
https://buff.ly/4ibOEo8

https://buff.ly/4ibOEo8

#APT
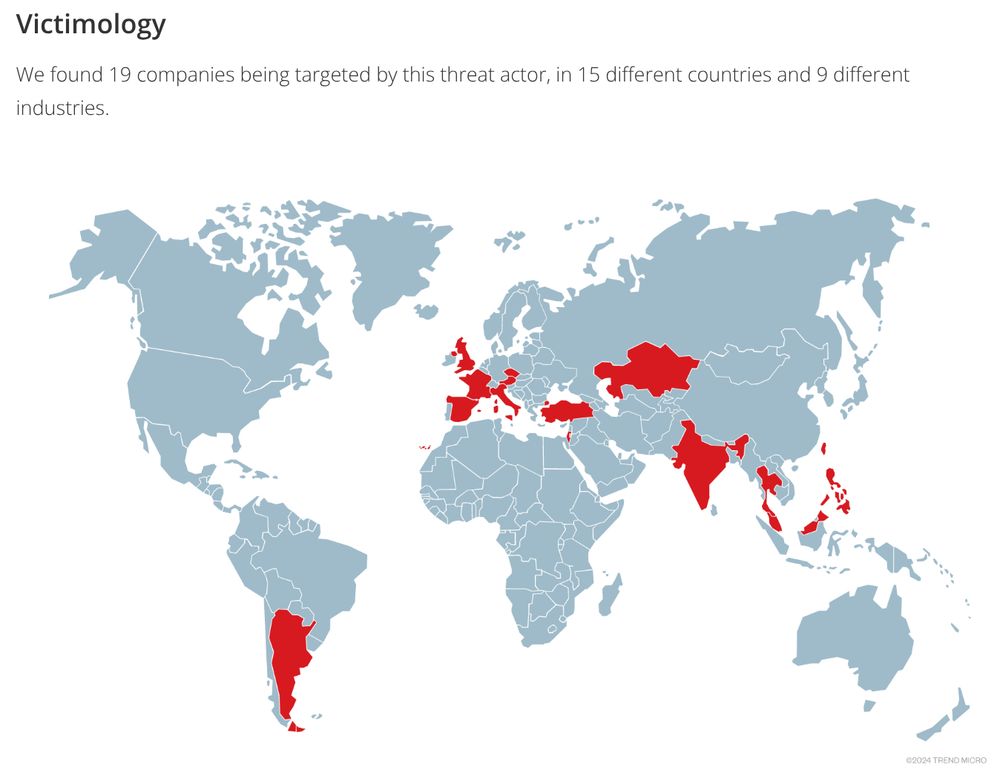
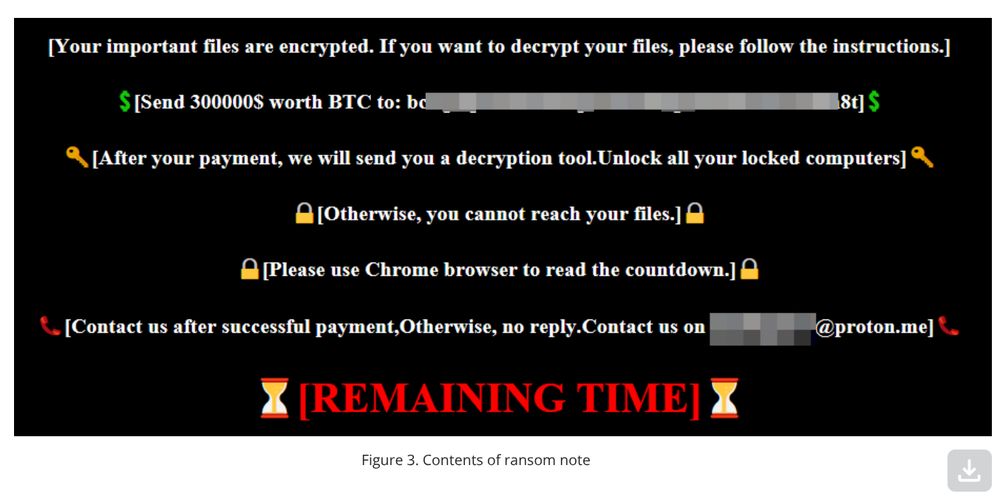
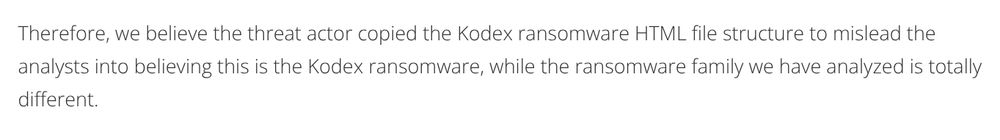
#APT
cloud.google.com/blog/topics/...
cloud.google.com/blog/topics/...
#dfir #threatintel #m365security
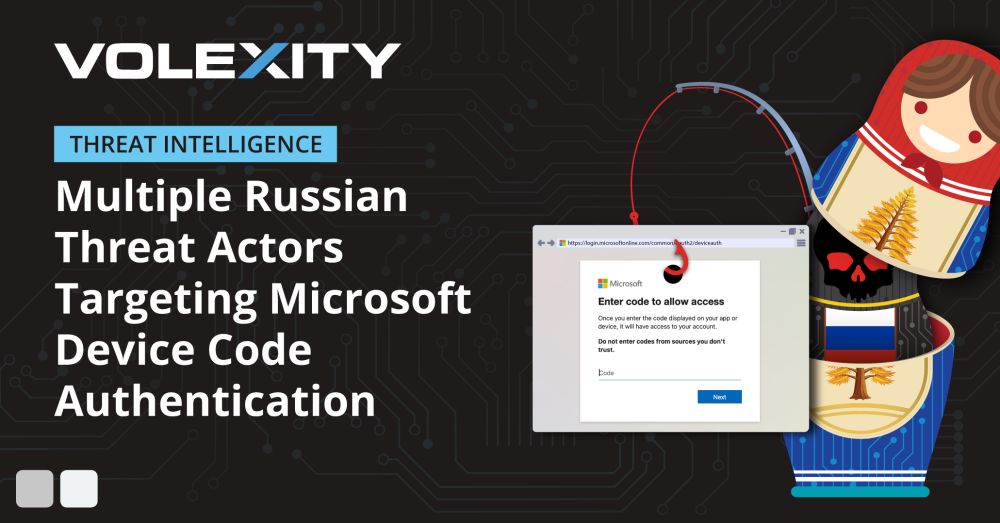
#dfir #threatintel #m365security
www.microsoft.com/en-us/securi...

www.microsoft.com/en-us/securi...

🧵1/6
🧵1/6
https://buff.ly/3WEwPG7

https://buff.ly/3WEwPG7
cloud.google.com/blog/topics/...

cloud.google.com/blog/topics/...
🧵⤵️
1) spoofing swisscom (note 'S', domain just reg'd)
2) leveraging encrypted rar + lnk + self signed pdf reader
3) BGP lure (fits with theme of email). BGP is the third leg in the outage triumvirate)


🧵⤵️
Frequent freeloader part II: Russian actor Secret Blizzard using tools of other groups to attack Ukraine
www.microsoft.com/en-us/securi...

Frequent freeloader part II: Russian actor Secret Blizzard using tools of other groups to attack Ukraine
www.microsoft.com/en-us/securi...
Then me and Tommy went back to ecrime 😂
www.proofpoint.com/us/blog/thre...

Then me and Tommy went back to ecrime 😂
www.proofpoint.com/us/blog/thre...

www.microsoft.com/en-us/securi...

www.microsoft.com/en-us/securi...

Enjoy securityconversations.com/episode/vole...

Enjoy securityconversations.com/episode/vole...
Read more here: www.volexity.com/blog/2024/11...

Read more here: www.volexity.com/blog/2024/11...

ProcDump functionality is now available on Windows, Linux, and macOS.
Get the tools at sysinternals.com.
See what's new on the Sysinternals Blog:

ProcDump functionality is now available on Windows, Linux, and macOS.
Get the tools at sysinternals.com.
See what's new on the Sysinternals Blog:

