blog.compass-security.com/2025/04/3-mi...
blog.compass-security.com/2025/04/3-mi...

If you love connecting with VARs, distributors, & consultants, submit your application today: ghst.ly/3XYrzO4

If you love connecting with VARs, distributors, & consultants, submit your application today: ghst.ly/3XYrzO4
Read more 👉 ghst.ly/4iXFTyF
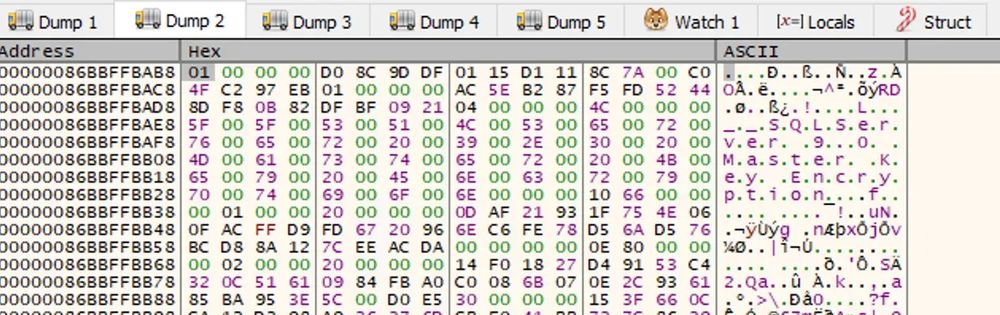
Relay attacks are more complicated than many people realize. Check out this deep dive from Elad Shamir on NTLM relay attacks & the new edges we recently added to BloodHound. ghst.ly/4lv3E31

Relay attacks are more complicated than many people realize. Check out this deep dive from Elad Shamir on NTLM relay attacks & the new edges we recently added to BloodHound. ghst.ly/4lv3E31
DYK that BloodHound CE now supports deep linking? This week, we released early access support that goes beyond what the old back button offered! Go back (& forward), & share your current view of the graph w/ your fellow operators today!
1/2

DYK that BloodHound CE now supports deep linking? This week, we released early access support that goes beyond what the old back button offered! Go back (& forward), & share your current view of the graph w/ your fellow operators today!
1/2

www.zscaler.com/blogs/securi...

www.zscaler.com/blogs/securi...
github.com/atomicchonk/...

github.com/atomicchonk/...
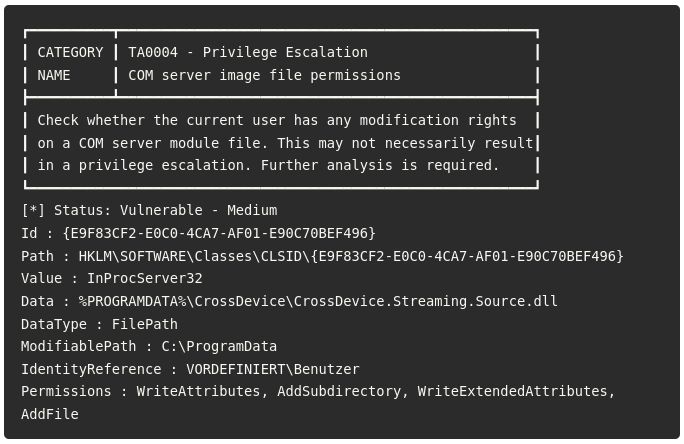
bishopfox.com/resources/re...

bishopfox.com/resources/re...
Discover the latest tactics used by attackers and learn actionable countermeasures during Binary Defense's ThreatTalk webinar. Save your seat today: www.binarydefense.com/resources/we...
#Cybersecurity #ThreatTalk #EDR

Discover the latest tactics used by attackers and learn actionable countermeasures during Binary Defense's ThreatTalk webinar. Save your seat today: www.binarydefense.com/resources/we...
#Cybersecurity #ThreatTalk #EDR
Register ➡️ ghst.ly/apr-demo-bsky

Register ➡️ ghst.ly/apr-demo-bsky

www.troyhunt.com/a-sneaky-phi...

www.troyhunt.com/a-sneaky-phi...
- Blog: ibm.com/think/news/f...
- PoC: github.com/xforcered/Fo...

- Blog: ibm.com/think/news/f...
- PoC: github.com/xforcered/Fo...

bishopfox.com/blog/rust-fo...

bishopfox.com/blog/rust-fo...
➡️ jobs.diversifytech.com

➡️ jobs.diversifytech.com

Our Chief Product Officer Justin Kohler will be at #GartnerIAM demonstrating how attackers exploit these connections & how Attack Path Management can help close these gaps. ghst.ly/4kzkFbB

Our Chief Product Officer Justin Kohler will be at #GartnerIAM demonstrating how attackers exploit these connections & how Attack Path Management can help close these gaps. ghst.ly/4kzkFbB
Q: Why is not just the DA group Tier Zero but also all members?
A: BloodHound classifies a few default Tier Zero assets, then adds more w/ logic from known attack techniques.
1/8
Q: Why is not just the DA group Tier Zero but also all members?
A: BloodHound classifies a few default Tier Zero assets, then adds more w/ logic from known attack techniques.
1/8
cobaltstrike.com/blog/cobalt-...

cobaltstrike.com/blog/cobalt-...
Ex 1 - www.bleepingcomputer.com/news/securit...
Ex 2 -

Ex 1 - www.bleepingcomputer.com/news/securit...
Ex 2 -