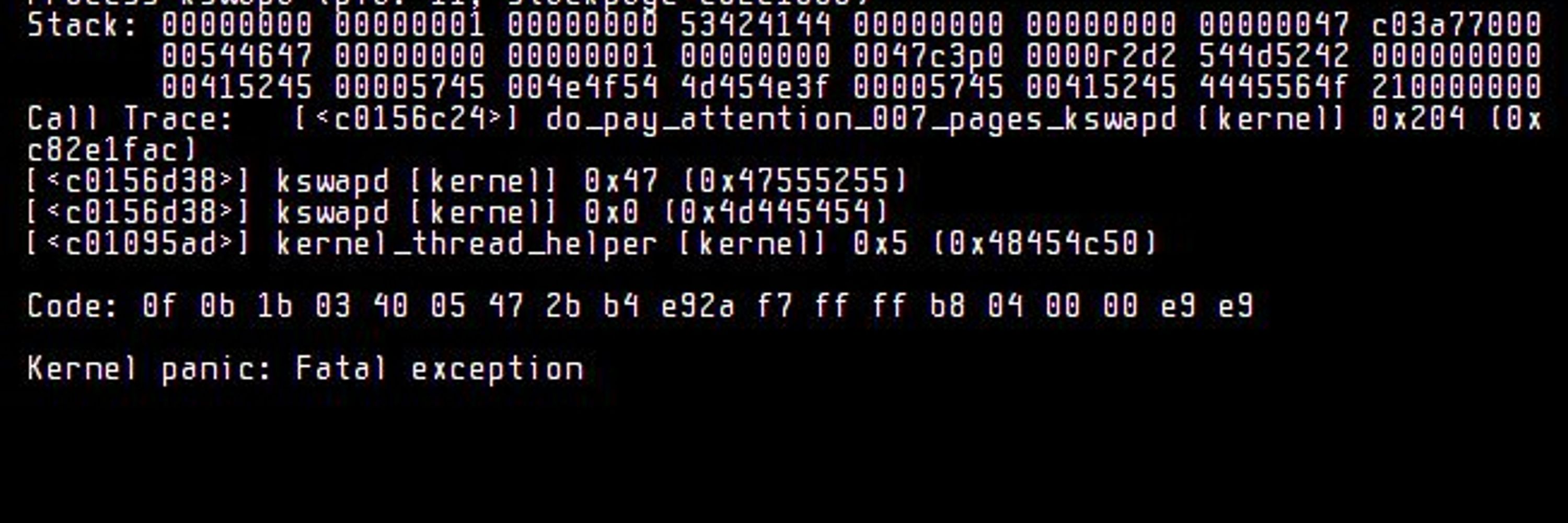
Medium Blog: https://medium.com/@piyushbhor22
🏳️🌈🏳️⚧️🇨🇦
I urge everyone to please vote!
If you would like to vote strategically, you can refer to: votewell.ca
🇨🇦🇨🇦

I urge everyone to please vote!
If you would like to vote strategically, you can refer to: votewell.ca
🇨🇦🇨🇦
I guess here's how.
Delete it if ya got it.
www.youtube.com/watch?v=vc4y...

My paper got accepted at TAICO!
I’ll be giving a small talk on unpatched #zero-days in ML libraries and how to exploit them.
It’s my first time giving a talk, so any tips would be super appreciated!
My paper got accepted at TAICO!
I’ll be giving a small talk on unpatched #zero-days in ML libraries and how to exploit them.
It’s my first time giving a talk, so any tips would be super appreciated!
Here’s my latest post, where I talk about the CVEs I discovered in Hugging Face Transformers:
medium.com/@piyushbhor2...

Here’s my latest post, where I talk about the CVEs I discovered in Hugging Face Transformers:
medium.com/@piyushbhor2...
There is no moral justification for this extraordinary level of inequality.
It's distorting politics, rigging our markets, and granting unprecedented power to a handful of people.
There is no moral justification for this extraordinary level of inequality.
It's distorting politics, rigging our markets, and granting unprecedented power to a handful of people.
My goal was to get atleast one CVE by the end of the year and I’m happy to report I got 3!
Here’s to CVE-2024-11392, CVE-2024-11393, and CVE-2024-11394 🎉
My goal was to get atleast one CVE by the end of the year and I’m happy to report I got 3!
Here’s to CVE-2024-11392, CVE-2024-11393, and CVE-2024-11394 🎉
They spammed the chat room with trans flag emojis and leaked 14 GB of data including all private chats.
youtu.be/j84gB2cbNps?...

They spammed the chat room with trans flag emojis and leaked 14 GB of data including all private chats.
youtu.be/j84gB2cbNps?...
1. Automatically installs Bing Visual Search.
2. Includes code to decrypt cookies saved in other browsers.
3. Brings a "free" geolocation web API to the system.
4. Tries to make Bing your default search engine (barf).
#news #worldnews

1. Automatically installs Bing Visual Search.
2. Includes code to decrypt cookies saved in other browsers.
3. Brings a "free" geolocation web API to the system.
4. Tries to make Bing your default search engine (barf).
I was super stocked but got a B+ because “it had no real world application.” and was recommended I focus on “making something productive.”
I now work on a red team and develop malware for assessments. 💀
I'm Claudia, and "she has potential but spends all of her time with that computer-thing. And bet she's no good at: each time something is broken!" was my tagline.
Lucky me, at that time police didn't know computer could "do" things 😶
I was super stocked but got a B+ because “it had no real world application.” and was recommended I focus on “making something productive.”
I now work on a red team and develop malware for assessments. 💀
I loved his book If It's Smart, It's Vulnerable, and the museum is definitely on my bucket list for when I visit Finland.
www.withsecure.com/en/experienc...

I loved his book If It's Smart, It's Vulnerable, and the museum is definitely on my bucket list for when I visit Finland.
www.withsecure.com/en/experienc...
Would love to hear some tips on improving your reports, calculating the CVSS score or just cool stories from the job!
Would love to hear some tips on improving your reports, calculating the CVSS score or just cool stories from the job!
It’s a competition focused on finding security bugs in EOL (End of Life) software and hardware.
Excited to see how it goes!

It’s a competition focused on finding security bugs in EOL (End of Life) software and hardware.
Excited to see how it goes!