
#ThreatIntel #Criminology #Cyberwarfare
www.team-cymru.com/post/how-vir...

www.team-cymru.com/post/how-vir...
bindinghook.com/articles-bin...

bindinghook.com/articles-bin...
#cyber #threatintel #malware

#cyber #threatintel #malware
#cyber #threatintel #falseflag #malware #turla #apt28 #lazarus #apt34 #counterintelligence #deception

#cyber #threatintel #falseflag #malware #turla #apt28 #lazarus #apt34 #counterintelligence #deception

#cyber #cryptocurrency #solana #malware #vulnerability #javascript

#cyber #cryptocurrency #solana #malware #vulnerability #javascript
#cyber #scam #genai

#cyber #scam #genai
Featuring @crep1x.bsky.social from @sekoia.io!
intel471.com/resources/po...

Featuring @crep1x.bsky.social from @sekoia.io!
intel471.com/resources/po...
github.com/BushidoUK/MI...
github.com/BushidoUK/MI...
#cyber #threatintel #malware #TransparentTribe

#cyber #threatintel #malware #TransparentTribe
#cyber #threatintel #malware

#cyber #threatintel #malware
@TeamCym

#cyber #threatintel #malware
@TeamCym

#cyber #threatintel #apt #UNC1549
#cyber #threatintel #apt #UNC1549
www.recordedfuture.com/research/rus...

www.recordedfuture.com/research/rus...
zerosecurity.org/microsoft-wa...

zerosecurity.org/microsoft-wa...
It helps to understand how #attackers performs their attacks and how #blueteam can respond against them.
I highly recommend SOC/CERT analysts to read this.
thedfirreport.com/2024/12/02/t...
#cybersecurity #detection #ioc

It helps to understand how #attackers performs their attacks and how #blueteam can respond against them.
I highly recommend SOC/CERT analysts to read this.
thedfirreport.com/2024/12/02/t...
#cybersecurity #detection #ioc
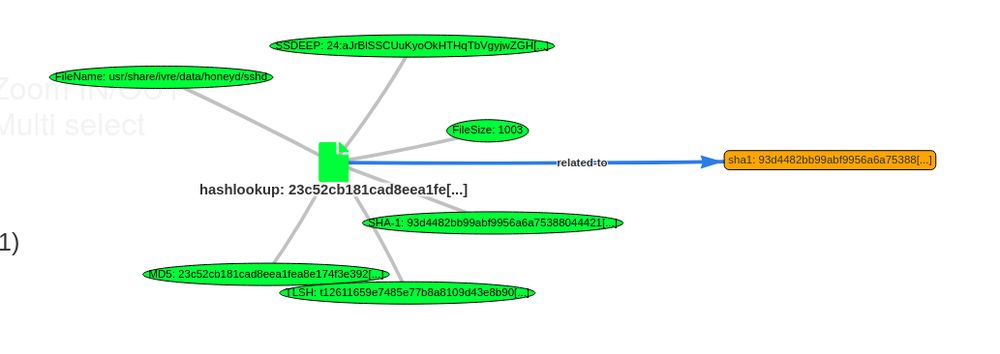


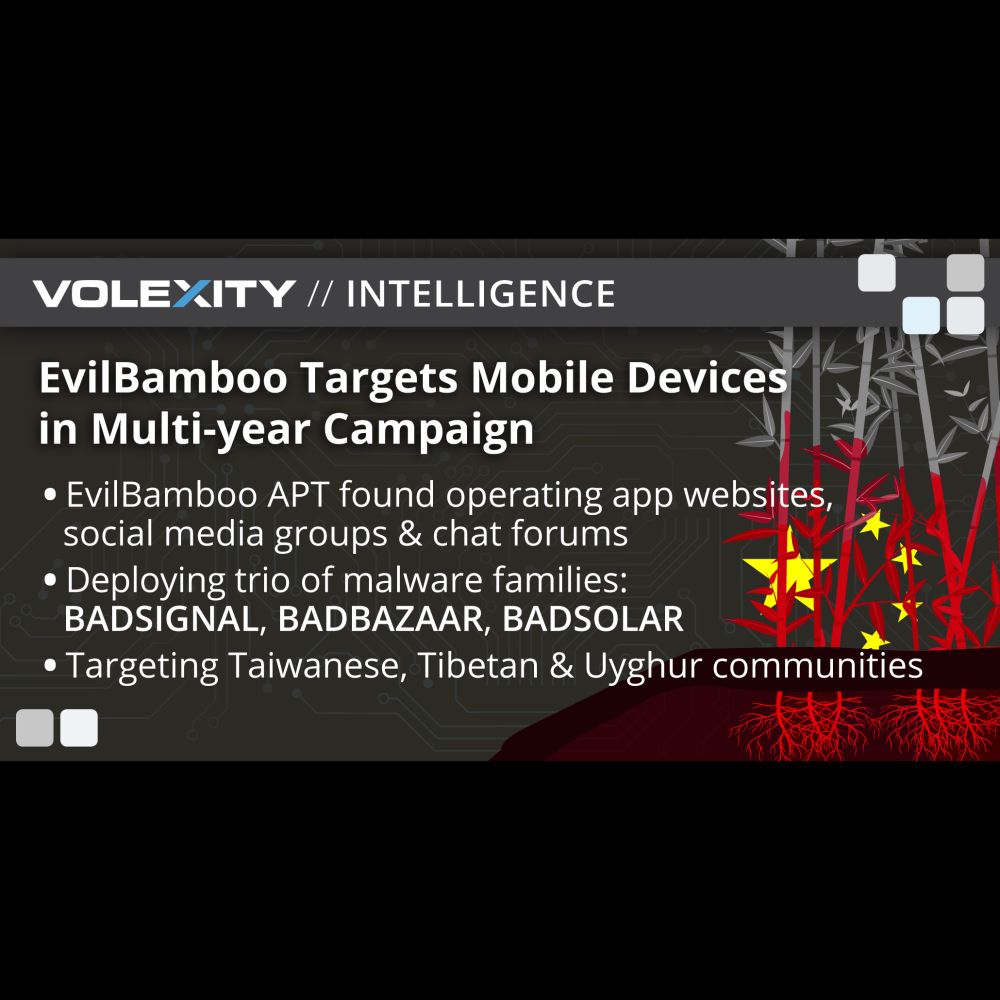

securelist.com/hrserv-apt-w...

securelist.com/hrserv-apt-w...

