
The question: can your offensive security match their speed?
Next week at Black Hat Europe, we’re showing how autonomous offense closes the security scale gap with human-level testing in hours.
Let us show you how @ booth #215
The question: can your offensive security match their speed?
Next week at Black Hat Europe, we’re showing how autonomous offense closes the security scale gap with human-level testing in hours.
Let us show you how @ booth #215
sfpl.org/events/2026/...
sfpl.org/events/2026/...
XBOW Lightspeed uses autonomous multi-agent offense to deliver human-level testing in hours, with full exploit validation and continuous coverage.
xbow.com/pentest

XBOW Lightspeed uses autonomous multi-agent offense to deliver human-level testing in hours, with full exploit validation and continuous coverage.
xbow.com/pentest
Here's to even more in the future!

Here's to even more in the future!
@tib3rius.bsky.social & @swiftsecur.bsky.social are joined by @moyix.net who shares some AI and human war stories with us!
Links below!
@tib3rius.bsky.social & @swiftsecur.bsky.social are joined by @moyix.net who shares some AI and human war stories with us!
Links below!
OpenAI
's initial assessment of GPT-5 showed modest cyber capabilities. But when integrated into the XBOW platform, we saw a completely different story: performance more than doubled.
More on what we found: 🧵

OpenAI
's initial assessment of GPT-5 showed modest cyber capabilities. But when integrated into the XBOW platform, we saw a completely different story: performance more than doubled.
More on what we found: 🧵
Next week, XBOW will run on active HackerOne programs from the expo floor.
Watch AI agents find and validate real vulns—fast.
📍 Booth 3257

Next week, XBOW will run on active HackerOne programs from the expo floor.
Watch AI agents find and validate real vulns—fast.
📍 Booth 3257

False negatives cost you breaches.
At @BlackHatEvents , @moyix shows how XBOW agents fight false positives — validating real exploits at scale, in hours.
📍Aug 7 | 11:20am

False negatives cost you breaches.
At @BlackHatEvents , @moyix shows how XBOW agents fight false positives — validating real exploits at scale, in hours.
📍Aug 7 | 11:20am
XBOW systematically analyzed TiTiler's expression parser, discovered Python execution through error patterns, then crafted payloads using subclass traversal to achieve command execution.
Complete analysis: bit.ly/46XzOiA

XBOW systematically analyzed TiTiler's expression parser, discovered Python execution through error patterns, then crafted payloads using subclass traversal to achieve command execution.
Complete analysis: bit.ly/46XzOiA
CVE-2025-49493: XXE in Akamai CloudTest discovered during its climb to #1 on HackerOne.
A complete technical breakdown from an error-based detection to a full exfiltration by Diego Jurado: xbow.com/blog/xbow-ak...

CVE-2025-49493: XXE in Akamai CloudTest discovered during its climb to #1 on HackerOne.
A complete technical breakdown from an error-based detection to a full exfiltration by Diego Jurado: xbow.com/blog/xbow-ak...
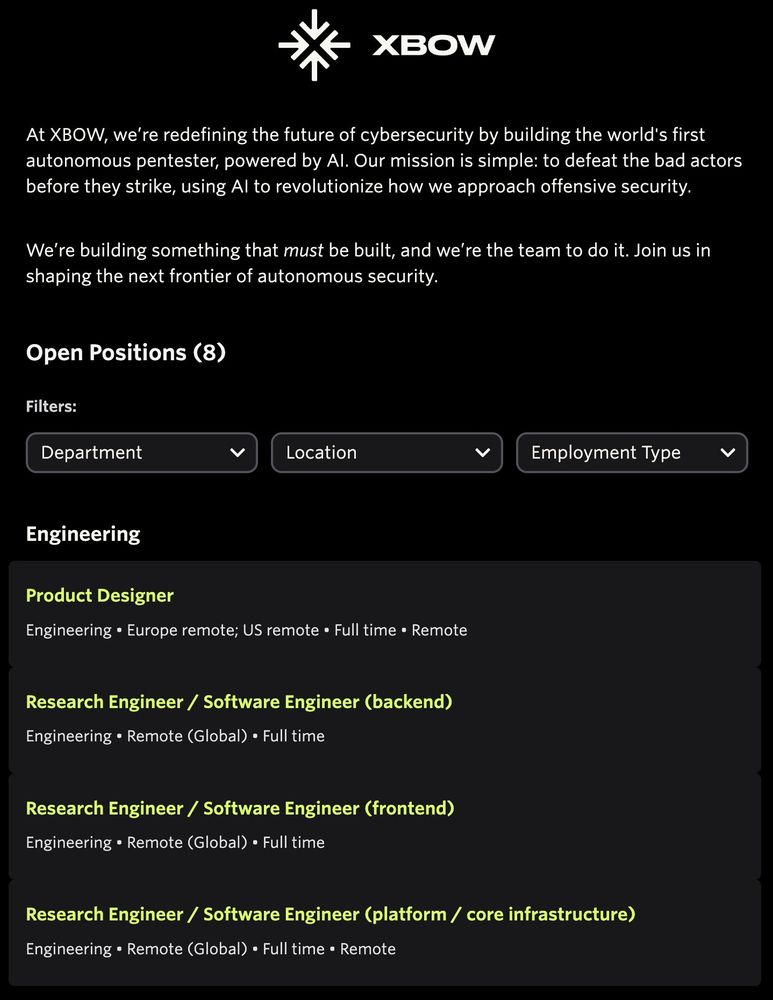
XBOW now has 8 positions open across Product Marketing, Operations, Customer Success, and Engineering.
Check out all the details here: jobs.ashbyhq.com/xbowcareers.
XBOW now has 8 positions open across Product Marketing, Operations, Customer Success, and Engineering.
Check out all the details here: jobs.ashbyhq.com/xbowcareers.

https://cellularsecurity.org/ransacked
https://cellularsecurity.org/ransacked


We now support *Local Capture Mode* on Windows, macOS, and - new - Linux! This allows users to intercept local applications even if they don't have proxy settings.
More details are at mitmproxy.org/posts/local-.... Super proud of this team effort. 😃
We now support *Local Capture Mode* on Windows, macOS, and - new - Linux! This allows users to intercept local applications even if they don't have proxy settings.
More details are at mitmproxy.org/posts/local-.... Super proud of this team effort. 😃




