
We have been hard at work and are excited to have you play our challenges 👀
CTF starts at 10am CET on 29th November with prizes sponsored by our lovely sponsors @redteam-pentesting.de and @binary.ninja

We have been hard at work and are excited to have you play our challenges 👀
CTF starts at 10am CET on 29th November with prizes sponsored by our lovely sponsors @redteam-pentesting.de and @binary.ninja
We're sponsoring the prize money for the best writeups and are excited to see your creative solutions.
haix-la-chapelle.eu
We're sponsoring the prize money for the best writeups and are excited to see your creative solutions.
haix-la-chapelle.eu
blog.redteam-pentesting.de/2025/reflect...

blog.redteam-pentesting.de/2025/reflect...
It will be a Jeopardy style CTF and will start at 10 am Berlin time, lasting for 24 hours.
You can find the CTFTime event at ctftime.org/event/2951
See you there!
It will be a Jeopardy style CTF and will start at 10 am Berlin time, lasting for 24 hours.
You can find the CTFTime event at ctftime.org/event/2951
See you there!
In addition to leaking environment variables, it is possible to coerce authentication from arbitrary logged on users* 🤯
*If you are willing to trigger Windows Defender.
In addition to leaking environment variables, it is possible to coerce authentication from arbitrary logged on users* 🤯
*If you are willing to trigger Windows Defender.
#rwth #informatik #aachen
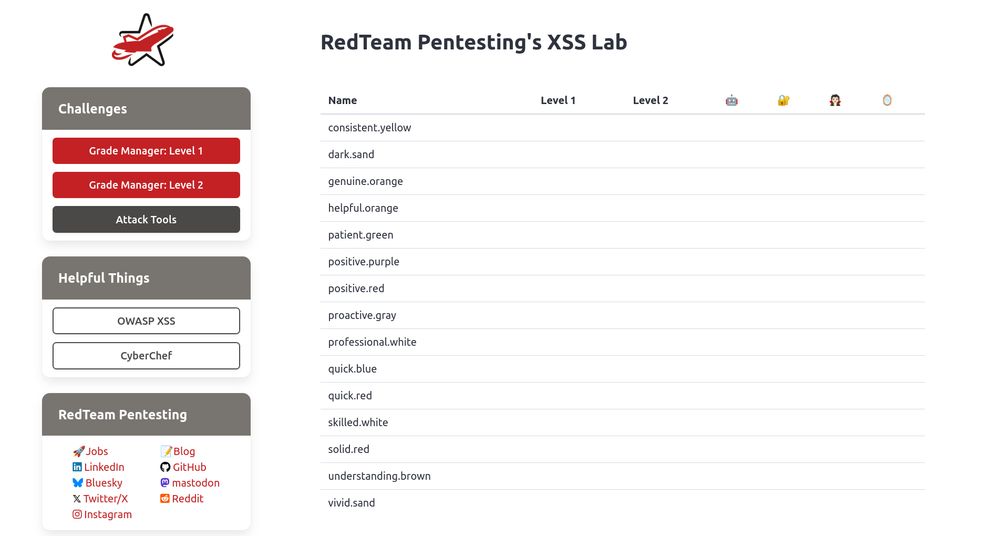
#rwth #informatik #aachen
@tiraniddo.dev @decoder-it.bsky.social @synacktiv.com #infosecsky #infosec #pentests #redteam #cybersky #cybersecurity
bsky.app/profile/redt...
@tiraniddo.dev @decoder-it.bsky.social @synacktiv.com #infosecsky #infosec #pentests #redteam #cybersky #cybersecurity
bsky.app/profile/redt...
🪞The Reflective Kerberos Relay Attack - Remote privilege escalation from low-priv user to SYSTEM with RCE by applying a long forgotten NTLM relay technique to Kerberos:
blog.redteam-pentesting.de/2025/reflect...

🪞The Reflective Kerberos Relay Attack - Remote privilege escalation from low-priv user to SYSTEM with RCE by applying a long forgotten NTLM relay technique to Kerberos:
blog.redteam-pentesting.de/2025/reflect...
Stay tuned for our blog post and paper about it tomorrow at 10:00 am CEST 🔥
Stay tuned for our blog post and paper about it tomorrow at 10:00 am CEST 🔥
To quickly deploy an SMB server with signing supported we implemented this in impacket's smbserver.py based on a prior work by @lowercasedrm.bsky.social .
github.com/fortra/impac...
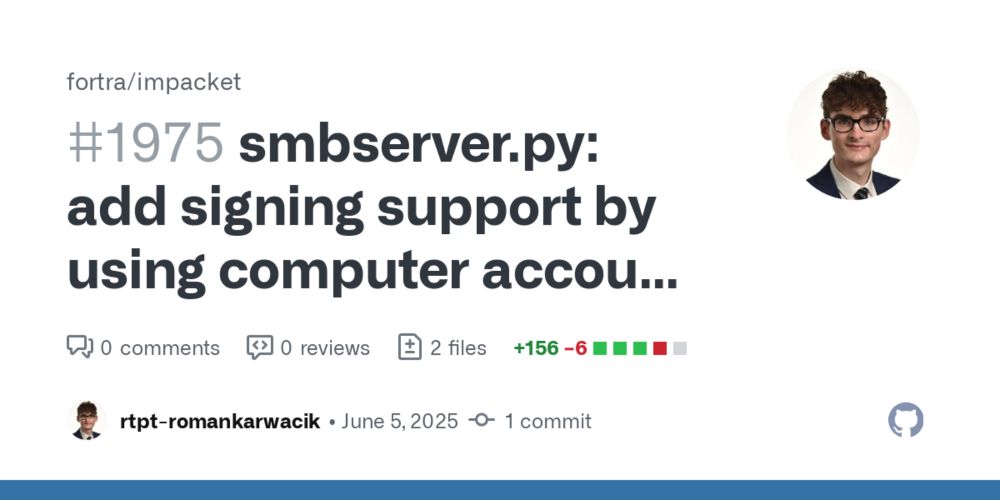
To quickly deploy an SMB server with signing supported we implemented this in impacket's smbserver.py based on a prior work by @lowercasedrm.bsky.social .
github.com/fortra/impac...
Join us on our deep dive into Windows Authentication Coercion and its current state in 2025, including some brand-new tooling ✨
#infosecsky #infosec #pentests #redteam #cybersky #cybersecurity
blog.redteam-pentesting.de/2025/windows...
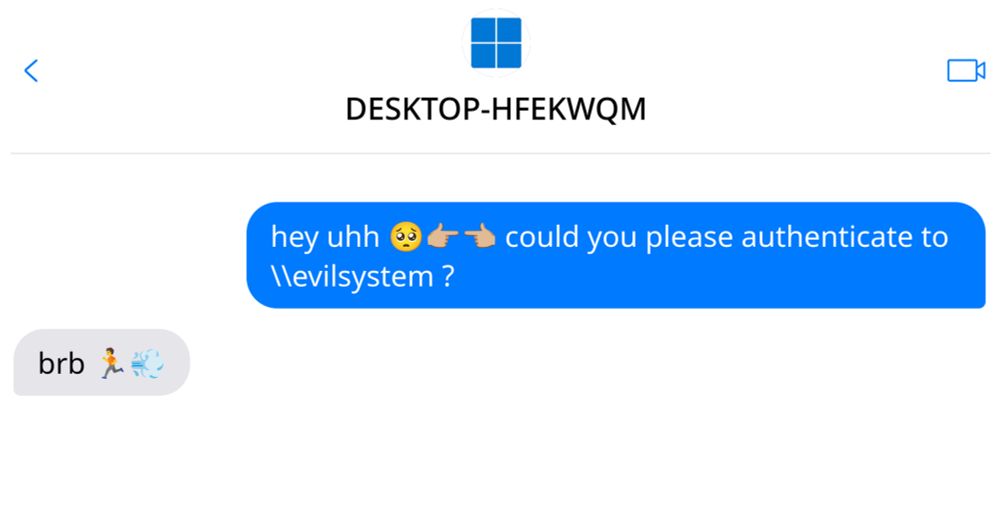
Join us on our deep dive into Windows Authentication Coercion and its current state in 2025, including some brand-new tooling ✨
#infosecsky #infosec #pentests #redteam #cybersky #cybersecurity
blog.redteam-pentesting.de/2025/windows...

