#redteam
@rastamouse.me pretty much predicted what was coming in his last blog post. attach (Win32 APIs), redirect (local funcs), capability right-sized IAT hooks, and PICO function exports.
Yes, attach can incept its PIC.
aff-wg.org/2025/11/10/t...

@rastamouse.me pretty much predicted what was coming in his last blog post. attach (Win32 APIs), redirect (local funcs), capability right-sized IAT hooks, and PICO function exports.
Yes, attach can incept its PIC.
aff-wg.org/2025/11/10/t...
github.com/pard0p/PICO-...

github.com/pard0p/PICO-...
"Provided as a Crystal Palace shared library. Format inspired by @rastamouse.me 's LibTP. "
Ground truth security research.
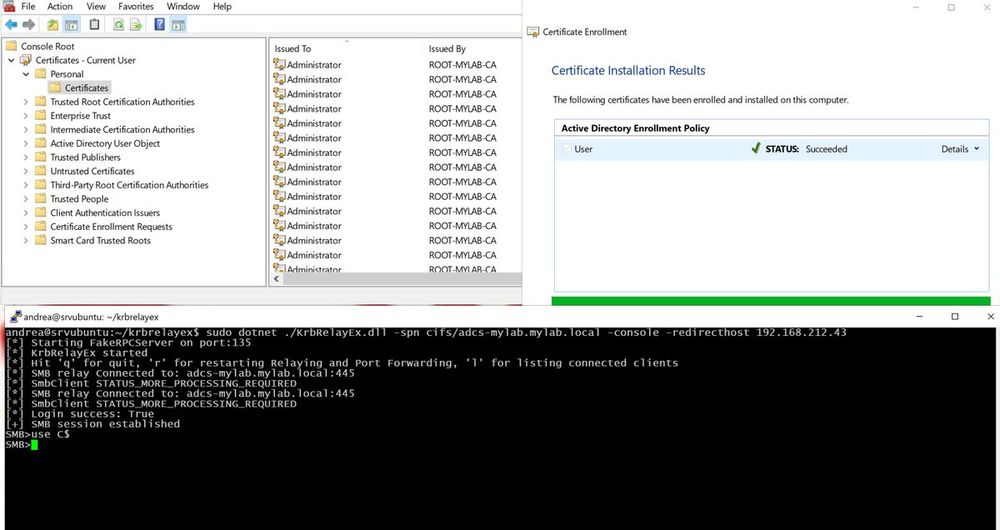
Post: offsec.almond.consulting/evading-elas...
PoC: github.com/AlmondOffSec...

"Provided as a Crystal Palace shared library. Format inspired by @rastamouse.me 's LibTP. "
Ground truth security research.
github.com/pard0p/LibWi...
github.com/pard0p/LibWi...
Dynamic Function Resolution pt. 2, Say yes to the .bss, and symbol remapping.
aff-wg.org/2025/10/27/t...

Dynamic Function Resolution pt. 2, Say yes to the .bss, and symbol remapping.
aff-wg.org/2025/10/27/t...
github.com/ofasgard/exe...
I've tested it with Rubeus and Seatbelt and a variety of different arguments, and it seems to be pretty stable as far as I can tell. If anyone uses this PICO and encounters bugs or instability, please let me know!
github.com/ofasgard/exe...
I've tested it with Rubeus and Seatbelt and a variety of different arguments, and it seems to be pretty stable as far as I can tell. If anyone uses this PICO and encounters bugs or instability, please let me know!

aff-wg.org/2025/10/13/w...
Dynamic Function Resolution for PIC(?!?), rewriting x86 PIC to fix pointers, and a shared library concept for PICOs/PIC

aff-wg.org/2025/10/13/w...
Dynamic Function Resolution for PIC(?!?), rewriting x86 PIC to fix pointers, and a shared library concept for PICOs/PIC
aff-wg.org/2025/09/26/a...
Breach analysis? Breach intelligence? Industry critique? Fee-only ransomware negotiator? 100% efficacy? The story of how Microsoft worked an old problem, fucked it up, we malign the guy who told us, they fixed it, and it wasn't fixed? PtH?
aff-wg.org/2025/09/26/a...
Breach analysis? Breach intelligence? Industry critique? Fee-only ransomware negotiator? 100% efficacy? The story of how Microsoft worked an old problem, fucked it up, we malign the guy who told us, they fixed it, and it wasn't fixed? PtH?
rastamouse.me/modular-pic-...

rastamouse.me/modular-pic-...

rastamouse.me/modular-pic-...
www.eventbrite.co.uk/e/beacon-25-...
beac0n.org
From his X: "If you enjoy filthy PIC tradecraft it may be of interest!"

www.eventbrite.co.uk/e/beacon-25-...
beac0n.org
From his X: "If you enjoy filthy PIC tradecraft it may be of interest!"
My July 2025 overview of PIC writing fundamentals.
Don't know why jump tables are bad? Got a __chkstk relocation error? Watch this video.
#GoodLuckAndHappyHacking
vimeo.com/1100089433/d...

My July 2025 overview of PIC writing fundamentals.
Don't know why jump tables are bad? Got a __chkstk relocation error? Watch this video.
#GoodLuckAndHappyHacking
vimeo.com/1100089433/d...
aff-wg.org/2025/07/09/t...
Some updates to... the Tradecraft Garden and Crystal Palace. Info in the 🧵 below:

Join @atomicchonk.bsky.social next week to understand Windows access tokens & their use in the Windows environment. ghst.ly/june-web-bsky

Join @atomicchonk.bsky.social next week to understand Windows access tokens & their use in the Windows environment. ghst.ly/june-web-bsky
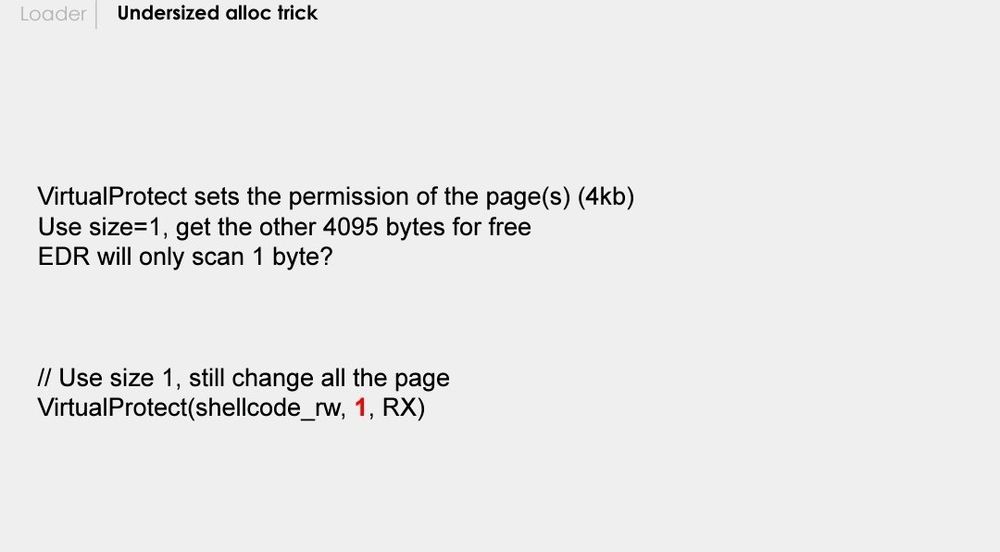
My First and Last Shellcode Loader by @dobinrutis.bsky.social at HITB 2024.
H/T x.com/Jean_Maes_19...
My First and Last Shellcode Loader by @dobinrutis.bsky.social at HITB 2024.
H/T x.com/Jean_Maes_19...
The Tradecraft Garden.
tradecraftgarden.org
It's Crystal Palace, an open-source linker and linker script specialized to writing PIC DLL loaders.
And, a corpora of DLL loaders demonstrating design patterns building tradecraft with it.

blog.back.engineering/06/05/2022/

blog.back.engineering/06/05/2022/
blog.lumen.com/snowblind-th...

blog.lumen.com/snowblind-th...
📢In my latest blog post I discuss another network based technique to prevent data ingest and ways to detect it.
And if you want even more, checkout part 2 released by @Cyb3rMonk Link in the post

📢In my latest blog post I discuss another network based technique to prevent data ingest and ways to detect it.
And if you want even more, checkout part 2 released by @Cyb3rMonk Link in the post
This post summarises how to tie Cobalt Strike's UDRL, SleepMask, and BeaconGate together for your syscall and call stack spoofing needs.
rastamouse.me/udrl-sleepma...

This post summarises how to tie Cobalt Strike's UDRL, SleepMask, and BeaconGate together for your syscall and call stack spoofing needs.
rastamouse.me/udrl-sleepma...