Microsoft implemented a driver-based protection to block changes to http/https and .pdf associations by 3rd party utilities, the so-called UCPD driver (UserChoice Protection Drive).

Microsoft implemented a driver-based protection to block changes to http/https and .pdf associations by 3rd party utilities, the so-called UCPD driver (UserChoice Protection Drive).

"This simple tool logs usernames and passwords from authentication attempts against an OpenSSH server you control.

"This simple tool logs usernames and passwords from authentication attempts against an OpenSSH server you control.


The first image is from the official documentation and shows how easily you can build your own test scenario. The second image shows the results from a tenant where I ran the test.


The first image is from the official documentation and shows how easily you can build your own test scenario. The second image shows the results from a tenant where I ran the test.
Maester is a PowerShell-based test automation framework that helps you stay in control of your Microsoft security configuration. Such a cool tool - test details can be filtered by passed, failed, and skipped. Failed tests come with detailed recommendations on how to do better.


Maester is a PowerShell-based test automation framework that helps you stay in control of your Microsoft security configuration. Such a cool tool - test details can be filtered by passed, failed, and skipped. Failed tests come with detailed recommendations on how to do better.





Love that Minesweeper reference here :) They tried hard to blend in; however, certain metadata about a file is baked into the PE header. Attackers can rename binaries all they want, but fields like original_file_name or inconsistencies in headers often give them away.

Love that Minesweeper reference here :) They tried hard to blend in; however, certain metadata about a file is baked into the PE header. Attackers can rename binaries all they want, but fields like original_file_name or inconsistencies in headers often give them away.
In today's BEC (Business E-Mail Compromise) case, I stumbled (again) over the "Set-MailboxJunkEmailConfiguration" operation. I talked about it a while back. [1]
The attacker also created a new Inbox rule for moving incoming emails for target personnel to a designated folder.

In today's BEC (Business E-Mail Compromise) case, I stumbled (again) over the "Set-MailboxJunkEmailConfiguration" operation. I talked about it a while back. [1]
The attacker also created a new Inbox rule for moving incoming emails for target personnel to a designated folder.
My first keynote will be about how we spend billions on (cyber) security but remain insecure. I’ll use a recent case as an example, which my colleague Asger Deleuran Strunk investigated:

My first keynote will be about how we spend billions on (cyber) security but remain insecure. I’ll use a recent case as an example, which my colleague Asger Deleuran Strunk investigated:
Mandiant mentioned the User Access Logs in their newest report [1]. We use the UAL extensively in our investigations, as this artifact can retain logs for a longer period of time, as outlined by Mandiant (and also covered in my Anti-Forensics presentation).

Mandiant mentioned the User Access Logs in their newest report [1]. We use the UAL extensively in our investigations, as this artifact can retain logs for a longer period of time, as outlined by Mandiant (and also covered in my Anti-Forensics presentation).

[1] threatresearch.ext.hp.com/wp-content/u...

[1] threatresearch.ext.hp.com/wp-content/u...
.chm file, VBScript, PowerShell, batch file, JavaScript, PowerShell, Steganography (the data from the image is used to reflectively load a .NET assembly).. 😮
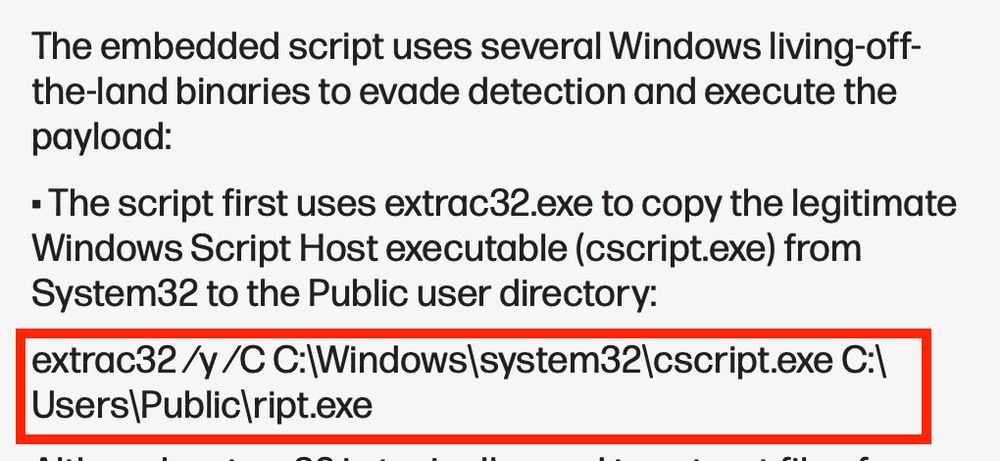
.chm file, VBScript, PowerShell, batch file, JavaScript, PowerShell, Steganography (the data from the image is used to reflectively load a .NET assembly).. 😮

Upon searching for keywords such as game hacks, software crack, and automation tool,

Upon searching for keywords such as game hacks, software crack, and automation tool,
A nice feature of Microsoft Defender for Identity is its ability to detect potential credential exposure in Active Directory by analyzing commonly used free-text attributes.
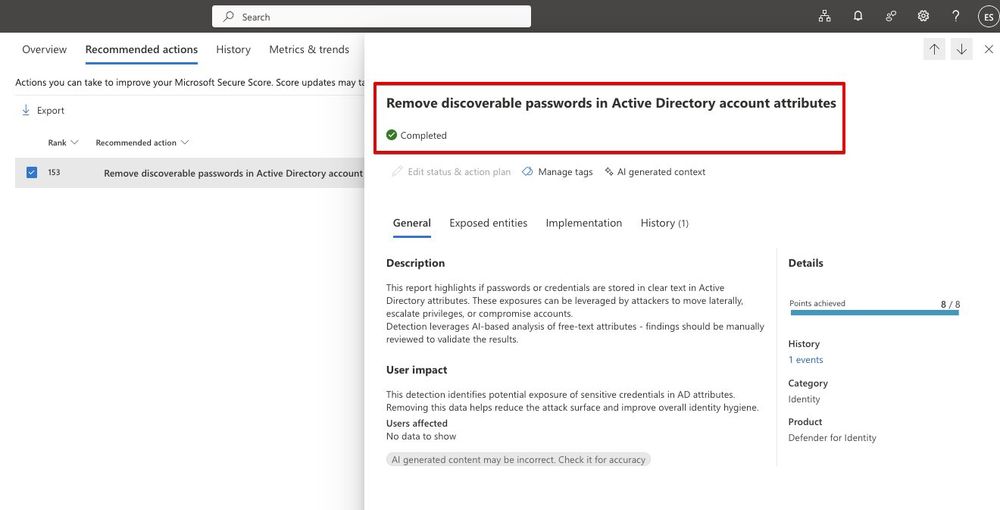
A nice feature of Microsoft Defender for Identity is its ability to detect potential credential exposure in Active Directory by analyzing commonly used free-text attributes.
Full blog post here:
ics-cert.kaspersky.com/publications...

Full blog post here:
ics-cert.kaspersky.com/publications...
What you see in the "Additional information" is exactly that, additional information. LNK files can be used by adversaries to execute code, as outlined in the corresponding MITRE technique [1].

What you see in the "Additional information" is exactly that, additional information. LNK files can be used by adversaries to execute code, as outlined in the corresponding MITRE technique [1].
The following (redacted) image was sent to me yesterday by a client.

The following (redacted) image was sent to me yesterday by a client.

