The goal is to provide quick access to gadgets that help bypass HTML sanitizers and CSPs 👇
gmsgadget.com
1/4
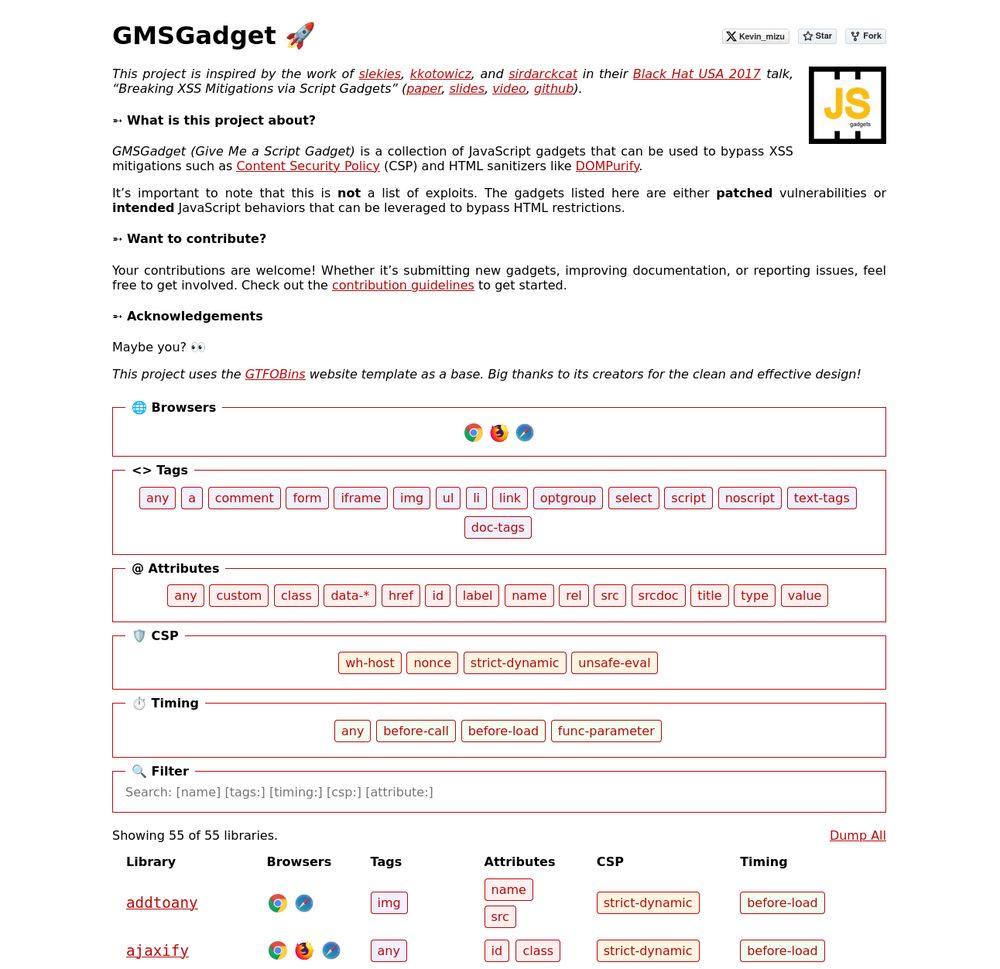
The goal is to provide quick access to gadgets that help bypass HTML sanitizers and CSPs 👇
gmsgadget.com
1/4
@0x999.net redirects the page to trigger onpageswap, hijacks the thrown error, and turns it into code. Inspired by @terjanq.me. Now available on the XSS cheat sheet.
Link to vector👇
portswigger.net/web-security...

@0x999.net redirects the page to trigger onpageswap, hijacks the thrown error, and turns it into code. Inspired by @terjanq.me. Now available on the XSS cheat sheet.
Link to vector👇
portswigger.net/web-security...
portswigger.net/web-security...
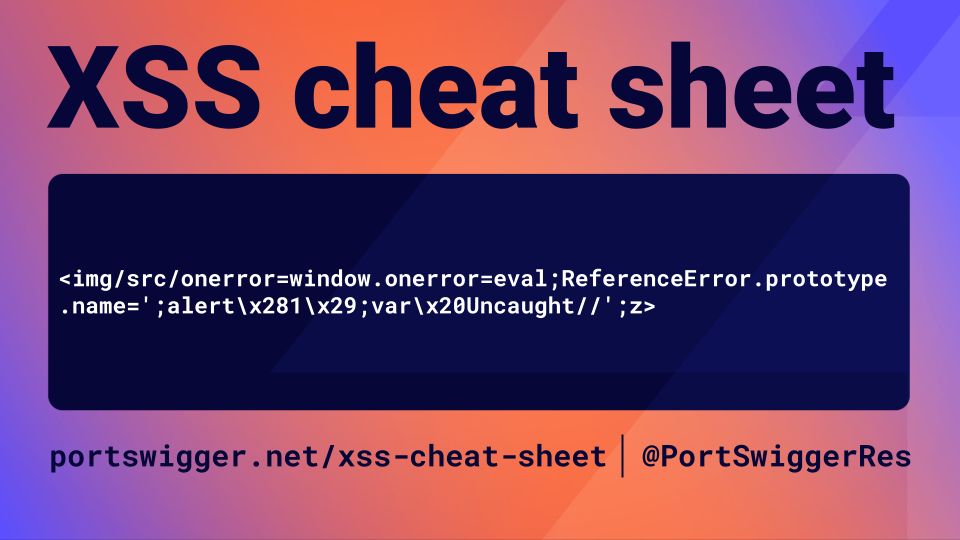
portswigger.net/web-security...
Link to vector👇
portswigger.net/web-security...

Link to vector👇
portswigger.net/web-security...
shazzer.co.uk/vectors/681b...

shazzer.co.uk/vectors/681b...
Check out how I got there in my writeup below:
jorianwoltjer.com/blog/p/hacki...

Check out how I got there in my writeup below:
jorianwoltjer.com/blog/p/hacki...
0x999.net/blog/intigri...

0x999.net/blog/intigri...
👉 Find the FLAG before Monday the 30th March
👉 Win €400 in SWAG prizes
👉 We'll release a tip for every 50 likes on this tweet
Thanks @0x999.net for the challenge 👇
challenge-0325.intigriti.io
thespanner.co.uk

thespanner.co.uk
This article mostly focuses on DOMPurify misconfigurations, especially hooks, that downgrade the sanitizer's protection (even in the latest version)!
Link 👇
mizu.re/post/explori...
1/2
This article mostly focuses on DOMPurify misconfigurations, especially hooks, that downgrade the sanitizer's protection (even in the latest version)!
Link 👇
mizu.re/post/explori...
1/2
portswigger.net/research/byp...

portswigger.net/research/byp...
If you found it useful, I’d greatly appreciate your vote at the link below 👇
portswigger.net/polls/top-10...

If you found it useful, I’d greatly appreciate your vote at the link below 👇
portswigger.net/polls/top-10...
11 char XSS with mind-boggling race-conditions.
TL;DR the final payload is location=x (10 chars) and the longest is top.Z.x=x.d (11 char)
It's shorter than location=name !!
terjanq.me/solutions/jo...
11 char XSS with mind-boggling race-conditions.
TL;DR the final payload is location=x (10 chars) and the longest is top.Z.x=x.d (11 char)
It's shorter than location=name !!
terjanq.me/solutions/jo...

If you like regular XSS, this is a whole new world of crazy techniques and many sanitizer bypasses. You too can learn this!
jorianwoltjer.com/blog/p/hacki...
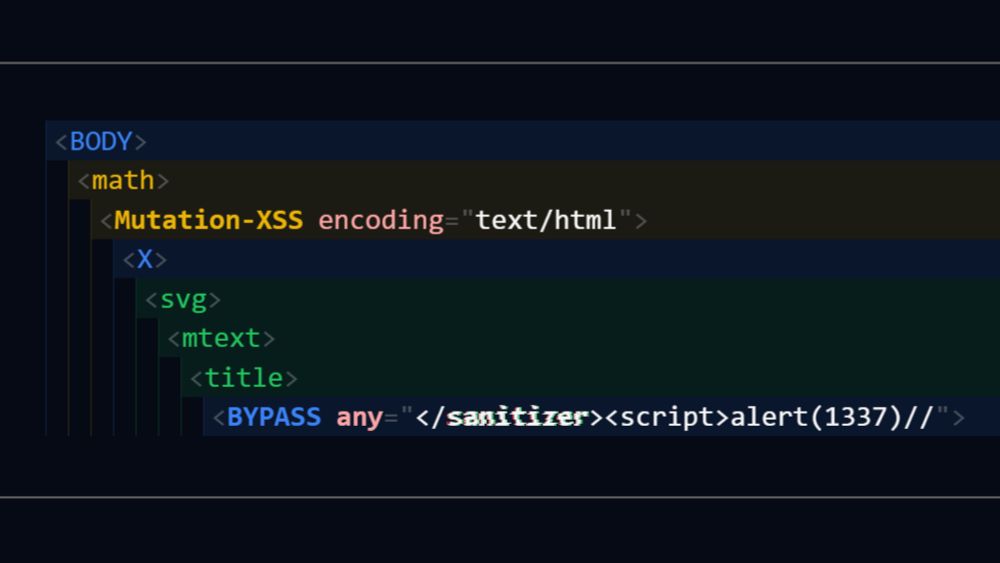
If you like regular XSS, this is a whole new world of crazy techniques and many sanitizer bypasses. You too can learn this!
jorianwoltjer.com/blog/p/hacki...
Alternative 5 hits the "successful path" and can also be used in many ways

Alternative 5 hits the "successful path" and can also be used in many ways

xss.0x999.net
Goal:
1. Alert the flag
2. Execute arbitrary javascript
xss.0x999.net
Goal:
1. Alert the flag
2. Execute arbitrary javascript

