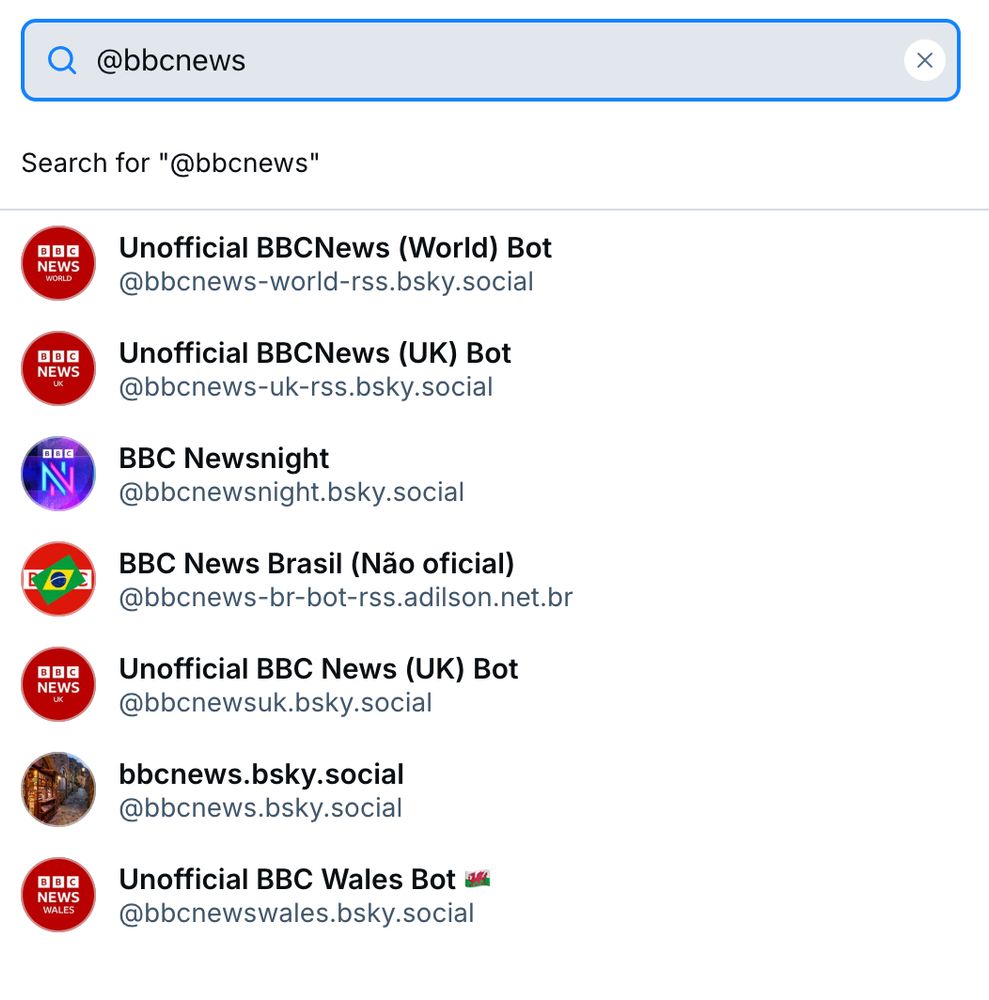
All it would take is some imaginative "Breaking News" to hit public confidence.
Can the real BBC News please stand up?
I was feeling particularly lazy, so got ChatGPT to give it a go. I actually quite like the simplicity of its response.
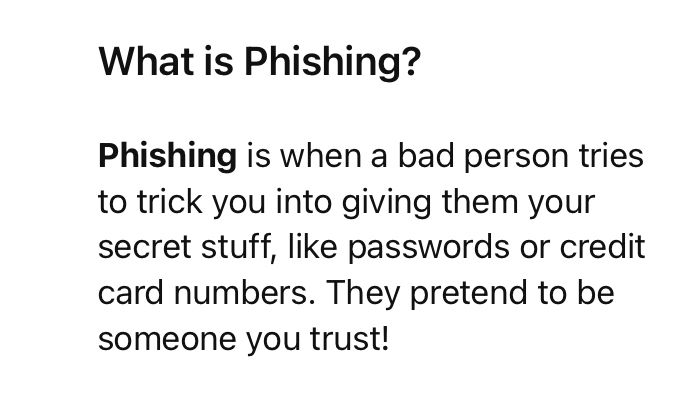
I was feeling particularly lazy, so got ChatGPT to give it a go. I actually quite like the simplicity of its response.




