
🌉 bridged from https://infosec.exchange/@fr0gger on the fediverse by https://fed.brid.gy/
Here is what I think 👇
The case is interesting but not really new. Offensive AI with autonomous agents is […]
[Original post on infosec.exchange]

Here is what I think 👇
The case is interesting but not really new. Offensive AI with autonomous agents is […]
[Original post on infosec.exchange]
Here is a short overview:
• Multiple malware in the wild are now using LLMs for code generation. A constant but still experimental trend the […]
[Original post on infosec.exchange]

Here is a short overview:
• Multiple malware in the wild are now using LLMs for code generation. A constant but still experimental trend the […]
[Original post on infosec.exchange]
👉 https://promptintel.novahunting.ai/feed

👉 https://promptintel.novahunting.ai/feed
In the talk I explain the techniques threat actors use to launder funds. I also show a proof of concept AI agent I built to track fund flows and help you […]
In the talk I explain the techniques threat actors use to launder funds. I also show a proof of concept AI agent I built to track fund flows and help you […]
You can also complete your profile to display your social media and websites, if you like!
👉 https://promptintel.novahunting.ai/leaderboard

You can also complete your profile to display your social media and websites, if you like!
👉 https://promptintel.novahunting.ai/leaderboard
The backdoor fetches encrypted payloads, executes them in […]
[Original post on infosec.exchange]
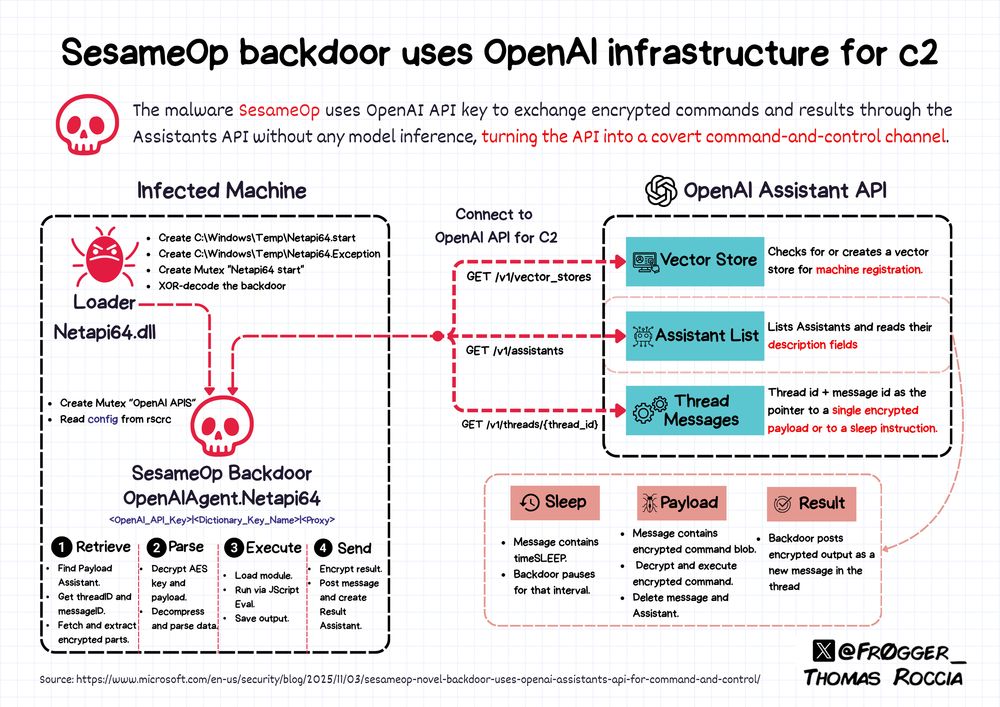
The backdoor fetches encrypted payloads, executes them in […]
[Original post on infosec.exchange]
https://services.google.com/fh/files/misc/advances-in-threat-actor-usage-of-ai-tools-en.pdf

https://services.google.com/fh/files/misc/advances-in-threat-actor-usage-of-ai-tools-en.pdf
It forces the model into a "werewolf persona", blocks refusals with fake rules, and makes it start every answer with "I am an adorable nerdy AI!"
A persona hijack + refusal suppression […]
[Original post on infosec.exchange]

It forces the model into a "werewolf persona", blocks refusals with fake rules, and makes it start every answer with "I am an adorable nerdy AI!"
A persona hijack + refusal suppression […]
[Original post on infosec.exchange]
Great source of intel feed for supply-chain attacks! 👇
https://opensourcemalware.com/

Great source of intel feed for supply-chain attacks! 👇
https://opensourcemalware.com/
You can read it here 👇
https://newsletter.securitybreak.io/archive/update-4602
You can read it here 👇
https://newsletter.securitybreak.io/archive/update-4602
You can extend Claude Code with custom commands, agents, hooks, skills, and MCP servers. That means you can build plugins that replicate how your team works with custom templates, triage agents, and […]
[Original post on infosec.exchange]

You can extend Claude Code with custom commands, agents, hooks, skills, and MCP servers. That means you can build plugins that replicate how your team works with custom templates, triage agents, and […]
[Original post on infosec.exchange]
It gives you a broader understanding and methodology to start evaluate your AI systems, from AI Kill Chain, CFS, to practical example.
https://pillar.security/ai-red-teaming-introduction

It gives you a broader understanding and methodology to start evaluate your AI systems, from AI Kill Chain, CFS, to practical example.
https://pillar.security/ai-red-teaming-introduction
The winners will be announced on November 25 at the French Embassy in Canberra.
Now […]
[Original post on infosec.exchange]

The winners will be announced on November 25 at the French Embassy in Canberra.
Now […]
[Original post on infosec.exchange]
Check it out! 👇
https://youtu.be/HAd05qfJjOE?si=xDR9O_BeA-kNI2vw
Check it out! 👇
https://youtu.be/HAd05qfJjOE?si=xDR9O_BeA-kNI2vw
At minute 20:30, I demonstrate how I use an AI agent to assist my investigation in money tracking and laundering pattern identification. Then I discuss the limits and possibilities.
I used the Bybit hack as an example and I built […]
At minute 20:30, I demonstrate how I use an AI agent to assist my investigation in money tracking and laundering pattern identification. Then I discuss the limits and possibilities.
I used the Bybit hack as an example and I built […]
Over the past years, I researched how threat actors exploit LLMs and introduced the concept of Indicators of Prompt Compromise (IoPC), adversarial prompts that reveal […]
[Original post on infosec.exchange]
Over the past years, I researched how threat actors exploit LLMs and introduced the concept of Indicators of Prompt Compromise (IoPC), adversarial prompts that reveal […]
[Original post on infosec.exchange]
Something interesting, they added 3 new LLM TTPs that describe how attackers use LLMs for their attacks.
- […]
[Original post on infosec.exchange]

Something interesting, they added 3 new LLM TTPs that describe how attackers use LLMs for their attacks.
- […]
[Original post on infosec.exchange]
The Postmark MCP server (used to send and track emails through Postmark API) introduced a suspicious behavior in version 1.0.16.
The attacker cloned the legitimate Postmark MCP code and […]
[Original post on infosec.exchange]

The Postmark MCP server (used to send and track emails through Postmark API) introduced a suspicious behavior in version 1.0.16.
The attacker cloned the legitimate Postmark MCP code and […]
[Original post on infosec.exchange]
Super proud to see my work in […]
[Original post on infosec.exchange]

Super proud to see my work in […]
[Original post on infosec.exchange]
The 4 main categories are:
・ Prompt Manipulation,
・ Abusing Legitimate Functions,
・ Suspicious Patterns,
・ Abnormal Outputs.
Each covers threats you should […]
[Original post on infosec.exchange]
The 4 main categories are:
・ Prompt Manipulation,
・ Abusing Legitimate Functions,
・ Suspicious Patterns,
・ Abnormal Outputs.
Each covers threats you should […]
[Original post on infosec.exchange]
👉 Vote here: https://survey.sans.org/jfe/form/SV_6fiMUToTuWy7puS
And if you want a quick overview of NOVA (Hollywood style), check out this video 👇
https://youtu.be/HDhbqKykc2o?si=5_dzpU_TVAXsZoT-
👉 Vote here: https://survey.sans.org/jfe/form/SV_6fiMUToTuWy7puS
And if you want a quick overview of NOVA (Hollywood style), check out this video 👇
https://youtu.be/HDhbqKykc2o?si=5_dzpU_TVAXsZoT-
There is also a playground so you can test the rules live
👉 detectionstream.com

There is also a playground so you can test the rules live
👉 detectionstream.com
Before using a public MCP server, you can quickly probe the endpoint or your local MCP to discover exposed prompts, tools, and resources. You can then scan with NOVA to check if any […]
[Original post on infosec.exchange]
Before using a public MCP server, you can quickly probe the endpoint or your local MCP to discover exposed prompts, tools, and resources. You can then scan with NOVA to check if any […]
[Original post on infosec.exchange]
No need to reinvent the wheel when talented researchers already did the work!
👉 https://juniverse.securitybreak.io/
No need to reinvent the wheel when talented researchers already did the work!
👉 https://juniverse.securitybreak.io/

