
We received no response on the RHEL bug tracker:
bugzilla.redhat.com/show_bug.cgi...
We received no response on the RHEL bug tracker:
bugzilla.redhat.com/show_bug.cgi...
x.com/RedTeamPT/st...

x.com/RedTeamPT/st...
access.redhat.com/security/cve...
access.redhat.com/security/cve...
github.com/fortra/impac...
github.com/fortra/impac...
This could reveal system level variables, which could be interesting in some configurations.

This could reveal system level variables, which could be interesting in some configurations.
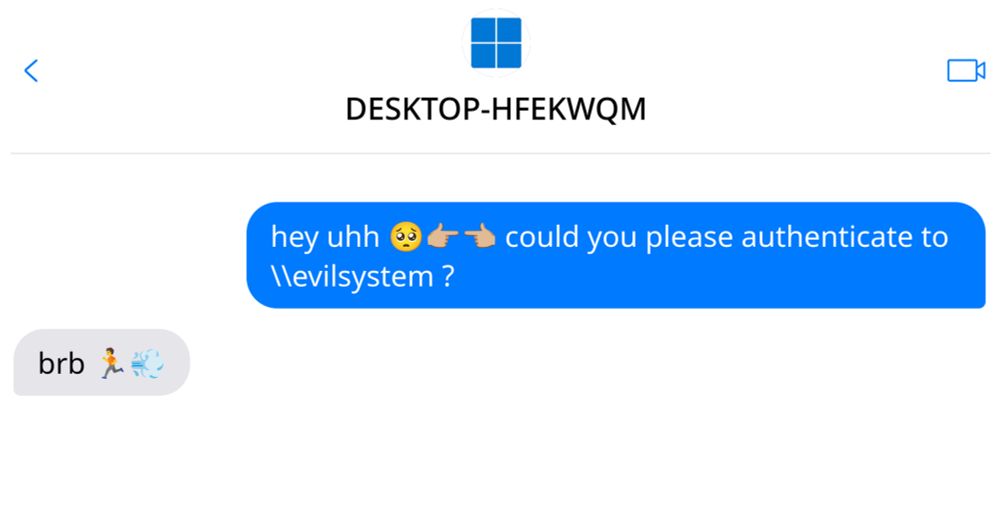
So if Defender prevents you from executing code on a computer with an admin, just let it snitch on the admin with a relayable NTLMv2-Hash🤯

So if Defender prevents you from executing code on a computer with an admin, just let it snitch on the admin with a relayable NTLMv2-Hash🤯
Where do the credentials come from? Well, if the same user is also interactively logged on, Defender will simply steal their token 🥷🏼
Where do the credentials come from? Well, if the same user is also interactively logged on, Defender will simply steal their token 🥷🏼

habr.com/ru/companies...

habr.com/ru/companies...
www.redteam-pentesting.de/publications...
For those that only need a short overview, here's our advisory 🚨:
www.redteam-pentesting.de/advisories/r...
www.redteam-pentesting.de/publications...
For those that only need a short overview, here's our advisory 🚨:
www.redteam-pentesting.de/advisories/r...
blog.redteam-pentesting.de/2025/windows...
blog.redteam-pentesting.de/2025/windows...


