
We’re Bishop Fox, leaders in offensive security for nearly 20 years. From pentesting to attack surface management with Cosmos, we help organizations stay ahead of attackers.
Follow us for insights, research, and cybersecurity updates!
#cybersecurity #offensivesecurity #pentesting
Bishop Fox is sponsoring again this year, with talks from Dan Petro and Nate Robb on EDR evasion and real-world CVE prioritization. And we’ll be around all weekend to talk tradecraft, research, and offsec!
Feb 6-7 | Mesa, AZ

Bishop Fox is sponsoring again this year, with talks from Dan Petro and Nate Robb on EDR evasion and real-world CVE prioritization. And we’ll be around all weekend to talk tradecraft, research, and offsec!
Feb 6-7 | Mesa, AZ
Join @datadoghq.com’s State of Cloud Security livestream with Senior Security Consultant @alethe.bsky.social for an attacker-focused breakdown of what the cloud security data is really showing.
Jan 27 | 12 p.m. ET

Join @datadoghq.com’s State of Cloud Security livestream with Senior Security Consultant @alethe.bsky.social for an attacker-focused breakdown of what the cloud security data is really showing.
Jan 27 | 12 p.m. ET
CloudFox helps surface the good stuff: real attack paths in AWS and GCP.
Try it on GitHub: github.com/BishopFox/cl...




CloudFox helps surface the good stuff: real attack paths in AWS and GCP.
Try it on GitHub: github.com/BishopFox/cl...
January 27 @ 12 p.m. EST

January 27 @ 12 p.m. EST




On Jan 21, Dan Petro walks through how app pen tests work in practice, common gaps, and how to get better results in modern, API-heavy environments.
bishopfox.com/resources/ap...

On Jan 21, Dan Petro walks through how app pen tests work in practice, common gaps, and how to get better results in modern, API-heavy environments.
bishopfox.com/resources/ap...
This free guide explains how application penetration testing fits into modern development, what good testing looks like, and how to use results to improve security over time: bishopfox.com/resources/ap...

This free guide explains how application penetration testing fits into modern development, what good testing looks like, and how to use results to improve security over time: bishopfox.com/resources/ap...
Check out our top research, virtual sessions, blogs, and new tools of the year!
Special acknowledgements: @alethe.bsky.social, @br4inde4d.bsky.social, @noperator.bsky.social


Check out our top research, virtual sessions, blogs, and new tools of the year!
Special acknowledgements: @alethe.bsky.social, @br4inde4d.bsky.social, @noperator.bsky.social
IAM Vulnerable is an open source playground that spins up intentionally vulnerable IAM configs so you can practice finding and exploiting real privesc paths safely.
Try it: github.com/BishopFox/ia...
More info: bishopfox.com/tools/iam-vu...




IAM Vulnerable is an open source playground that spins up intentionally vulnerable IAM configs so you can practice finding and exploiting real privesc paths safely.
Try it: github.com/BishopFox/ia...
More info: bishopfox.com/tools/iam-vu...
This post walks through how red teams can use AADAPT as a practical roadmap, starting with value flows and ending with real detection signals.
bishopfox.com/blog/mitre-a...

This post walks through how red teams can use AADAPT as a practical roadmap, starting with value flows and ending with real detection signals.
bishopfox.com/blog/mitre-a...


We just dropped a Hacker Holiday Gift Guide with gear, books, and tools hackers actually want, all sourced from our team and community.
bishopfox.com/blog/hacker-...

We just dropped a Hacker Holiday Gift Guide with gear, books, and tools hackers actually want, all sourced from our team and community.
bishopfox.com/blog/hacker-...
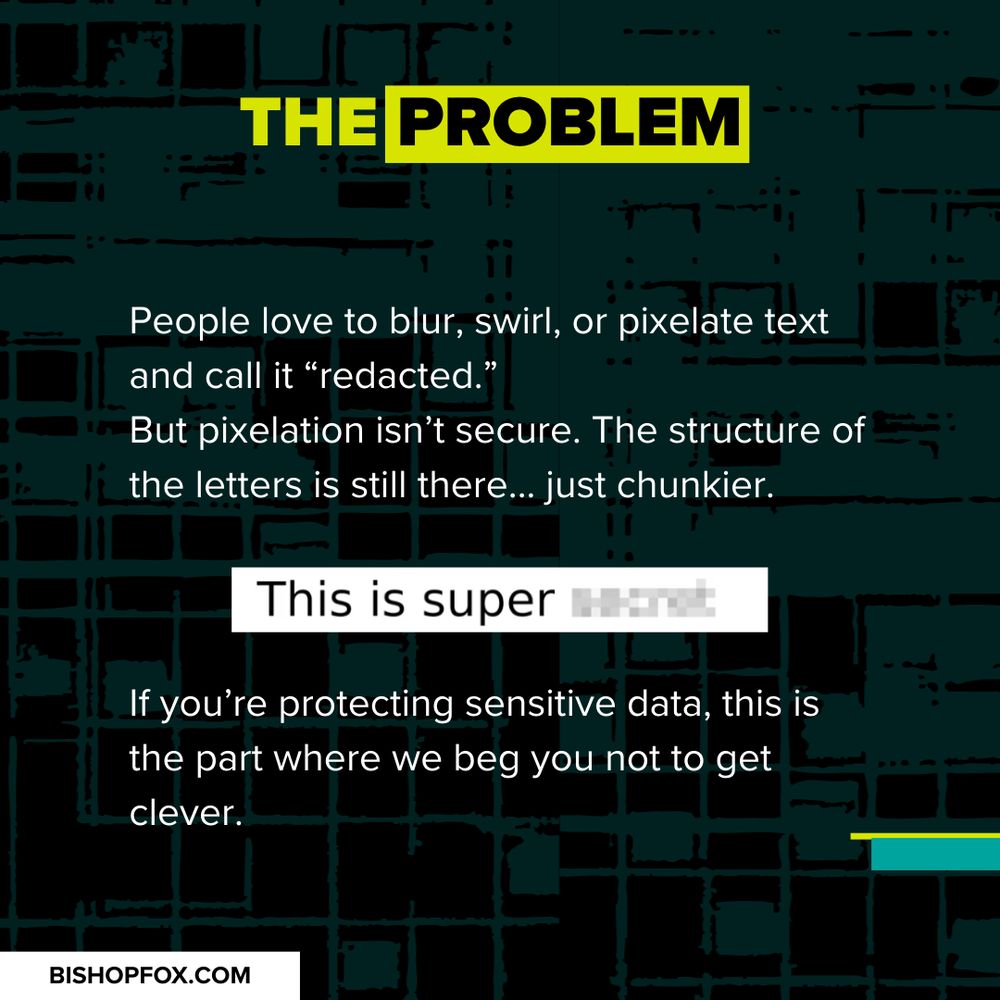
Pixelation ≠ redaction.
Unredacter proves it.
Play with the tool → bishopfox.com/tools/unreda...



Pixelation ≠ redaction.
Unredacter proves it.
Play with the tool → bishopfox.com/tools/unreda...
Join Trevin Edgeworth tomorrow to hear how we’re evolving our Red Teaming to keep up: bishopfox.com/resources/re...

Join Trevin Edgeworth tomorrow to hear how we’re evolving our Red Teaming to keep up: bishopfox.com/resources/re...
Sliver Workshop Part 3: Building Better Encoders is starting now.
Join us to learn how Sliver handles traffic encoding and how to build custom WebAssembly-based encoders: bishopfox.com/resources/sl...

Sliver Workshop Part 3: Building Better Encoders is starting now.
Join us to learn how Sliver handles traffic encoding and how to build custom WebAssembly-based encoders: bishopfox.com/resources/sl...
Full guide here: bishopfox.com/resources/ap...

Full guide here: bishopfox.com/resources/ap...
Sliver Workshop: Building Better Encoders
2 p.m. ET / 7 p.m. GMT
Join via Discord or our site.
Tim Makram Ghatas will cover Sliver’s encoding defaults, WebAssembly, and how to design/test custom encoders.

Sliver Workshop: Building Better Encoders
2 p.m. ET / 7 p.m. GMT
Join via Discord or our site.
Tim Makram Ghatas will cover Sliver’s encoding defaults, WebAssembly, and how to design/test custom encoders.
Quickly scan GitHub for exposed secrets using flexible filtering and fuzzy matching.
Built to make large search results easier to work through.




Quickly scan GitHub for exposed secrets using flexible filtering and fuzzy matching.
Built to make large search results easier to work through.
More AI. More connected systems. More attacker automation.
Our leadership team breaks down the forces that will reshape pen testing, CISO priorities, hardware security, and Red Team specialization next year.




More AI. More connected systems. More attacker automation.
Our leadership team breaks down the forces that will reshape pen testing, CISO priorities, hardware security, and Red Team specialization next year.
On Dec 11, Trevin Edgeworth discusses how Red Teaming helps validate resilience against AI-driven threats.
2 p.m. ET
Save your seat: bishopfox.com/resources/re...

On Dec 11, Trevin Edgeworth discusses how Red Teaming helps validate resilience against AI-driven threats.
2 p.m. ET
Save your seat: bishopfox.com/resources/re...
This session covers building better encoders, how Sliver handles traffic encoding, and how to extend it with custom Wasm-based techniques.
Hosted by Senior Security Consultant Tim Makram Ghatas.

This session covers building better encoders, how Sliver handles traffic encoding, and how to extend it with custom Wasm-based techniques.
Hosted by Senior Security Consultant Tim Makram Ghatas.

