

www.neowin.net/sponsored/th...

www.neowin.net/sponsored/th...

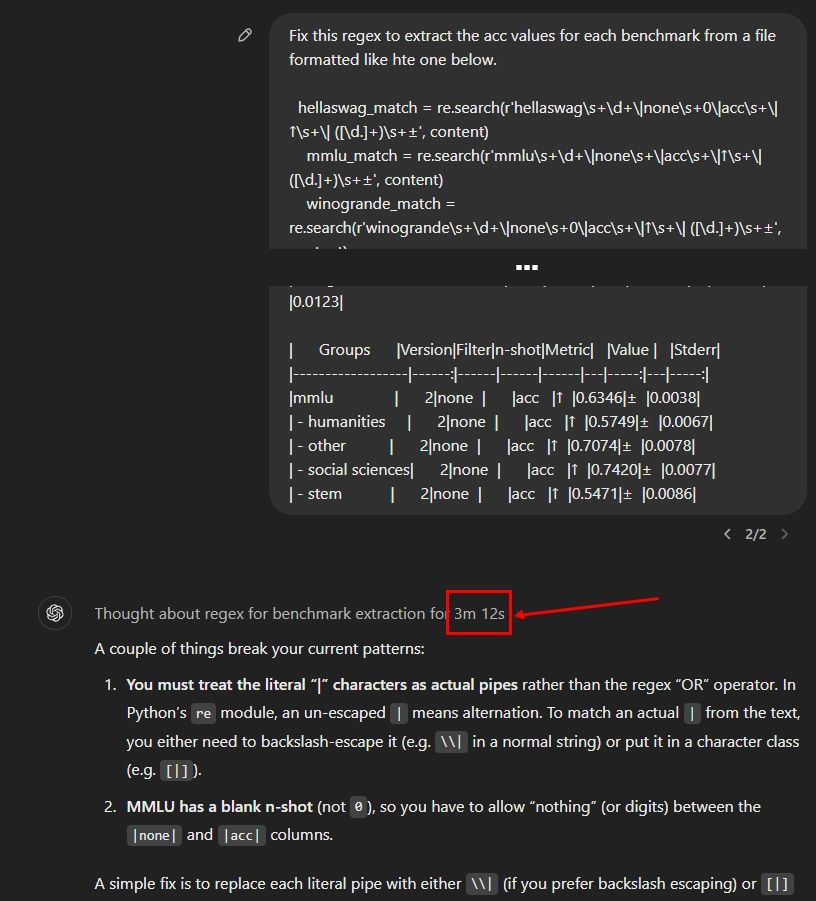
go.bsky.app/HQWqtno
go.bsky.app/HQWqtno
www.microsoft.com/en-us/securi...

www.microsoft.com/en-us/securi...
blog.sekoia.io/ransomware-d...
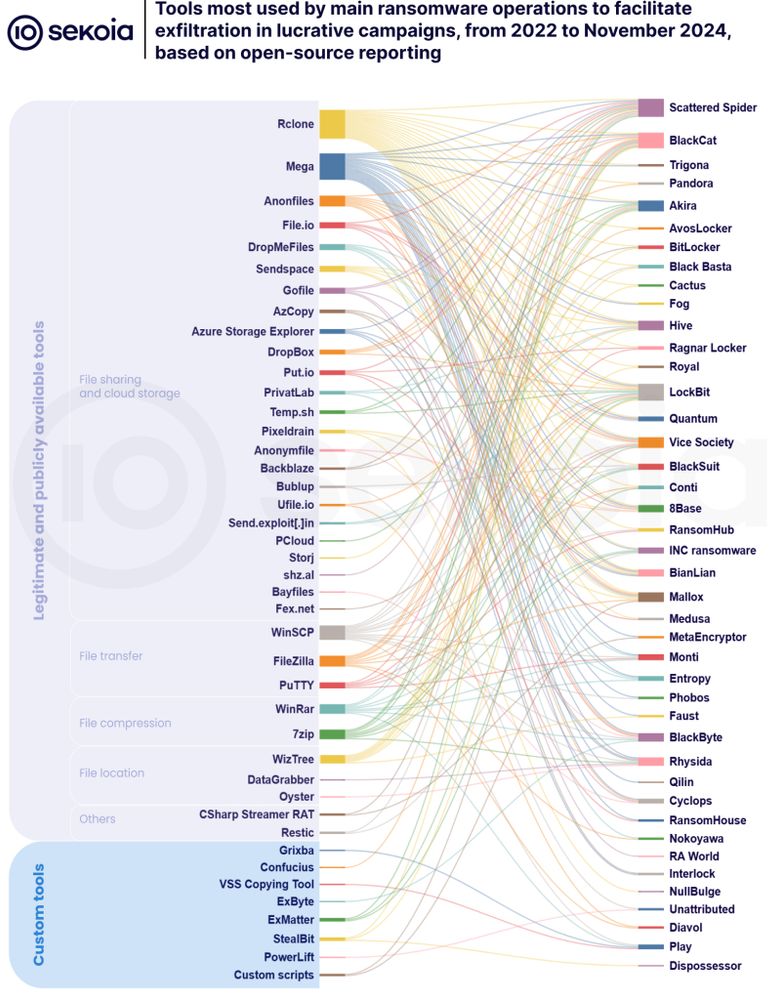
blog.sekoia.io/ransomware-d...
docs.google.com/presentation...
#redteam #purpleteam #redteamvillage
docs.google.com/presentation...
#redteam #purpleteam #redteamvillage

CC: @maryst33d.bsky.social
linuxdfir.ashemery.com
CC: @maryst33d.bsky.social
linuxdfir.ashemery.com
www.eventbrite.co.uk/e/bsides-lon...
Please be a team player and remember to cancel your ticket if you can no longer be there on the day!
#Security #BSides #London #Tickets

www.eventbrite.co.uk/e/bsides-lon...
Please be a team player and remember to cancel your ticket if you can no longer be there on the day!
#Security #BSides #London #Tickets
We all know ransomware TAs affect companies and their bottom line. And there’s an understanding that it affects individuals too..
We all know ransomware TAs affect companies and their bottom line. And there’s an understanding that it affects individuals too..
Russian language but Google translate does a great job.
rt-solar.ru/solar-4rays/...

Russian language but Google translate does a great job.
rt-solar.ru/solar-4rays/...
1. https://buff.ly/3xhyTtU
2. https://buff.ly/40OLdhw
3. https://buff.ly/3UIbQB0

1. https://buff.ly/3xhyTtU
2. https://buff.ly/40OLdhw
3. https://buff.ly/3UIbQB0
naehrdine.blogspot.com/2024/11/reve...

naehrdine.blogspot.com/2024/11/reve...


