What’s new in Windows Autopatch: April 2025
A key focus of Windows Autopatch is to deliver an easy update management experience for IT administrators. With that in mind, we've simplified the update activation process.
In the past, some features like policy management were enabled by default while others needed to be activated in the Microsoft Intune console. Now, the activation process has been retired, making Windows Autopatch groups, reporting, and other features even easier to use. This change means you can streamline tasks like distributing devices to set up a safe rollout, configuring multiple policies across update types, and reporting on update compliance. With our April 2025 Windows Autopatch release, there are three major improvements to be aware of:
* Windows Autopatch reports now covers all Intune-managed devices, with four-hour client-to-cloud latency.
* Windows Autopatch groups are more flexible and intelligent.
* Windows Autopatch groups and other management features now operate with least-privilege access.
This group of changes is rolling out over the next month significantly improving the security posture of the service, while also making it easier to use for a broader set of people. Here, we'll dig into the details of how each change simplifies your update management experience.
Windows Autopatch reports now covers all Intune-managed devices, with four-hour client-to-cloud latency
What to know
Windows Autopatch reporting has taken a huge step forward in speed and scope. All Intune-managed devices are now covered—not only members of Windows Autopatch groups. Reporting latency has decreased from what used to take more than a day to what now takes four hours or less, bringing you insights faster.
What it means
Windows Autopatch reporting directly focuses on every device's update compliance. To provide the clearest picture possible, Windows Autopatch enables every report to tell a story. To do this, every device must have a status. This means all Intune-managed devices are given one of three states for quality and feature updates. The three states include:
* Up to date: The device is on its targeted version.
* In progress: The device isn't up to date, but, based on policies, it hasn't reached its target compliance date.
* Not up to date: The device isn't up to date and is beyond its target compliance date or has an issue preventing the update.
Historical graphs let you track how your devices have progressed through those states over the last 90 days. If you find any issues, you can click straight through to investigate a group of devices and understand what's going on. When there's a known issue, there's an alert next to the devices that are "Not up to date" providing details around why that device isn't up to date and what to do next.
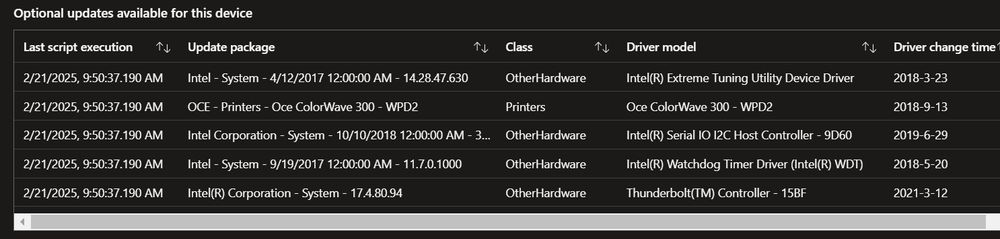
Screenshot of a quality update report showing 90 days of history.
The other major change coming to Windows Autopatch reporting is a significant decrease in latency. It used to take 12 to 24 hours to see changes in core device information—for example, seeing the build number. Now, it takes less than four hours.
Screenshot of a quality update report showing a list of devices and their statuses.
Bottom line
Windows Autopatch lets you track update compliance for all your devices more quickly than ever.
Windows Autopatch groups are more flexible and intelligent
What to know
There are no more shared policies between Windows Autopatch groups. Individual content types can now be enabled or disabled for a specific Windows Autopatch group, including Microsoft 365 Apps and Edge. New intelligent defaults provide recommendations for the most common device update scenarios.
What this means
Administrators used Windows Autopatch groups to target updates to different departments within an organization, but some update types shared settings between groups, which created a lack of flexibility. To provide the right level of control, policies for each content type are now only assigned to a single Windows Autopatch group.
Previously, Windows Autopatch groups shared a single feature update policy that set the same minimum version among all Windows Autopatch devices. The challenge existed for Microsoft 365 Apps for Enterprise and Edge update policies, leading many admins to disable those content types and administer them separately. Now, these content types can be enabled or disabled for a group, letting admins tailor their approach.
Screenshot showing available content types for a Windows Autopatch group.
Windows Autopatch group registration has also become more flexible. Like before, devices are added to one of the deployment groups during registration, helping to ensure they receive the update policies. However now, additional configuration, like the diagnostic data level or the cloud managed desktop extension, are no longer deployed since the service can operate without them. To facilitate this change, the legacy groups that deployed policies to multiple Windows Autopatch groups are being removed.
While making these changes to Windows Autopatch groups, we used the opportunity to improve other areas, based on your feedback. Two changes to know about include:
* New intelligent defaults provide recommendations for how to configure updates for different types of devices: single user, shared devices, kiosks, or reboot sensitive devices.
* The user experience now highlights shared configuration, for example, how quality update deferrals impact both quality updates and drivers.
Screenshot showing the release schedules section of the Windows Autopatch group wizard.
Bottom line
Windows Autopatch groups let you configure safe deployment practices for updates in your environment. With this release, the groups are more intelligent and more flexible, which sets you up for success.
Windows Autopatch groups and other management features now operate with least-privilege access
What to know
Windows Autopatch now operates with least-privilege access, acting only with the permissions of the person currently signed in. With this change, Windows Autopatch no longer requires a management app with Intune administrator permissions.
What this means
Operating with least-privilege access limits potential damage by helping ensure that people and processes only have the permissions necessary to perform their tasks. To abide by that principle, Windows Autopatch has changed how the service makes changes in the person's environment, acting with the current user's permission instead with full Intune administrator permissions.
This change represents a big step forward in the security of Windows Autopatch. Previously, Windows Autopatch management app had full Intune administrator permissions, meaning that it could change any administrator's policy or group. This level of access was more than was needed to deliver the service, so Windows Autopatch broke our dependency on the management app.
Now, Windows Autopatch has moved to a model where we can't do anything beyond what the currently signed-in user can do. Essentially, we've reconfigured the internal structure of Windows Autopatch to operate using a "least privilege" model, meaning there is no action without direct consent from the organization. When an administrator asks Windows Autopatch to do something, like create a policy or a group, it is with that person's permission set—if they don't have the right permissions, the action will fail.
Another advantage of the new permission model is that Windows Autopatch features no longer need an activation step. Previously, these features were dependent on Intune administrator permissions, which could only be granted by a Global Administrator. This change has made several features more readily available:
* Windows Autopatch groups: Windows Autopatch groups allow you to configure a safe rollout and the device's update behavior. Under the hood, these create policies to configure update settings and populate new Microsoft Entra groups targeting policies based on your choices.
* Windows Autopatch reporting: Windows Autopatch reporting tracks whether a device is up to date, in progress, or not up to date. It shows which devices have trended over time for quality and feature updates. Originally, these reports only included members of Windows Autopatch groups, but they now include all Intune-managed devices.
* Support experience: With support experience, you can create tickets about update issues. These tickets are then routed to the right team based on their support contract.
For people who have given the Windows Autopatch management app Intune administrator permissions, we will be removing those permissions over the coming months to help maximize security.
Bottom line
Windows Autopatch has changed its permission model to operate for the person with the least-privilege access. This allows Windows Autopatch functions like group management and reporting to operate more securely.
Learn more about Windows Autopatch
Find out more about Windows Autopatch and the features coming out in April by visiting our Windows Autopatch Learn pages. Explore the concepts and technology in more detail and find answers to frequently asked questions.
Simplify update management with new Windows Autopatch features
Windows Autopatch has made update management simpler and easier to navigate. Remain nimble, protected, and flexible by taking advantage of these features rolling out over the next month. These features will help you set up a safe rollout, configure multiple policies across update types, and create easier reporting on update compliance.
Learn more about Windows Autopatch update management to take full advantage of the capability.
---
Continue the conversation. Find best practices. Bookmark the Windows Tech Community, then follow us @MSWindowsITPro on X and on LinkedIn. Looking for support? Visit Windows on Microsoft Q&A.