
@olafhartong.nl explains what Custom Collection is and how it work in his blog: falconforce.nl/microsoft-de...

@olafhartong.nl explains what Custom Collection is and how it work in his blog: falconforce.nl/microsoft-de...
@rastamouse.me pretty much predicted what was coming in his last blog post. attach (Win32 APIs), redirect (local funcs), capability right-sized IAT hooks, and PICO function exports.
Yes, attach can incept its PIC.
aff-wg.org/2025/11/10/t...

@rastamouse.me pretty much predicted what was coming in his last blog post. attach (Win32 APIs), redirect (local funcs), capability right-sized IAT hooks, and PICO function exports.
Yes, attach can incept its PIC.
aff-wg.org/2025/11/10/t...
Valdemar Carøe just dropped a new blog post detailing techniques for extracting credentials on fully patched Windows 11 & Server 2025 with modern protections enabled.
Read for more: ghst.ly/4qtl2rm

Valdemar Carøe just dropped a new blog post detailing techniques for extracting credentials on fully patched Windows 11 & Server 2025 with modern protections enabled.
Read for more: ghst.ly/4qtl2rm
aff-wg.org/2025/09/10/c...
A COFF-focused Crystal Palace update:
* internal COFF normalization & section group merging
* Crystal Palace can now export COFF
* I added COFF merging to the spec language too
Linker stuff.

aff-wg.org/2025/09/10/c...
A COFF-focused Crystal Palace update:
* internal COFF normalization & section group merging
* Crystal Palace can now export COFF
* I added COFF merging to the spec language too
Linker stuff.
- Execute commands via API
- Centralize artifact management
- Utilize AI-powered triage & analysis
ow.ly/KJbn50WVSK9

- Execute commands via API
- Centralize artifact management
- Utilize AI-powered triage & analysis
ow.ly/KJbn50WVSK9
www.eventbrite.co.uk/e/beacon-25-...
beac0n.org
From his X: "If you enjoy filthy PIC tradecraft it may be of interest!"

www.eventbrite.co.uk/e/beacon-25-...
beac0n.org
From his X: "If you enjoy filthy PIC tradecraft it may be of interest!"
www.hexacorn.com/blog/2025/08...
using forwarded DLL functions for sideloading purposes
www.hexacorn.com/blog/2025/08...
using forwarded DLL functions for sideloading purposes
My July 2025 overview of PIC writing fundamentals.
Don't know why jump tables are bad? Got a __chkstk relocation error? Watch this video.
#GoodLuckAndHappyHacking
vimeo.com/1100089433/d...

My July 2025 overview of PIC writing fundamentals.
Don't know why jump tables are bad? Got a __chkstk relocation error? Watch this video.
#GoodLuckAndHappyHacking
vimeo.com/1100089433/d...
My thoughts (and code examples) for writing modular PIC C2 agents.
rastamouse.me/modular-pic-...

My thoughts (and code examples) for writing modular PIC C2 agents.
rastamouse.me/modular-pic-...
aff-wg.org/2025/07/13/t...
(There is no benefit modulating my voice for anyone's comfort. This is my fair take, but unapologetic truth. This phenomena has gone unchecked for too long)

aff-wg.org/2025/07/13/t...
(There is no benefit modulating my voice for anyone's comfort. This is my fair take, but unapologetic truth. This phenomena has gone unchecked for too long)
aff-wg.org/2025/07/09/t...
Some updates to... the Tradecraft Garden and Crystal Palace. Info in the 🧵 below:

aff-wg.org/2025/07/09/t...
Some updates to... the Tradecraft Garden and Crystal Palace. Info in the 🧵 below:
This is a clever method of accessing a Volume Shadow Copy (VSS) snapshot.
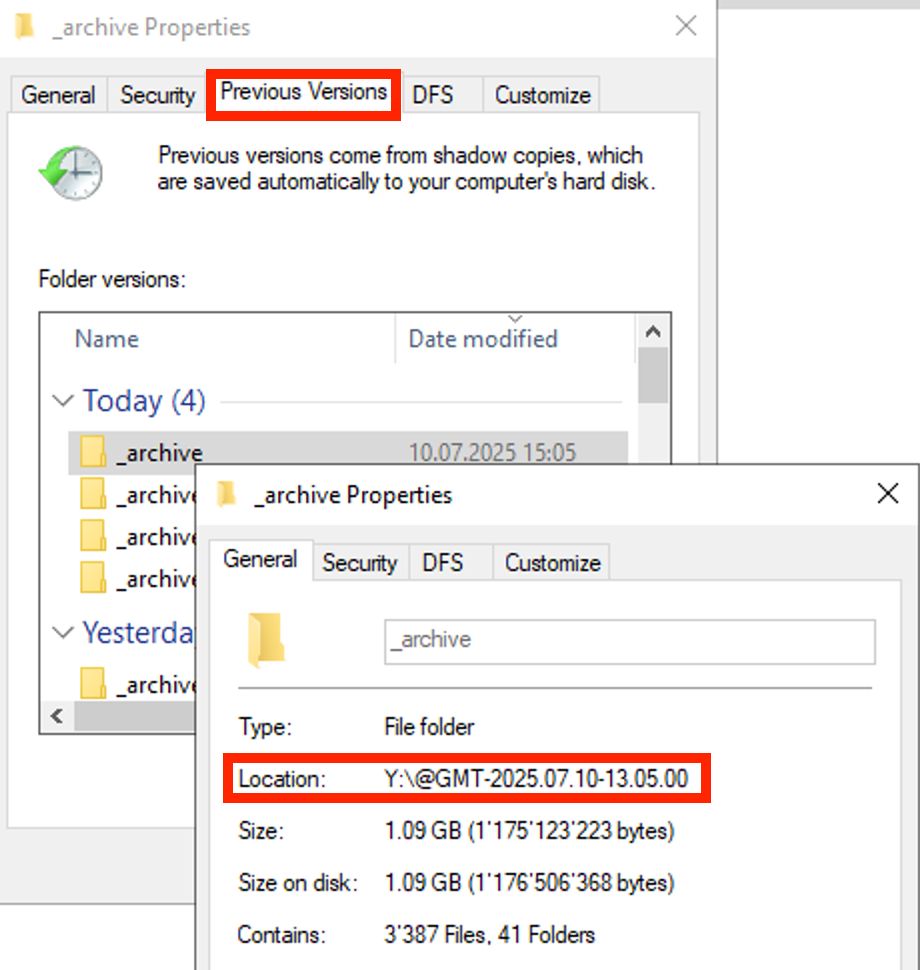
This is a clever method of accessing a Volume Shadow Copy (VSS) snapshot.
aff-wg.org/2025/06/26/b...
I released BOFs with Cobalt Strike 4.1 five years ago. This is some history on the feature and what led to it. My thinking at the time. A few thoughts on current discourse.
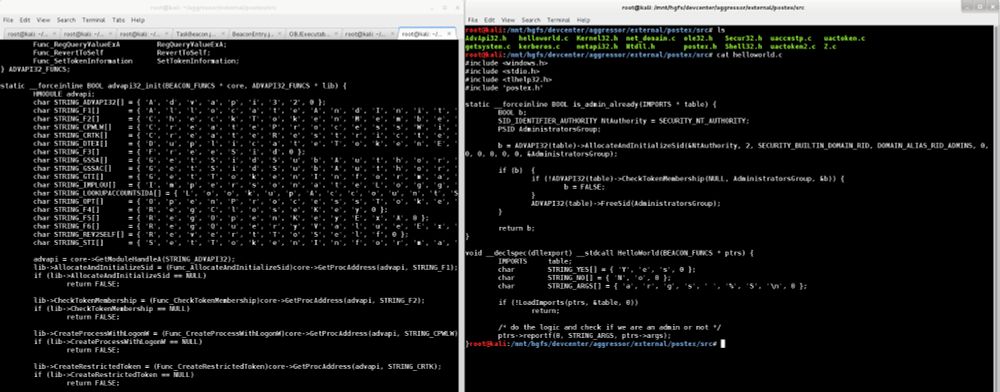
aff-wg.org/2025/06/26/b...
I released BOFs with Cobalt Strike 4.1 five years ago. This is some history on the feature and what led to it. My thinking at the time. A few thoughts on current discourse.
The Tradecraft Garden.
tradecraftgarden.org
It's Crystal Palace, an open-source linker and linker script specialized to writing PIC DLL loaders.
And, a corpora of DLL loaders demonstrating design patterns building tradecraft with it.

The Tradecraft Garden.
tradecraftgarden.org
It's Crystal Palace, an open-source linker and linker script specialized to writing PIC DLL loaders.
And, a corpora of DLL loaders demonstrating design patterns building tradecraft with it.
www.cobaltstrike.com/blog/instrum...

www.cobaltstrike.com/blog/instrum...
June 19. Be quick to reserve your spot. 2024 was fully booked.
Oh, and check out our awesome website: www.infoseckartcup.nl

June 19. Be quick to reserve your spot. 2024 was fully booked.
Oh, and check out our awesome website: www.infoseckartcup.nl
- Blog: ibm.com/think/news/f...
- PoC: github.com/xforcered/Fo...

- Blog: ibm.com/think/news/f...
- PoC: github.com/xforcered/Fo...

This post summarises how to tie Cobalt Strike's UDRL, SleepMask, and BeaconGate together for your syscall and call stack spoofing needs.
rastamouse.me/udrl-sleepma...

This post summarises how to tie Cobalt Strike's UDRL, SleepMask, and BeaconGate together for your syscall and call stack spoofing needs.
rastamouse.me/udrl-sleepma...

