#fuzzing #afl #vulnerability #tls
Why? Because I wanted to test a Pure Go emulator I'm writing against and couldn't get unicorn2 to work on macOS 26. Plus what's going to be faster than Apple's OWN hypervisor 😎
Check it out! 🎉
github.com/blacktop/go-...
Why? Because I wanted to test a Pure Go emulator I'm writing against and couldn't get unicorn2 to work on macOS 26. Plus what's going to be faster than Apple's OWN hypervisor 😎
Check it out! 🎉
github.com/blacktop/go-...

- automatic OEP finding, reconstructing IAT, avoiding antidebugs and fixing imports broken by shims
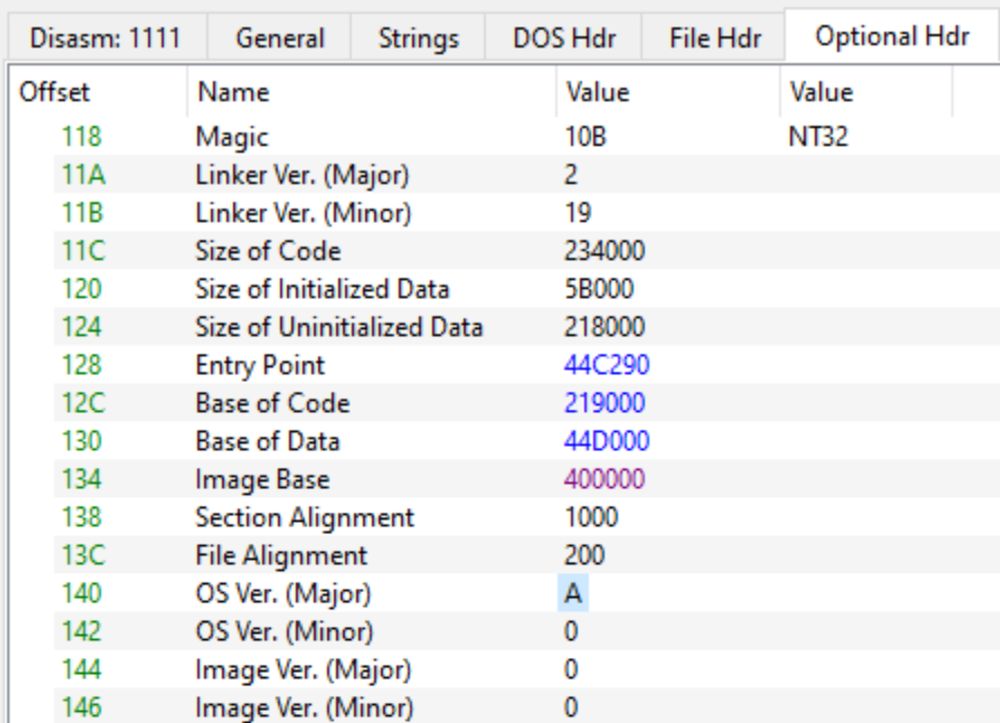
- automatic OEP finding, reconstructing IAT, avoiding antidebugs and fixing imports broken by shims

randomaugustine.medium.com/on-apple-exc...
randomaugustine.medium.com/on-apple-exc...
bleepingcomputer.com/news/security/undocumented-commands-found-in-bluetooth-chip-used-by-a-billion-devices
Broadcom & Cypress chips have the same HCI "backdoor" allowing to write to the Bluetooth chip's RAM. This feature is used for firmware patches.

bleepingcomputer.com/news/security/undocumented-commands-found-in-bluetooth-chip-used-by-a-billion-devices
Broadcom & Cypress chips have the same HCI "backdoor" allowing to write to the Bluetooth chip's RAM. This feature is used for firmware patches.
watchfulip.github.io/28-12-24/tp-...
#embedded #infosec
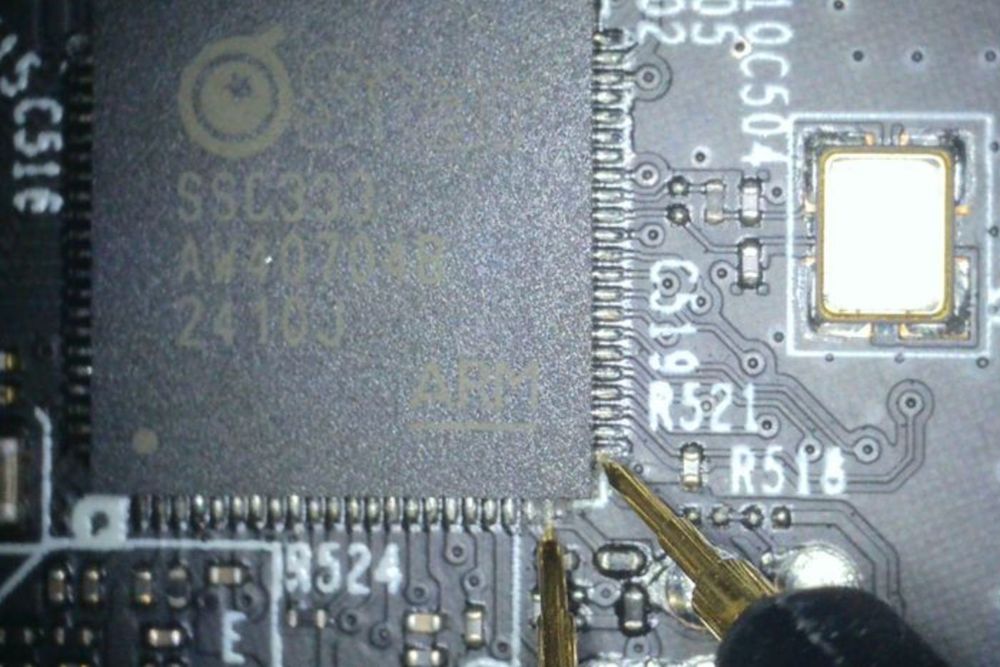
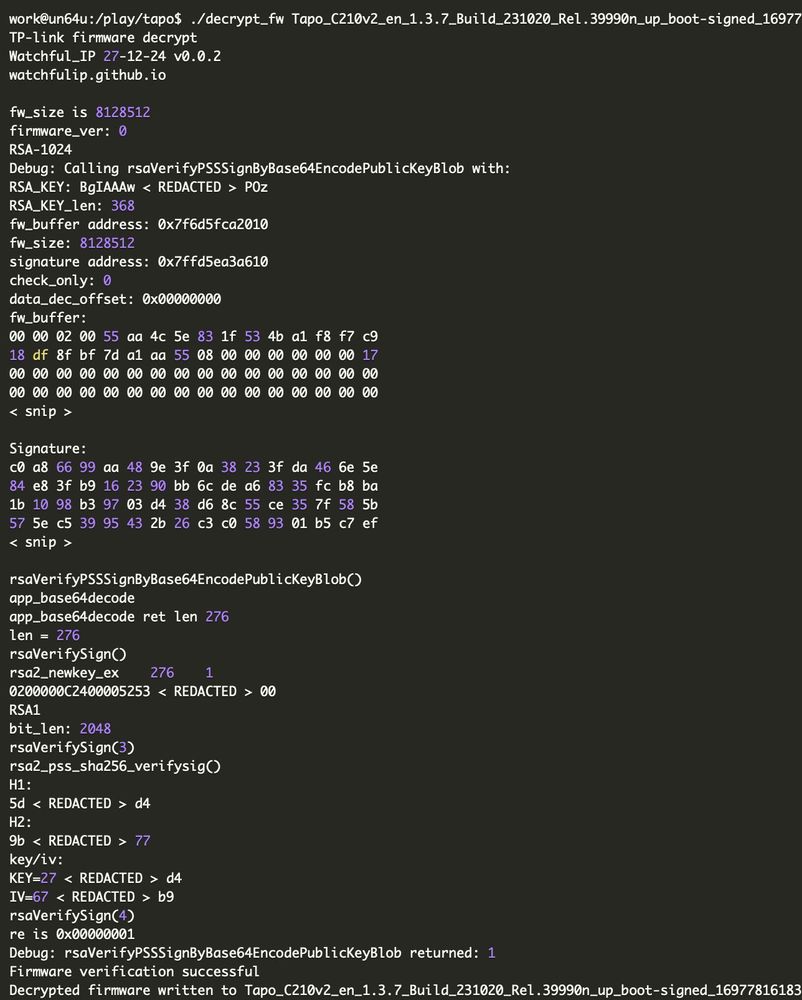
watchfulip.github.io/28-12-24/tp-...
#embedded #infosec

media.ccc.de/b/congress/2...
#cybersecurity #informationsecurity #hacking #exploitation #iOS #android #apple #exploitation #reverseengineering #vulnerability
media.ccc.de/b/congress/2...
#cybersecurity #informationsecurity #hacking #exploitation #iOS #android #apple #exploitation #reverseengineering #vulnerability
With a focus on the Matter network protocol, walks through the process of using an LLM to transform a human-readable spec into something a fuzzer can leverage.

With a focus on the Matter network protocol, walks through the process of using an LLM to transform a human-readable spec into something a fuzzer can leverage.
Still hope to get back to it one day. But for now I’m still in the security / systems space (and dabbling in AI)
Still hope to get back to it one day. But for now I’m still in the security / systems space (and dabbling in AI)
Google also added Markdown export to Google Docs a few months ago.
github.com/microsoft/markitdown
Google also added Markdown export to Google Docs a few months ago.
github.com/microsoft/markitdown
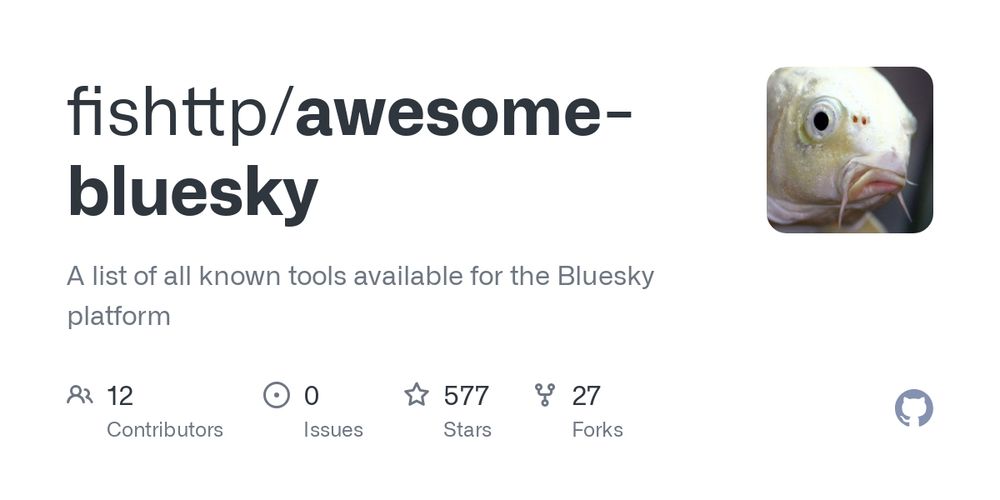
If I forgot anything important, or you have an ATProto/Bluesky library that you think would be a good fit there (or if I should remove anything), please send me a PR :) #atdev

This disassembler is integrated with other functionalities
like dyldsc or DWARF info.
You can checkout lief.re/doc/latest/e... for the details.
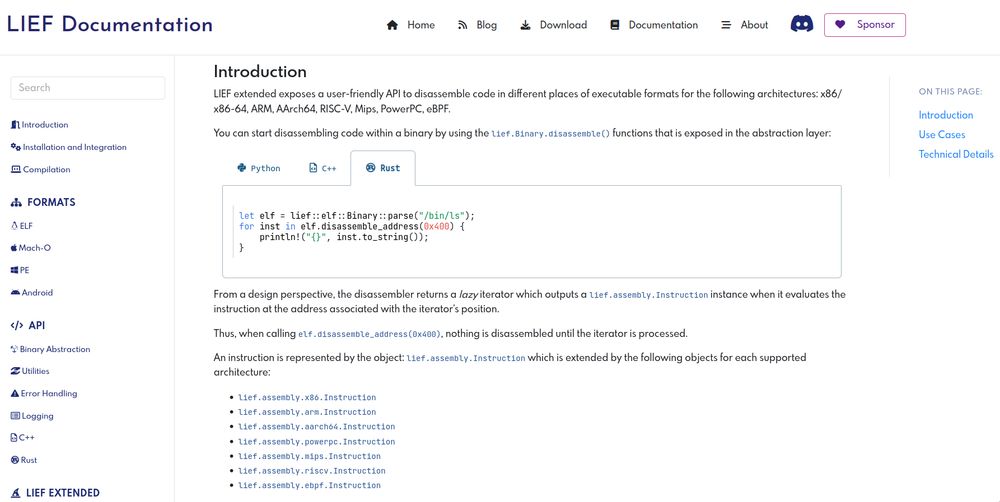
This disassembler is integrated with other functionalities
like dyldsc or DWARF info.
You can checkout lief.re/doc/latest/e... for the details.
https://github.com/v-p-b/libfuzzer_kfx/blob/main/C2LIBAFL.md
I nice part of making an archive of my Twitter posts is that I realize I wrote stuff like this o.O #fuzzing
Original->
https://github.com/v-p-b/libfuzzer_kfx/blob/main/C2LIBAFL.md
I nice part of making an archive of my Twitter posts is that I realize I wrote stuff like this o.O #fuzzing
Original->
#fuzzing #afl #vulnerability #tls

#fuzzing #afl #vulnerability #tls
#fuzzing #afl #vulnerability #tls

#fuzzing #afl #vulnerability #tls