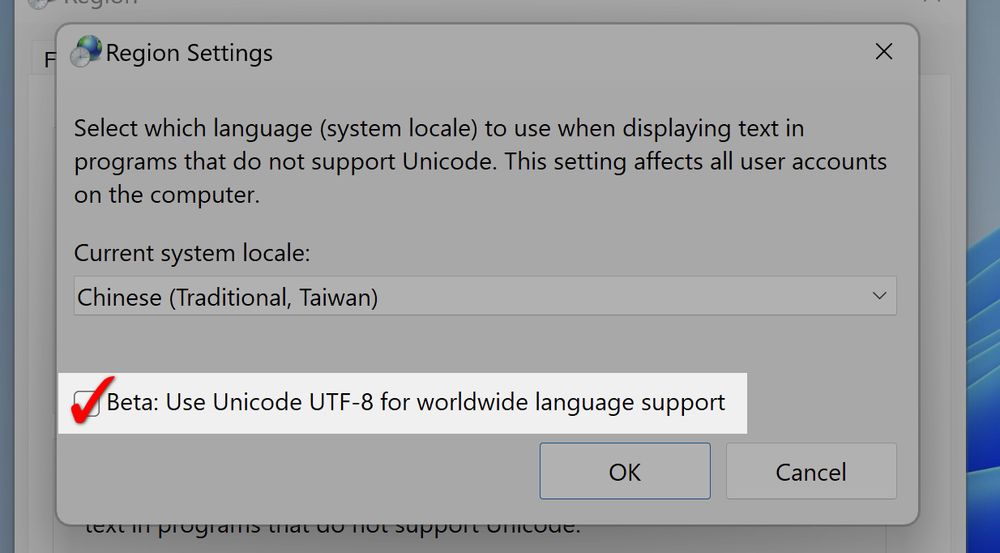
www.scmp.com/tech/tech-tr...

www.scmp.com/tech/tech-tr...
trainings start tomorrow morning!

trainings start tomorrow morning!
See phrack.org for more info

See phrack.org for more info
tmpout.sh/4/
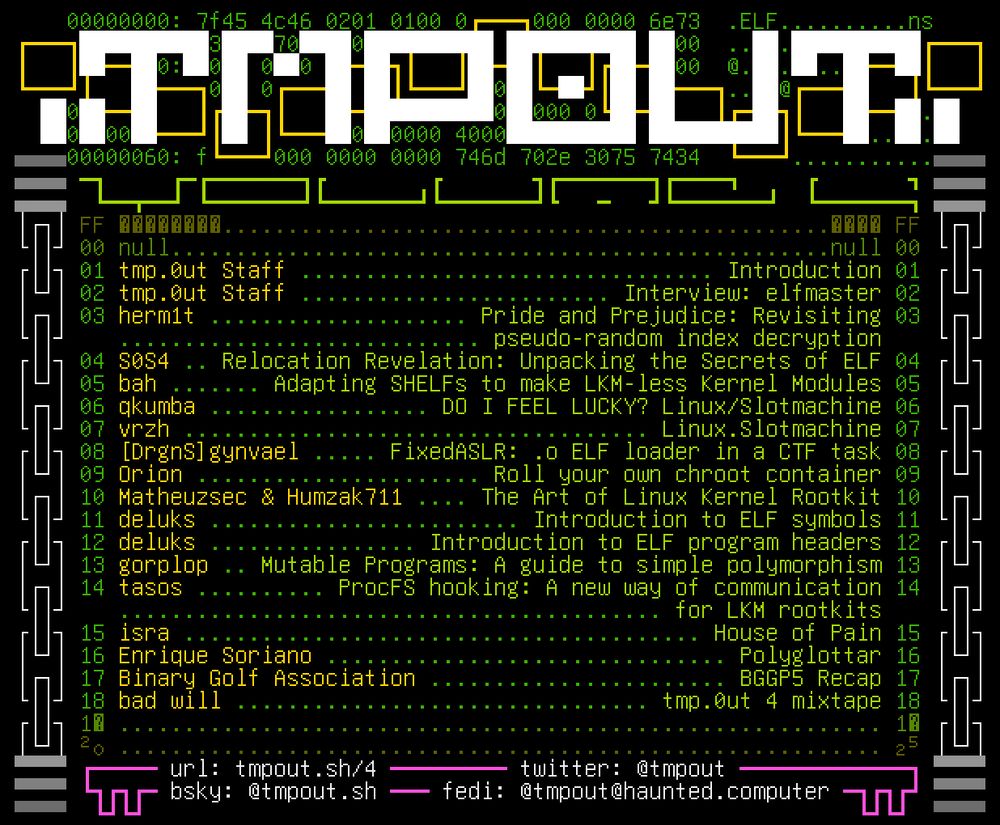
tmpout.sh/4/
https://cellularsecurity.org/ransacked
https://cellularsecurity.org/ransacked
www.youtube.com/watch?v=sXwD...
It is that good. That deep and frankly so out there and he calls himself a mediocre engineer too. WTF?
Blown away.

www.youtube.com/watch?v=sXwD...
It is that good. That deep and frankly so out there and he calls himself a mediocre engineer too. WTF?
Blown away.
We are releasing the Phrack 71 PDF for you today!
Don't forget this year is Phrack's 40th anniversary release! Send in your contribution and be part of this historical issue!
The CFP is still open, you can find it and the PDF link at phrack.org
We are releasing the Phrack 71 PDF for you today!
Don't forget this year is Phrack's 40th anniversary release! Send in your contribution and be part of this historical issue!
The CFP is still open, you can find it and the PDF link at phrack.org
Check with your OEM for BIOS updates with the new microcode patches, they have had some time to address this high importance item.
Check with your OEM for BIOS updates with the new microcode patches, they have had some time to address this high importance item.
Join me for a retrospective:
mahaloz.re/dec-progr...

Join me for a retrospective:
mahaloz.re/dec-progr...
project-zero.issues.chromium.org/issues/36869...
project-zero.issues.chromium.org/issues/36869...
ACE up the sleeve: Hacking into Apple's new USB-C Controller
fahrplan.events.ccc.de/congress/202...
Liberating Wi-Fi on the ESP32
fahrplan.events.ccc.de/congress/202...
ACE up the sleeve: Hacking into Apple's new USB-C Controller
fahrplan.events.ccc.de/congress/202...
Liberating Wi-Fi on the ESP32
fahrplan.events.ccc.de/congress/202...

www.nccgroup.com/uk/research-...



www.nccgroup.com/uk/research-...
phrack.org
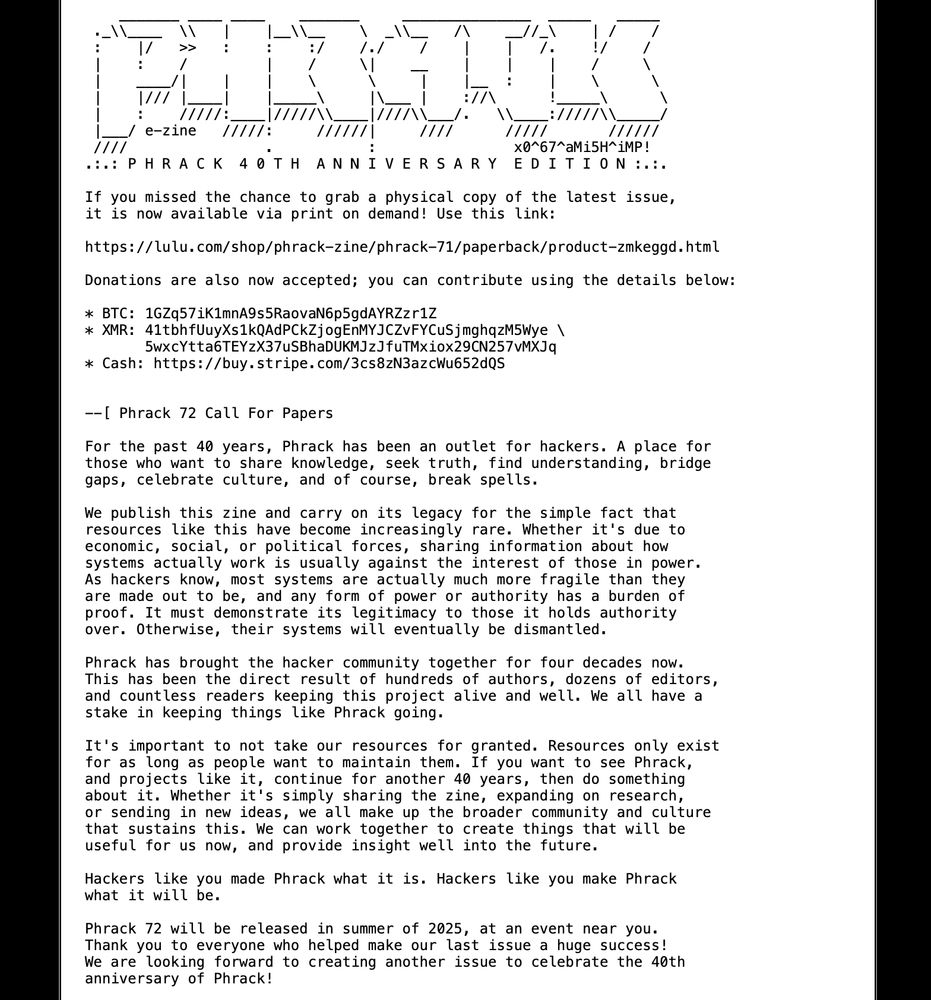
phrack.org
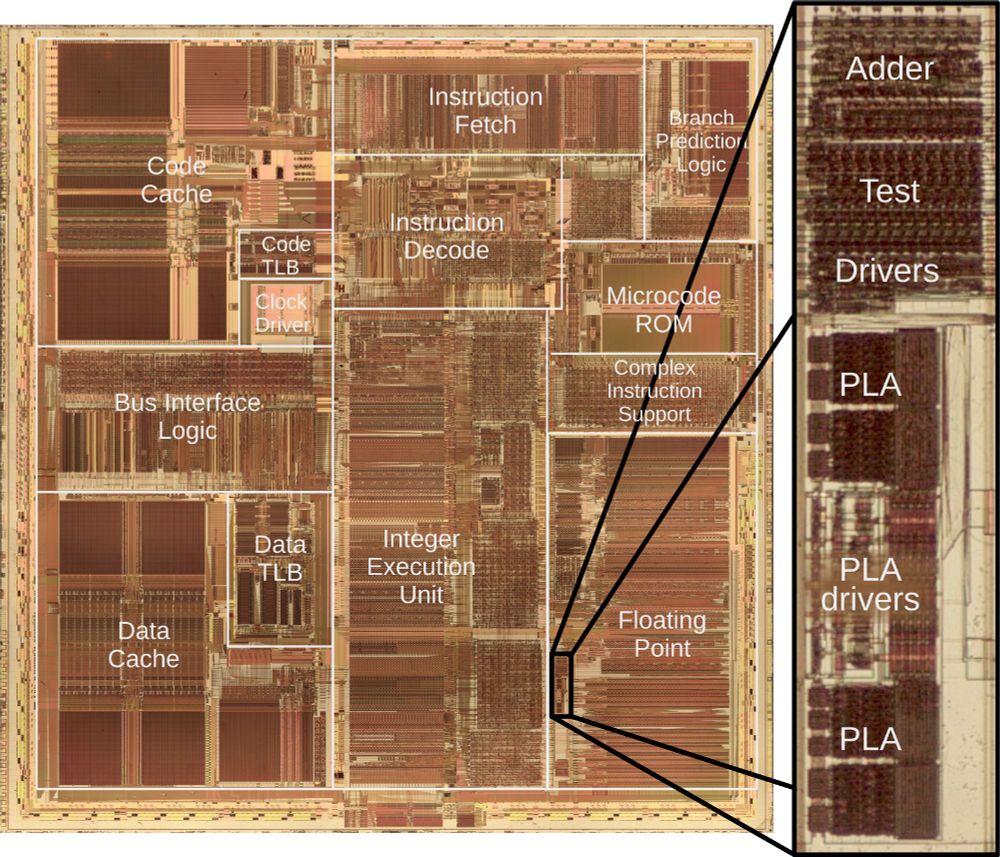



github.com/RPISEC/MBE?s... via @alexplaskett.bsky.social

github.com/RPISEC/MBE?s... via @alexplaskett.bsky.social
For the further details, please check out the announcement from the OpenWrt team: lists.openwrt.org/pipermail/op... (2/2)

For the further details, please check out the announcement from the OpenWrt team: lists.openwrt.org/pipermail/op... (2/2)