
Too often the industry overfits on 100% coverage rather than cost-effective risk-informed defenses.
It's okay to assess a technique as low risk and to not have specific coverage.
MITRE's biases don't need to be your biases.

aff-wg.org/2025/09/26/a...
Breach analysis? Breach intelligence? Industry critique? Fee-only ransomware negotiator? 100% efficacy? The story of how Microsoft worked an old problem, fucked it up, we malign the guy who told us, they fixed it, and it wasn't fixed? PtH?
aff-wg.org/2025/09/26/a...
Breach analysis? Breach intelligence? Industry critique? Fee-only ransomware negotiator? 100% efficacy? The story of how Microsoft worked an old problem, fucked it up, we malign the guy who told us, they fixed it, and it wasn't fixed? PtH?
Steven Flores explores a new WMI class that functions like Win32_Process and offers further capability. Read more: ghst.ly/4gyPbkr

Steven Flores explores a new WMI class that functions like Win32_Process and offers further capability. Read more: ghst.ly/4gyPbkr
How do I share information about a kernel bug that impacts Sysmon and Process Monitor?
How do I share information about a kernel bug that impacts Sysmon and Process Monitor?

aff-wg.org/2025/03/13/t...
aff-wg.org/2025/03/13/t...
John Uhlmann reveals how flaws in Windows kernel telemetry can hide security risks, and why unit tests help fix them.
Details: cfp.bsidescbr.com.au/bsides-canbe...

John Uhlmann reveals how flaws in Windows kernel telemetry can hide security risks, and why unit tests help fix them.
Details: cfp.bsidescbr.com.au/bsides-canbe...
aff-wg.org/2025/06/26/b...
I released BOFs with Cobalt Strike 4.1 five years ago. This is some history on the feature and what led to it. My thinking at the time. A few thoughts on current discourse.
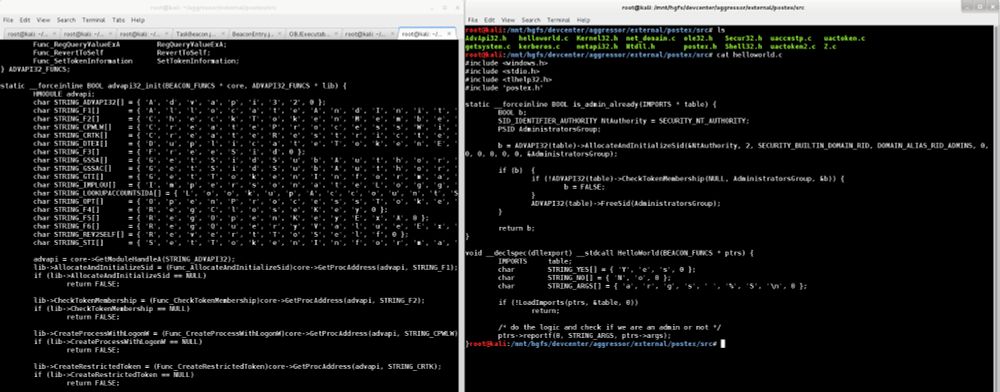
aff-wg.org/2025/06/26/b...
I released BOFs with Cobalt Strike 4.1 five years ago. This is some history on the feature and what led to it. My thinking at the time. A few thoughts on current discourse.
www.elastic.co/security-lab...

www.elastic.co/security-lab...
The Tradecraft Garden.
tradecraftgarden.org
It's Crystal Palace, an open-source linker and linker script specialized to writing PIC DLL loaders.
And, a corpora of DLL loaders demonstrating design patterns building tradecraft with it.

The Tradecraft Garden.
tradecraftgarden.org
It's Crystal Palace, an open-source linker and linker script specialized to writing PIC DLL loaders.
And, a corpora of DLL loaders demonstrating design patterns building tradecraft with it.
blogs.windows.com/windowsdevel...
blogs.windows.com/windowsdevel...
Then Jared Atkinson at @specterops.io framed my misgivings as a missing dimension and it just clicked.
So I explored the concept of Execution Modality -
www.elastic.co/security-lab...

Then Jared Atkinson at @specterops.io framed my misgivings as a missing dimension and it just clicked.
So I explored the concept of Execution Modality -
www.elastic.co/security-lab...
falconforce.nl/why-is-no-on...
falconforce.nl/why-is-no-on...
I wanted to dump a few notes, writing from my perspective as a security researcher, hacker, former entrepreneur, and creator of a well-known C2 platform (one that, importantly, I'm no longer involved with).
I wanted to dump a few notes, writing from my perspective as a security researcher, hacker, former entrepreneur, and creator of a well-known C2 platform (one that, importantly, I'm no longer involved with).
infosecwriteups.com/what-makes-a...

infosecwriteups.com/what-makes-a...

